2019 SDN第三次上机作业
作业要求:
- 利用Mininet仿真平台构建给定的网络拓扑,配置主机h1和h2的IP地址(h1:10.0.0.1,h2:10.0.0.2),测试两台主机之间的网络连通性;
- 利用Wireshark工具,捕获拓扑中交换机与控制器之间的通信数据,对OpenFlow协议类型的各类报文(hello, features_request, features_reply, set_config, packet_in, packet_out等)进行分析,对照wireshark截图写出你的分析内容;
- 作业博客链接:https://edu.cnblogs.com/campus/fzu/fzusdn2019/homework/9968
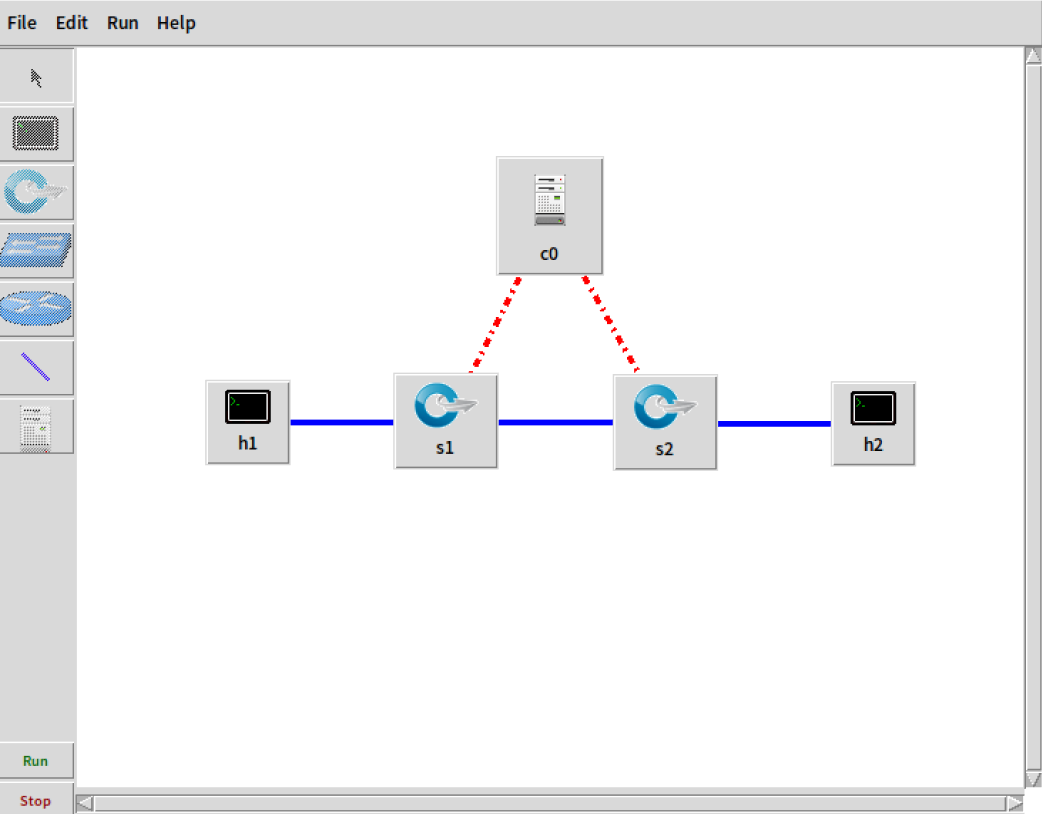
1. 利用Mininet仿真平台构建如下图所示的网络拓扑,配置主机h1和h2的IP地址(h1:10.0.0.1,h2:10.0.0.2),测试两台主机之间的网络连通性

具体操作步骤与截图说明:
- 打开终端启动wireshark工具,在wireshark中使用any捕获过滤器(避免实验过程中没有捕捉到拓扑网络建立过程中的某些报文)

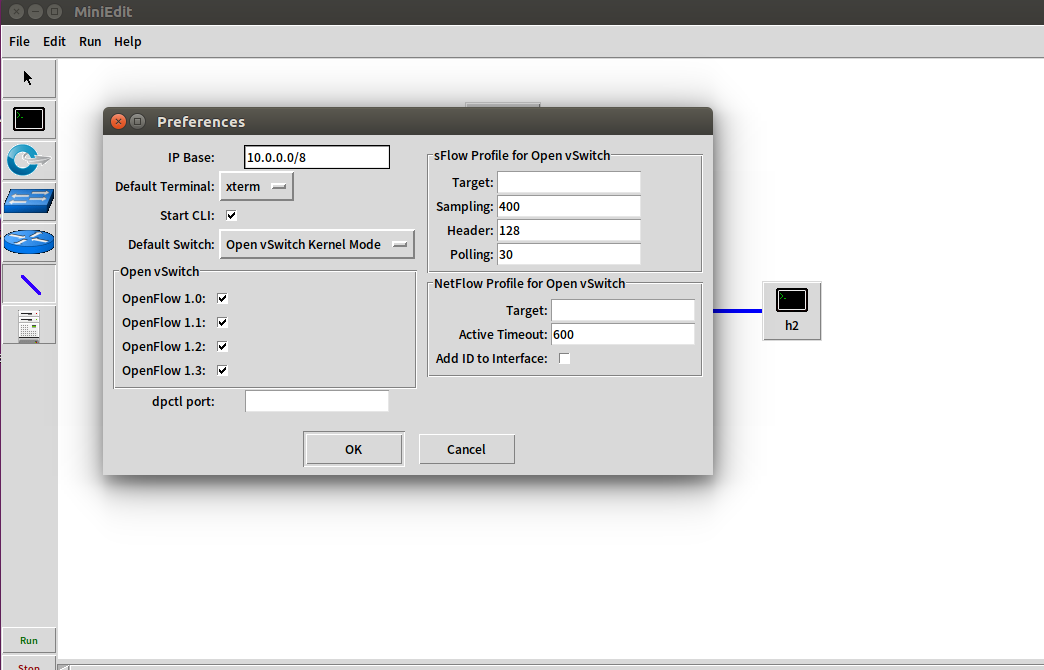
- 使用miniedit仿真工具创建拓扑,并设置主机h1的IP地址为10.0.0.1,设置主机h2的IP地址为10.0.0.2,勾选start CLI,并支持OpenFlow 1.0 1.1 1.2 1.3,Controller选择默认的openflow reference
2. 利用Wireshark工具,捕获拓扑中交换机与控制器之间的通信数据,对OpenFlow协议类型的各类报文(hello, features_request, features_reply, set_config, packet_in, packet_out等)进行分析,对照wireshark截图写出你的分析内容

报文分析
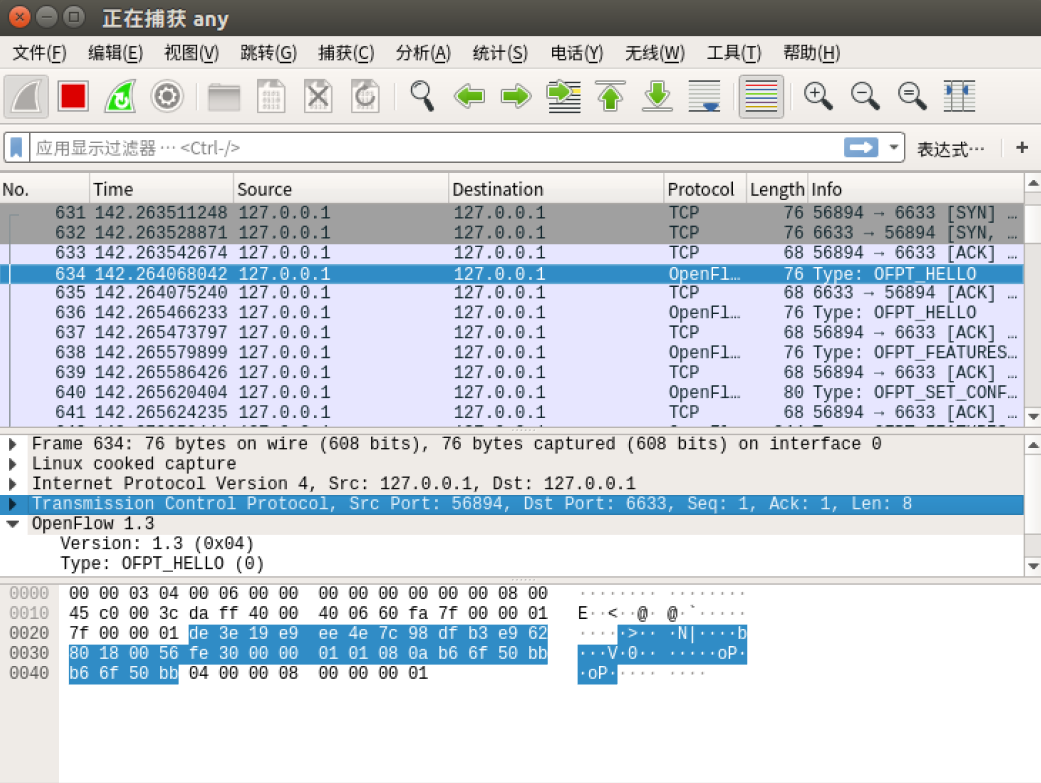
- hello
交换机56894端口 --> 控制器6633端口(最高支持OpenFlow 1.3协议)
控制器6633端口 --> 交换机56894端口(最高支持OpenFlow 1.0协议)
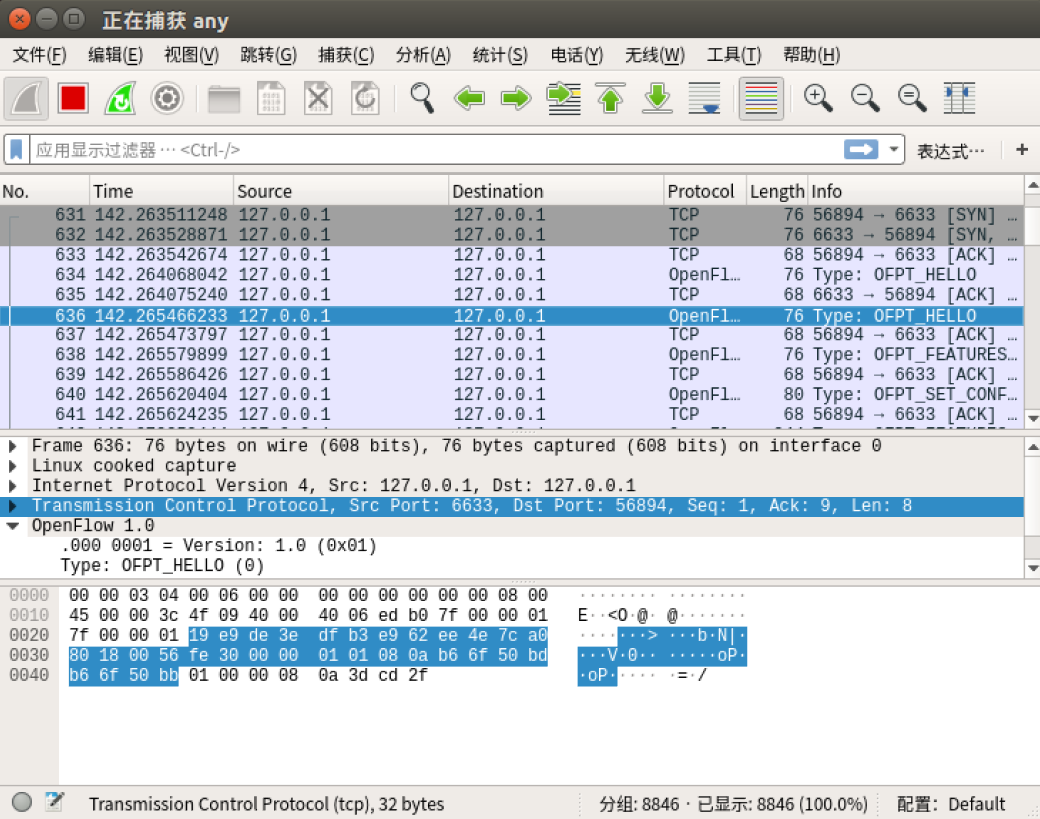
