国外DDoS产品的一些调研—— Akamai Arbor Networks Cloudflare DOSarrest F5 Fastly Imperva Link11 Neustar Nexusguard Oracle (Dyn) Radware Verisign
Global DDoS Threat Landscape
Q4 2017
https://www.incapsula.com/ddos-report/ddos-report-q4-2017.html,DDOS攻击的报告。
Market Guide for DDoS Mitigation Services
2018年的,from:https://www.gartner.com/doc/3873489/market-guide-ddos-mitigation-services
Summary
The DDoS market has been expanding since 2013, as many new providers have begun to offer DDoS mitigation services. Here, we outline the market segments and highlight differentiators to be considered by security and risk management leaders to select key vendors.
Table of Contents
- Market Definition
- Market Description
- Scrubbing Centers
- Content Delivery Networks
- CSPs and Hosting Providers
- IaaS
- Market Description
- Market Direction
- Market Analysis
- Scrubbing Center
- CDN
- CSPs and Hosters
- IaaS
- Representative Vendors
- Market Introduction
- Vendor Profiles
- Akamai
- Arbor Networks
- Cloudflare
- DOSarrest
- F5
- Fastly
- Imperva
- Link11
- Neustar
- Nexusguard
- Oracle (Dyn)
- Radware
- Verisign
- Market Recommendations
- Gartner Recommended Reading
某网站排名:from:https://www.itcentralstation.com/categories/ddos
一个产品目录,from:https://www.business.com/categories/best-ddos-protection-services/
List of 10 DDoS Protection Services

DOSarrest
http://www.dosarrest.com
DOSarrest's DDoS protection service can thwart application layer, volumetric and protocol attacks. To learn more, check out our review.

CloudFlare
https://www.cloudflare.com
CloudFlare Enterprise is a strong cloud-based DDoS protection service. See how it compares to other denial of service attack mitigation providers.

Neustar
https://www.neustar.biz
Neustar is designed to protect your business from volumetric, application and protocol DDoS attacks. Learn more about this DDoS protection service in our review.

Nexusguard
https://www.nexusguard.com
Nexusguard offers cloud-based mitigation services against DDoS attacks. To learn more, read our review.

Imperva Incapsula
http://www.incapsula.com
Imperva Incapsula offers always-on or on-demand DDoS protection for small to medium-size businesses. Read our full article to learn more.

Radware
http://www.radware.com
Radware's Attack Mitigation Service integrates on-premises detection with cloud-based technology. Compare it with other DDoS mitigation services in our review.

Verisign
http://www.verisigninc.com
Verisign DDoS Protection Service developed a unique mitigation platform, Athena, to mitigate complex DDoS attacks. Learn more about this service in our review.

Akamai
http://www.akamai.com
Akamai Kona Site Defender successfully mitigates denial-of-service attacks. To learn more, read our review.

F5 Networks
https://f5.com
F5's Silverline DDoS Protection uses a number of advanced mitigation techniques to protect you from attacks. Learn more in our review.

Arbor
http://www.arbornetworks.com
Arbor Networks offers cloud-based and on-premise DDoS solutions to safeguard your business from DDoS attacks. Learn more about this service in our review.
DDoS: A Comparison of Defense Approaches
注意:是2014年的结果,from:https://www.gartner.com/doc/2910217/ddos-comparison-defense-approaches
Summary
Distributed denial of service attacks have risen in complexity, bandwidth and number of occurrences targeting enterprises. Organizations must architect their defenses with both cloud and on-premises defenses along with integrating DDoS responses into the current incident response process.
Table of Contents
- Comparison
- Analysis
- Introduction
- Distributed Denial-of-Service Costs
- Unique Attributes of DDoS Attacks
- DDoS Attacks Today
- Brief Attack Taxonomy
- Commonly Seen DDoS Attack Types
- Application-Layer DDoS
- Attack Motivations
- DoS Defense
- DDoS Defense Triad: Resilience, Detection, Mitigation
- DDoS Resilience
- DDoS Detection
- DDoS Mitigation
- DoS Defense Architecture
- DoS Defense Layers and the Shared Nature of DDoS Defense
- Introduction
- Guidance
- Recommendations
- Scenario 1 — Large Enterprise With Mission-Critical Website
- Scenario 2 — Large Enterprise
- Scenario 3 — Enterprise
- Scenario 4 — SMB or Small Enterprise
- Scenario 5 — Cloud-Hosted Website
- Additional Recommendations
- Recommendations
- The Details
- Vendors by Layer Details
- A10 Networks
- Akamai/Prolexic
- Arbor Networks
- Check Point
- Corero Network Security
- F5 Networks
- Juniper Networks
- Neustar
- Radware
- RioRey
- Verisign
- Vendors by Layer Details
- Gartner Recommended Reading
Gartner Says 25 Percent of Distributed Denial of Services Attacks in 2013 Will Be Application-Based
from:https://www.gartner.com/newsroom/id/2344217
WAF 2017的,https://www.gartner.com/doc/reprints?id=1-496C4QP&ct=170807&st=sb

