Downgrade extraction on phones running Android 7/8/9
Now it's more and more difficult for forensic tools to extract evidence from smartphone running Android 7 and above. Maybe you could acquire physical image in Bootloader mode or by Smart ADB. Don't celebrate too early. Let me remind you of "FDE". The fact is that if forensic tools could not decode this physical image, such image is just like a meaningless "black box" you have in hand.
No way to gain root privileges from phones running Android 7 and above . What else can be done? Fortunately once you got the pattern/password , you could enable USB debugging and change any settings you want to make "Downgrade extraction" possible. That's the key to get the evidence from certain Apps you want.
Let's take WeChat on a phone running Android Pie for example.

First we hava to download an old version apk file of WeChat. Then we want to uninstall original version of WeChat on this phone without data loss. The most important thing is remember the parameter "-k" when uninstall WeChat . So we could keep all data of WeChat safe and sound.
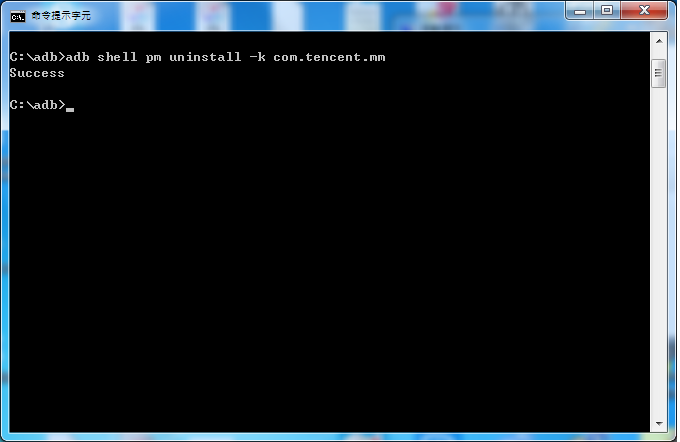
What the next? Install old version WeChat apk? No, it won't work unless you reboot this phone first.
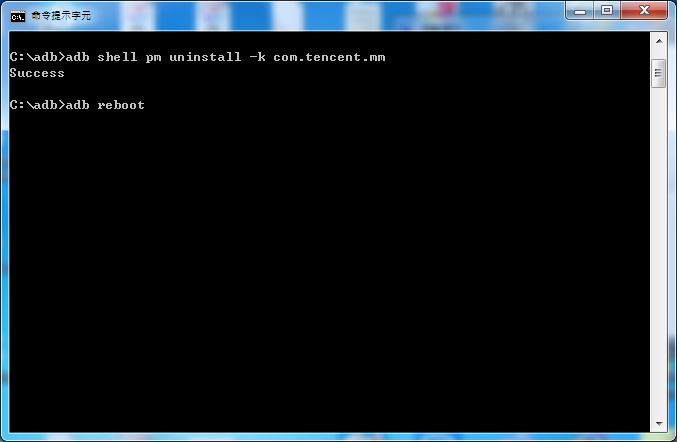
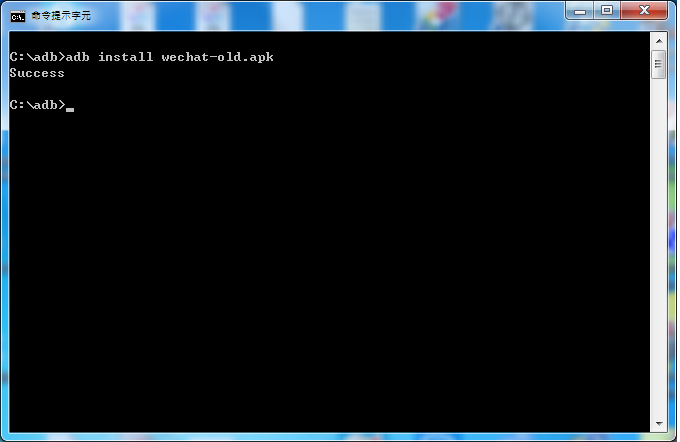
After rebooting we could use adb command to install older version WeChat apk. What kind of older version of WeChat apk you need? Of course the version enable adb backup permission. What? you are not sure? All you have to do is to take a look at its manifest.xml and you could see the allowBackup permission. Let's install and the result is "success". Is it surprise you? Keep in mind that do not click WeChat now!
Now we could use adb backup to extract WeChat. The output file is a .ab file. You have to convert this .ab to a .tar file.
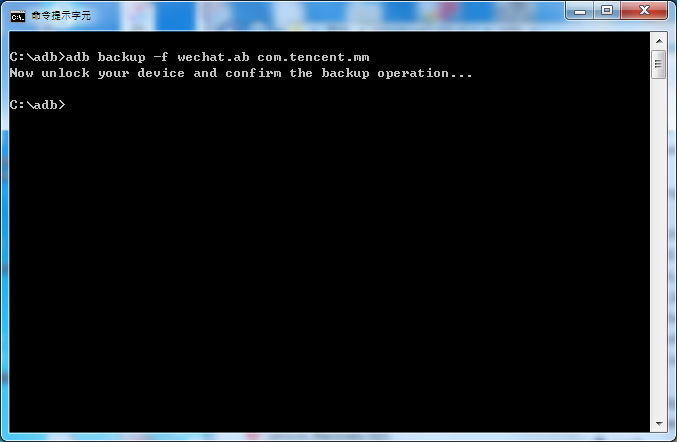
How to deal with a .ab file? You could take advantage of android backup extractor jar file to unpack .ab file.
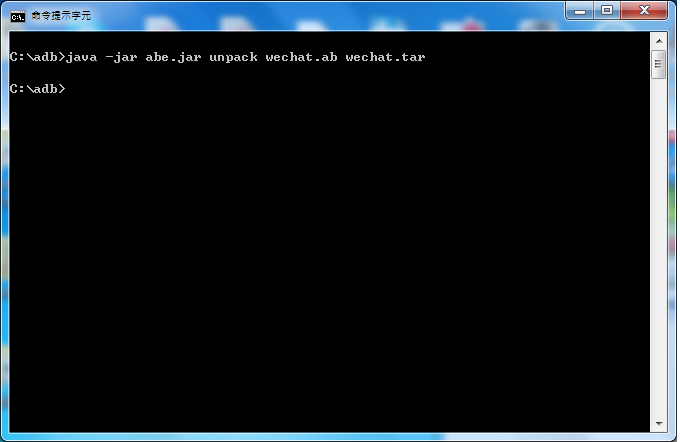
Unzip this .tar file and make sure you got the database file containing chat history. Yes, that's it. Don't forget that EnMicroMsg.db is an encrypted file. All you have to do is to look at my earlier post and you will know what to do.
最新文章
- mybatis : trim标签, “等于==”经验, CDATA标签 ,模糊查询CONCAT,LIKE
- String类和StringBuffer类的区别
- ABAP modify screen:修改屏幕,实现隐藏、禁止输入字段
- hdu 4617 Weapon
- PHP算法之二分查找和顺序查找
- 重置mysql管理员密码
- rac 10g 加入节点具体解释
- [Mugeda HTML5技术教程之7]添加动画
- IHttpModule与IHttpHandler的区别整理
- 使用pabot并发执行robotframework的testSuite
- du和df显示磁盘空间使用差异大的几种情况
- [Codeforces]871D Paths
- 手把手教你轻松实现listview上拉加载
- bzoj2839 集合计数(容斥)
- Spark基础-scala学习(五、集合)
- Ehcache缓存配置以及基本使用
- slf4j日志使用
- MySQL的启动和关闭
- DPHARD
- AIDL原理之 Framewok层实现