交换机与控制器并使用OpenFlow 1.0协议(向下兼容)
- Features Request
控制器6633端口(请求发送特征信息)-->交换机56894端口

- Set Config
控制器6633端口(按照控制器发送的flag和max bytes of packet进行配置)-->交换机56894
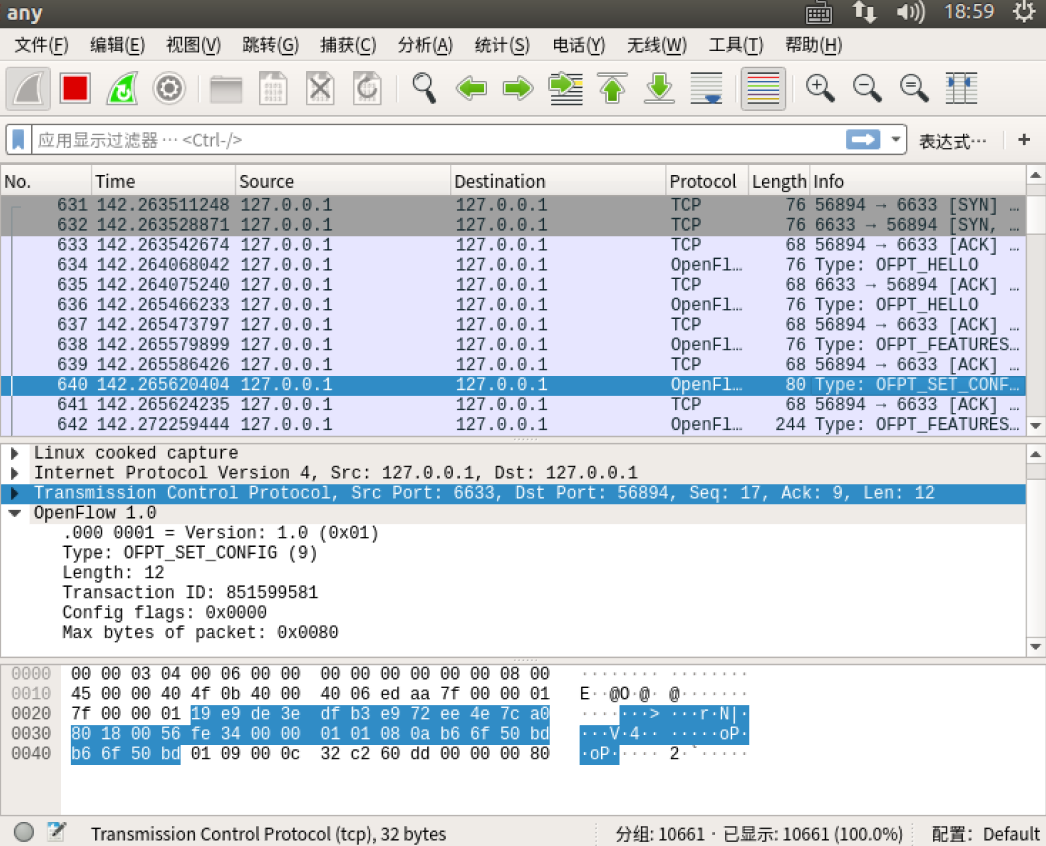
- Features Reply
交换机56894端口(回复特征信息)-->控制器6633端口
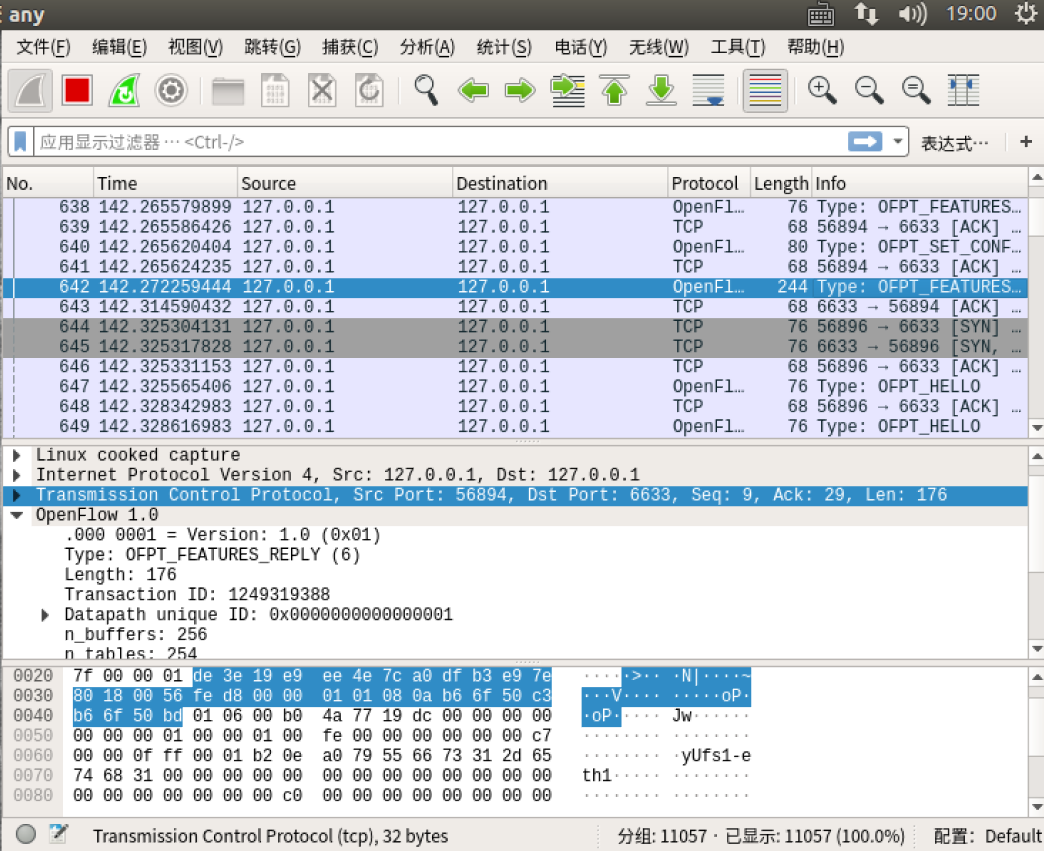
Features 消息包括 OpenFlow Header 和 Features Reply Message
对照Features Reply Message结构
struct ofp_switch_features{
struct ofp_header header;
uint64_t datapath_id; /*唯一标识 id 号*/
uint32_t n_buffers; /*交缓冲区可以缓存的最大数据包个数*/
uint8_t n_tables; /*流表数量*/
uint8_t pad[3]; /*align to 64 bits*/
uint32_t capabilities; /*支持的特殊功能,具体见 ofp_capabilities*/
uint32_t actions; /*支持的动作,具体见 ofp_actions_type*/
struct ofp_phy_port ports[0]; /*物理端口描述列表,具体见 ofp_phy_port*/
};
对应到抓取到的报文,逐项查看报文内容
OpenFlow 1.0
.000 0001 = Version: 1.0 (0x01)
Type: OFPT_FEATURES_REPLY (6)
Length: 176
Transaction ID: 1249319388
Datapath unique ID: 0x0000000000000001
MAC addr: 00:00:00_00:00:00 (00:00:00:00:00:00)
Implementers part: 0x0001
n_buffers: 256
n_tables: 254
Pad: 000000
