[Angular] Protect The Session Id with https and http only
For the whole signup process. we need to
- Hash the password to create a password digest
- Store the user's info and password digest into db
- Create a random sessionId to assoc with user
- Set Session Id into cookie
async function createUserAndSession(res, credentials) {
// Create a password digest
const passwordDigest = await argon2.hash(credentials.password);
// Save into db
const user = db.createUser(credentials.email, passwordDigest);
// create random session id
const sessionId = await randomBytes(32).then(bytes => bytes.toString('hex'));
// link sessionId with user
sessionStore.createSession(sessionId, user);
// set sessionid into cookie
res.cookie('SESSIONID', sessionId);
// send back to UI
res.status(200).json({id: user.id, email: user.email});
}
-----
const util = require('util');
const crypto = require('crypto');
// convert a callback based code to promise based
export const randomBytes = util.promisify(
crypto.randomBytes
);
-----
import {Session} from './session';
import {User} from '../src/app/model/user';
class SessionStore {
private sessions: {[key: string]: Session} = {};
createSession(sessionId: string, user: User) {
this.sessions[sessionId] = new Session(sessionId, user);
}
}
// We want only global singleton
export const sessionStore = new SessionStore();
Now we have set the cookie, later, each request we send to the server, this cookie will be attached in the request header, we can confirm that:
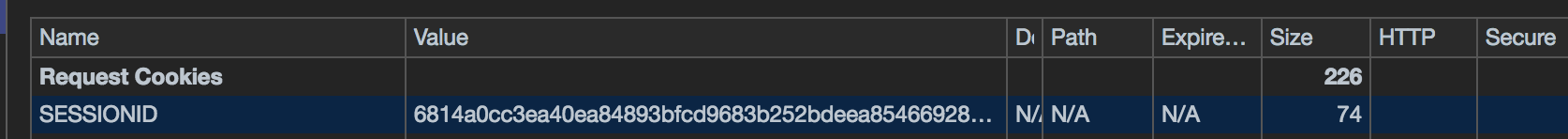
But the problem is that, hacker can inject some script to get our cookie by using:
document.cookie
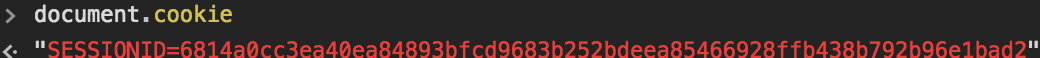
It enables the hacker to attack our site by just set cookie in his broswer, then in each reqest, the cookie will be sent to server, cookie is the only thing which server used to verfiy the user.
document.cookie = "......"
To protect that, we can make cookie can only be accessed by http, not JS:
// set sessionid into cookie
res.cookie('SESSIONID', sessionId, {
httpOnly: true, // js cannot access cookie
});

We can see that "HTTP" column was marked.
Second, we need to enable https protect.
To do that in server:
// set sessionid into cookie
res.cookie('SESSIONID', sessionId, {
httpOnly: true, // js cannot access cookie
secure: true // enable https only
});
We also need to adjust angular cli so that app run on https:
package.json:
"start": "ng serve --proxy-config ./proxy.json --ssl 1 --ssl-key key.pem --ssl-cert cert.pem",
// proxy.json
{
"/api": {
"target": "https://localhost:9000",
"secure": true
}
}

We can see that "Secure" column now is also marked.
最新文章
- 微信小程序-页面链接
- vim学习
- 夺命雷公狗-----React---2--组建
- HTML5 UI框架Kendo UI Web中如何创建自定义组件(二)
- BigDecimal在实际项目的应用及遇到的问题
- IIS启动出错解决方法
- 关于Apache Struts 2 S2-032高危漏洞的一些确认
- C#对word、excel、pdf等格式文件的操作总结
- 初涉JavaScript模式 (7) : 原型模式 【三】
- java项目(java project)如何导入jar包的解决方案列表
- 【转】Visual Studio Code 使用Git进行版本控制
- ps命令手册
- zookeeper使用和原理探究
- 【转】Android开发笔记(序)写在前面的目录
- mysql 日志类型
- vue 单独页面body css 样式设置
- 使用别名访问MSSQL Express
- 利用linux的mtrace命令定位内存泄露(Memory Leak)
- springmvc与ajax交互常见问题
- (KMP)Oulipo -- poj --3461