from:https://www.imperva.com/blog/2017/08/gartner-magic-quadrant-for-wafs-a-leader-four-consecutive-years/
Forcepoint recognized in Visionary quadrant in Gartner 2017 Magic Quadrant for Enterprise Network Firewalls
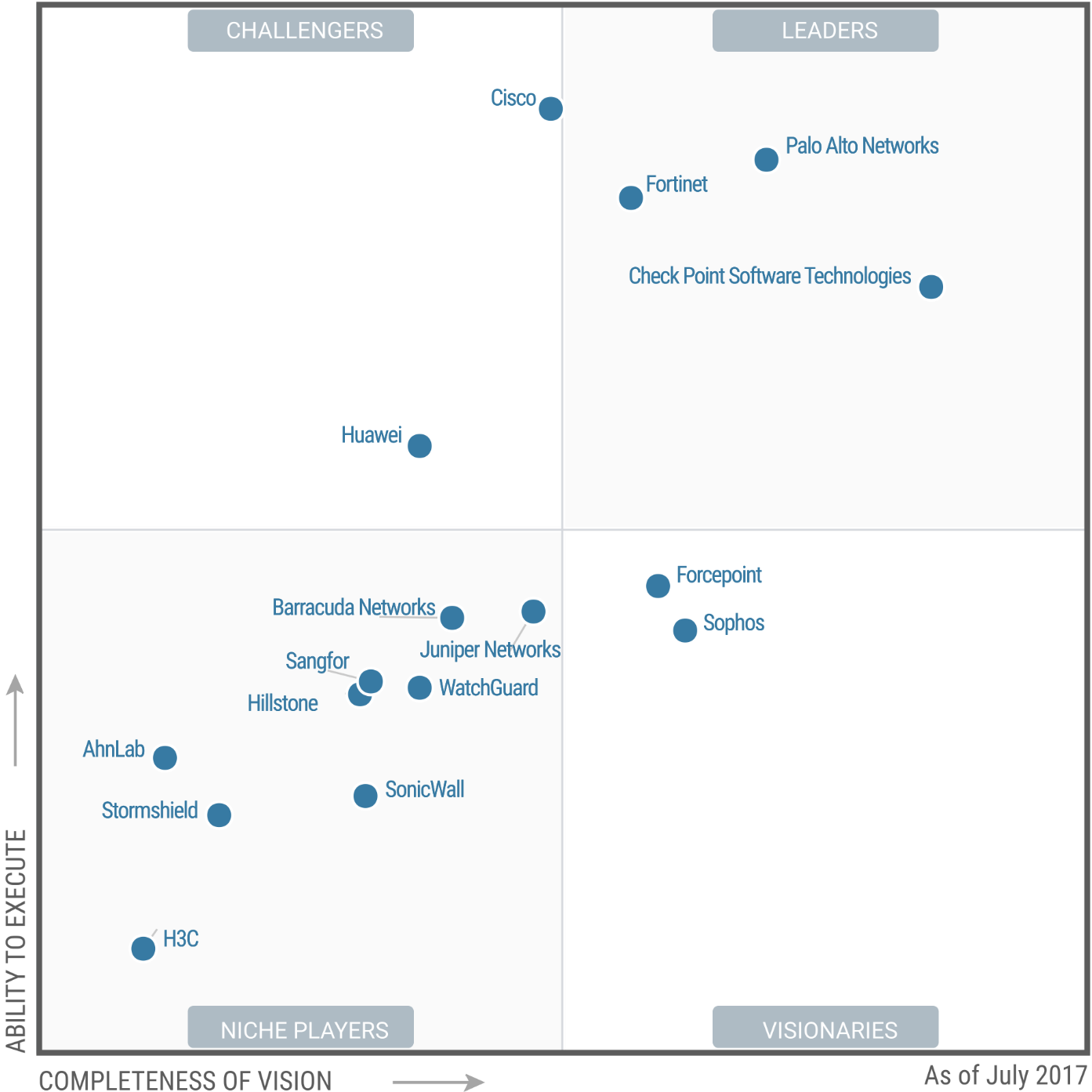
Forcepoint leaps from Niche Player in 2016 to highest for ability to execute in the Visionary quadrant in the 2017 Gartner Magic Quadrant for Enterprise Network Firewalls.
from:https://www.forcepoint.com/zh-hans/node/14171
最新文章
- Effective C++ -----条款22:将成员变量声明为private
- struct大小
- 如何彻底的卸载和删除Windows service
- unity jiaoben
- org.springframework.web.servlet.view
- The Arduino IDE(compiler)'s float bug
- 单例模式(Singleton)详解——转载
- Fibinary Numbers
- android service文章转载
- Git 删除文件
- 广告等第三方应用嵌入到web页面方案 之 使用js片段
- 抽象工厂模式(Abstract Factory Pattern)
- Elasticsearch学习笔记(八)Elasticsearch的乐观锁并发控制
- 初识JDBC
- Linux c 获取cpu使用率(2)
- TCP/IP学习20180710-数据链路层-ICMP协议
- Zookeeper在Linux平台Java开发环境配置(命令行)
- RocketMQ源码 — 五、 主要feature及其实现方式
- 前端 跨Area后Cookie无法访问
- 多进程和mongo的配合使用