capabilities: 0x000000c7
.... .... .... .... .... .... .... ...1 = Flow statistics: True
.... .... .... .... .... .... .... ..1. = Table statistics: True
.... .... .... .... .... .... .... .1.. = Port statistics: True
.... .... .... .... .... .... .... 0... = Group statistics: False
.... .... .... .... .... .... ..0. .... = Can reassemble IP fragments: False
.... .... .... .... .... .... .1.. .... = Queue statistics: True
.... .... .... .... .... ...0 .... .... = Switch will block looping ports: False
actions: 0x00000fff
.... .... .... .... .... .... .... ...1 = Output to switch port: True
.... .... .... .... .... .... .... ..1. = Set the 802.1q VLAN id: True
.... .... .... .... .... .... .... .1.. = Set the 802.1q priority: True
.... .... .... .... .... .... .... 1... = Strip the 802.1q header: True
.... .... .... .... .... .... ...1 .... = Ethernet source address: True
.... .... .... .... .... .... ..1. .... = Ethernet destination address: True
.... .... .... .... .... .... .1.. .... = IP source address: True
.... .... .... .... .... .... 1... .... = IP destination address: True
.... .... .... .... .... ...1 .... .... = IP ToS (DSCP field, 6 bits): True
.... .... .... .... .... ..1. .... .... = TCP/UDP source port: True
.... .... .... .... .... .1.. .... .... = TCP/UDP destination port: True
.... .... .... .... .... 1... .... .... = Output to queue: True
Port data 1
Port number: 1
HW Address: b2:0e:a0:79:55:66 (b2:0e:a0:79:55:66)
Port Name: s1-eth1
Config flags: 0x00000000
State flags: 0x00000000
Current features: 0x000000c0
Advertised features: 0x00000000
Features supported: 0x00000000
Features advertised by peer: 0x00000000
Port data 2
Port number: 65534
HW Address: 36:4c:9b:3e:44:46 (36:4c:9b:3e:44:46)
Port Name: s1
Config flags: 0x00000001
State flags: 0x00000001
Current features: 0x00000000
Advertised features: 0x00000000
Features supported: 0x00000000
Features advertised by peer: 0x00000000
Port data 3
Port number: 2
HW Address: 7e:ff:63:0f:59:51 (7e:ff:63:0f:59:51)
Port Name: s1-eth2
Config flags: 0x00000000
State flags: 0x00000000
Current features: 0x000000c0
Advertised features: 0x00000000
Features supported: 0x00000000
Features advertised by peer: 0x00000000
- Packet_in
交换机56894端口-->控制器6633端口
结合Packet_in的结构
struct ofp_packet_in
{
struct ofp_header header;
uint32_t buffer_id; /*Packet-in消息所携带的数据包在交换机缓存区中的ID*/
uint16_t total_len; /*data字段的长度*/
uint16_t in_port; /*数据包进入交换机时的端口号*/
uint8_t reason; /*发送Packet-in消息的原因,具体见 ofp_packet_in_reason*/
uint8_t pad;
uint8_t data[0]; /*携带的数据包*/
};
分析抓取的数据包,可以发现是因为交换机发现此时自己并没有匹配的流表(Reason: No matching flow (table-miss flow entry) (0)),所以要问控制器如何处理
OpenFlow 1.0
.000 0001 = Version: 1.0 (0x01)
Type: OFPT_PACKET_IN (10)
Length: 104
Transaction ID: 0
Buffer Id: 0x00000100
Total length: 86
In port: 1
Reason: No matching flow (table-miss flow entry) (0)
Pad: 00
Ethernet II, Src: 76:78:c7:38:d0:de (76:78:c7:38:d0:de), Dst: IPv6mcast_ff:38:d0:de (33:33:ff:38:d0:de)
Destination: IPv6mcast_ff:38:d0:de (33:33:ff:38:d0:de)
Source: 76:78:c7:38:d0:de (76:78:c7:38:d0:de)
Type: IPv6 (0x86dd)
Internet Protocol Version 6, Src: ::, Dst: ff02::1:ff38:d0de
0110 .... = Version: 6
.... 0000 0000 .... .... .... .... .... = Traffic Class: 0x00 (DSCP: CS0, ECN: Not-ECT)
.... 0000 00.. .... .... .... .... .... = Differentiated Services Codepoint: Default (0)
.... .... ..00 .... .... .... .... .... = Explicit Congestion Notification: Not ECN-Capable Transport (0)
.... .... .... 0000 0000 0000 0000 0000 = Flow Label: 0x00000
Payload Length: 32
Next Header: ICMPv6 (58)
Hop Limit: 255
Source: ::
Destination: ff02::1:ff38:d0de
Internet Control Message Protocol v6
Type: Neighbor Solicitation (135)
Code: 0
Checksum: 0xf163 [correct]
[Checksum Status: Good]
Reserved: 00000000
Target Address: fe80::7478:c7ff:fe38:d0de
ICMPv6 Option (Nonce)
Type: Nonce (14)
Length: 1 (8 bytes)
Nonce: 710398f79618
- Packet_out
控制器6633端口-->交换机56894端口
结合Packet_out的结构
struct ofp_packet_out
{
struct ofp_header header;
uint32_t buffer_id; /*交换机缓存区id,如果为-1则指定的为packet-out消息携带的data字段*/
uint16_t in_port; /*如果buffer_id为‐1,并且action列表中指定了Output=TABLE的动作,in_port将作为data段数据包的额外匹配信息进行流表查询*/
uint16_t actions_len; /*action列表的长度,可以用来区分actions和data段*/
struct ofp_action_header actions[0]; /*动作列表*/
uint8_t data[0]; /*数据缓存区,可以存储一个以太网帧,可选*/
}
告诉输出到交换机的65531端口
OpenFlow 1.0
.000 0001 = Version: 1.0 (0x01)
Type: OFPT_PACKET_OUT (13)
Length: 24
Transaction ID: 0
Buffer Id: 0x00000100
In port: 1
Actions length: 8
Actions type: Output to switch port (0)
Action length: 8
Output port: 65531
Max length: 0
h1 ping h2
- packet_in
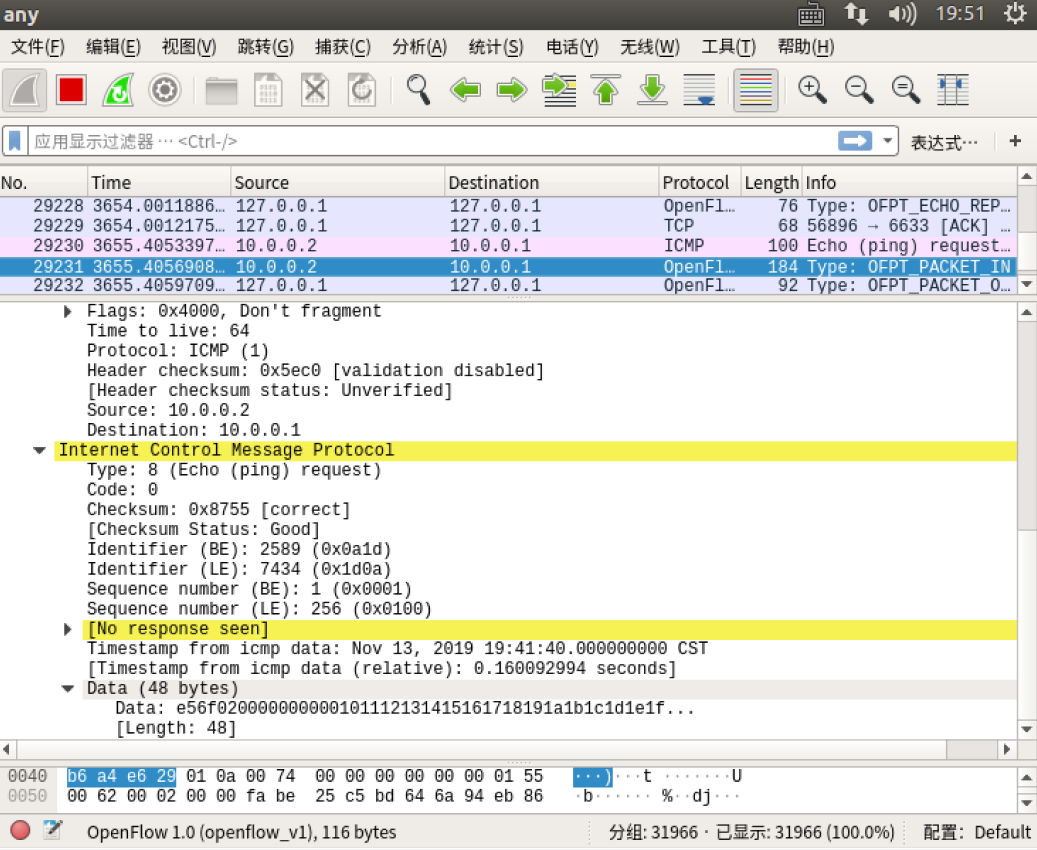
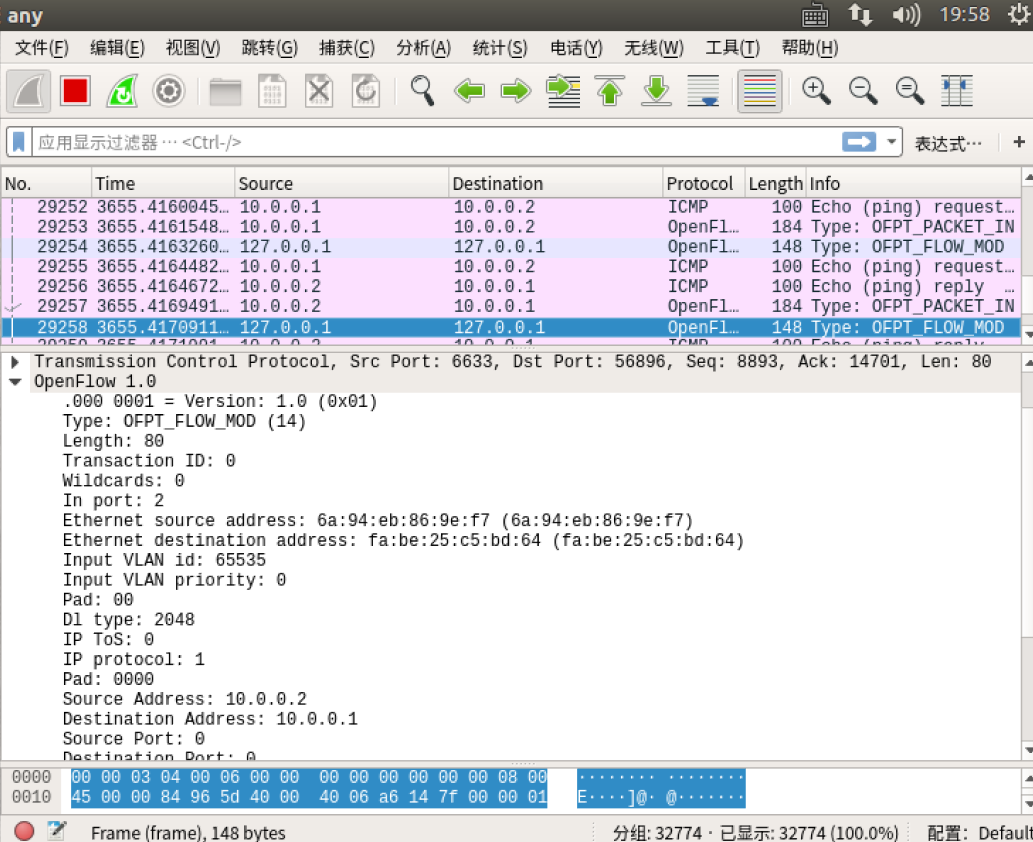
- flow_mod

结合flow_mod结构
struct ofp_flow_mod
{
struct ofp_header header;
struct ofp_match match; /*流表的匹配域*/
uint64_t cookie; /*流表项标识符*/
uint16_t command; /*可以是ADD,DELETE,DELETE-STRICT,MODIFY,MODIFY-STRICT*/
uint16_t idle_timeout; /*空闲超时时间*/
uint16_t hard_timeout; /*最大生存时间*/
uint16_t priority; /*优先级,优先级高的流表项优先匹配*/
uint32_t buffer_id; /*缓存区ID ,用于指定缓存区中的一个数据包按这个消息的action列表处理*/
uint16_t out_port; /*如果这条消息是用于删除流表则需要提供额外的匹配参数*/
uint16_t flags; /*标志位,可以用来指示流表删除后是否发送flow‐removed消息,添加流表时是否检查流表重复项,添加的流表项是否为应急流表项。*/
struct ofp_action_header actions[0]; /*action列表*/
};
分析抓取的flow_mod数据包,控制器通过6633端口向交换机56894端口、交换机56896端口下发流表项,指导数据的转发处理

把控制器从openflow reference改成ovs controller
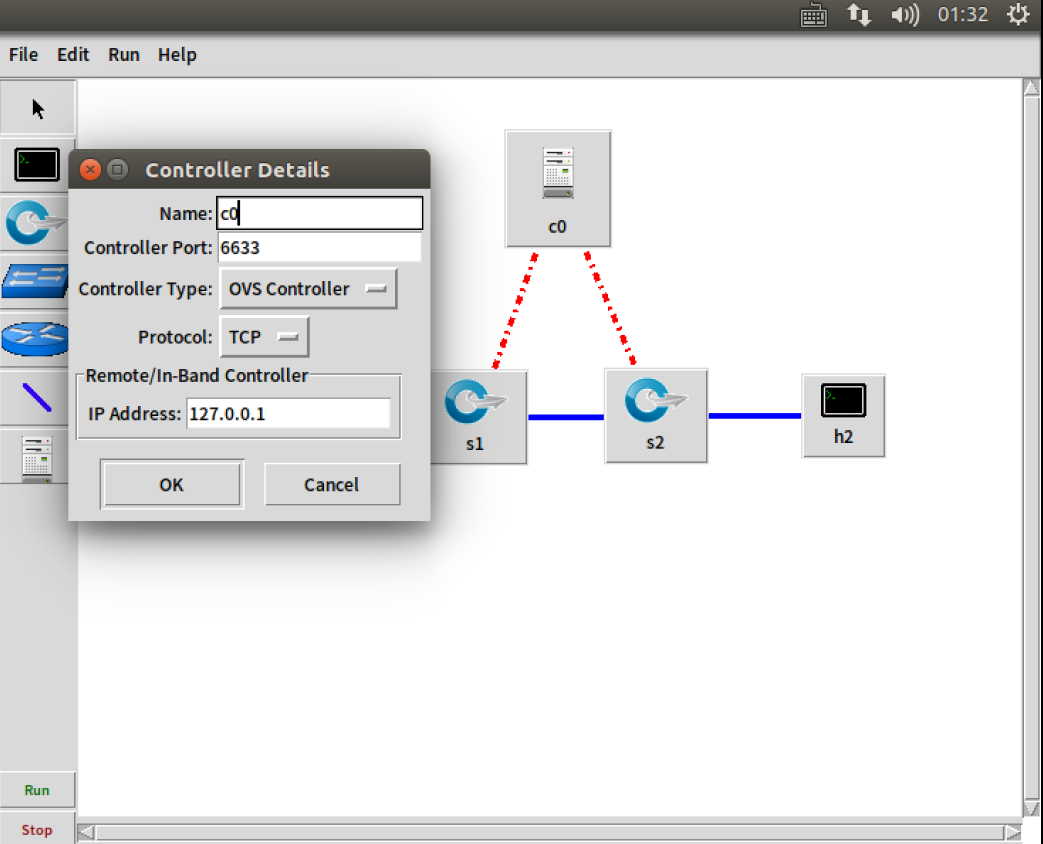
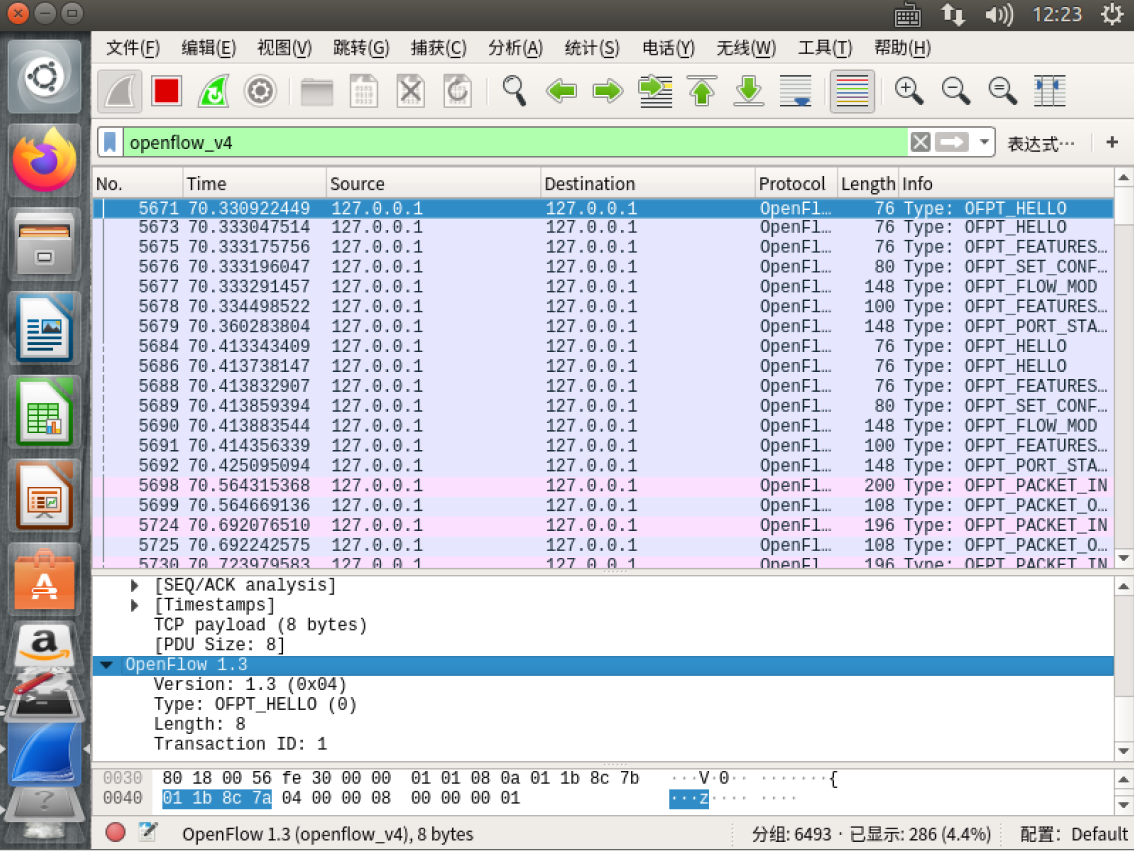
- hello
在hello报文中可以发现控制器支持的OpenFlow版本从1.0变成了1.3,因此,经过协商交换机和控制器之间将通过1.3版本的OpenFlow协议进行通信
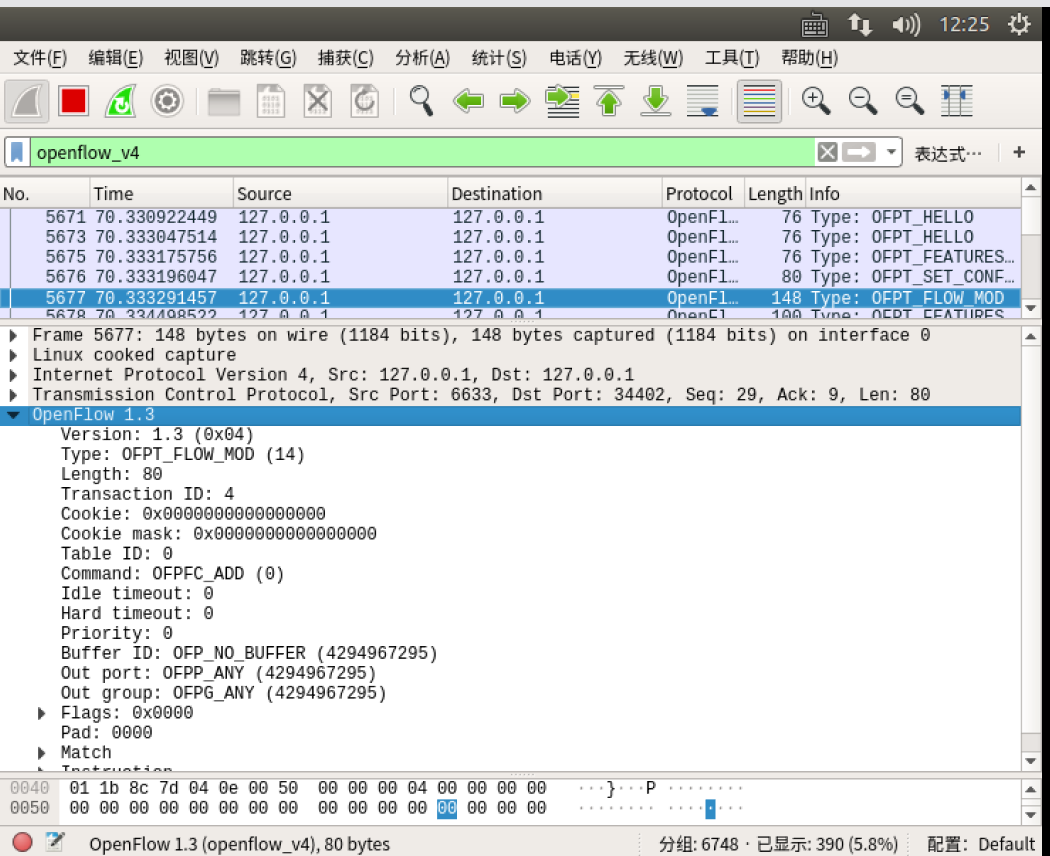
- flow_mod
双方协商使用OpenFlow 1.3进行通信
3.实验总结:
通过这次实验,进一步熟悉了wireshark这一抓包工具的使用,捕获OpenFlow协议中的各类报文(hello,features_request,features_reply,set_config, packet_in, packet_out等等)。对在openflow协议下交换机和控制器的工作原理有了一定的了解。
最新文章
- JAVA 取得当前目录的路径/Servlet/class/文件路径/web路径/url地址
- [蓝牙] 5、Battery Service module
- POJ 1068 Parencodings 模拟 难度:0
- 3.VS2010C++相关文件说明
- 利用 Composer 一步一步构建自己的 PHP 框架(三)——设计 MVC
- C++封装常用对象和对头文件探索
- UVA1152 4Values whose Sum is 0
- java全组合算法
- 基于synchronized实现的阻塞队列
- 数据标记系列——图像分割 & PolygonRNN++(一)
- Tools:实现ping操作带时间戳【windows+linux】
- 【转帖】Systemd 入门教程:命令篇
- Referrer Policy 介绍
- MySQL、Mariadb 复制原理
- C#编程(十四)----------构造函数
- IDEA 禁止自动导入引用包 取消import包
- composer概念学习
- javascript时间日期操作
- JavaScript数据结构-16.二叉树计数
- 总结:Python学习 和 Python与C/C++交互