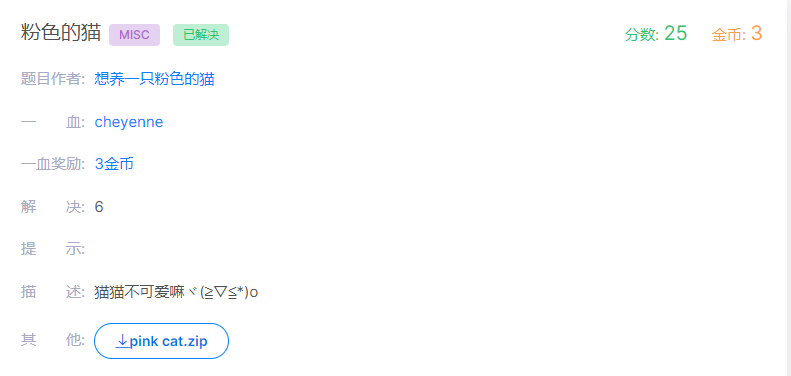
粉色的猫MISC(bugku)
一 题目描述
ps:本题特别感谢树叶大佬给的一些提示以及WP!欢迎大家关注树木有点绿~~
二 解题过程
下载附件得到zip压缩包
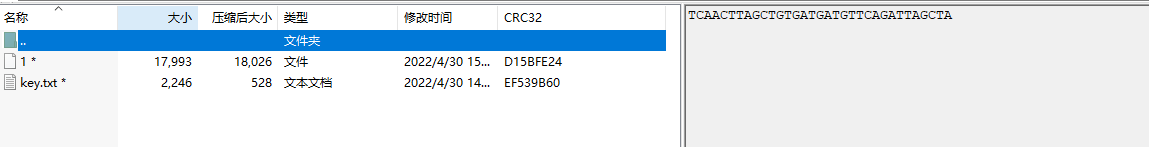
根据作者提示,压缩包注释应该为压缩包密码。
1.压缩包密码
一开始看到这个就想到应该是什么DNA相关解密,但未搜索到相关解码(搜索关键字真的很重要呜呜呜~),后来在GitHub等搜索到两个解码脚本,本质就是一组碱基对会对应一个字母。
但杯具的是解出来的一直不对!好了,直接上真正的解密方法:在线解密网址 https://earthsciweb.org/js/bio/dna-writer/
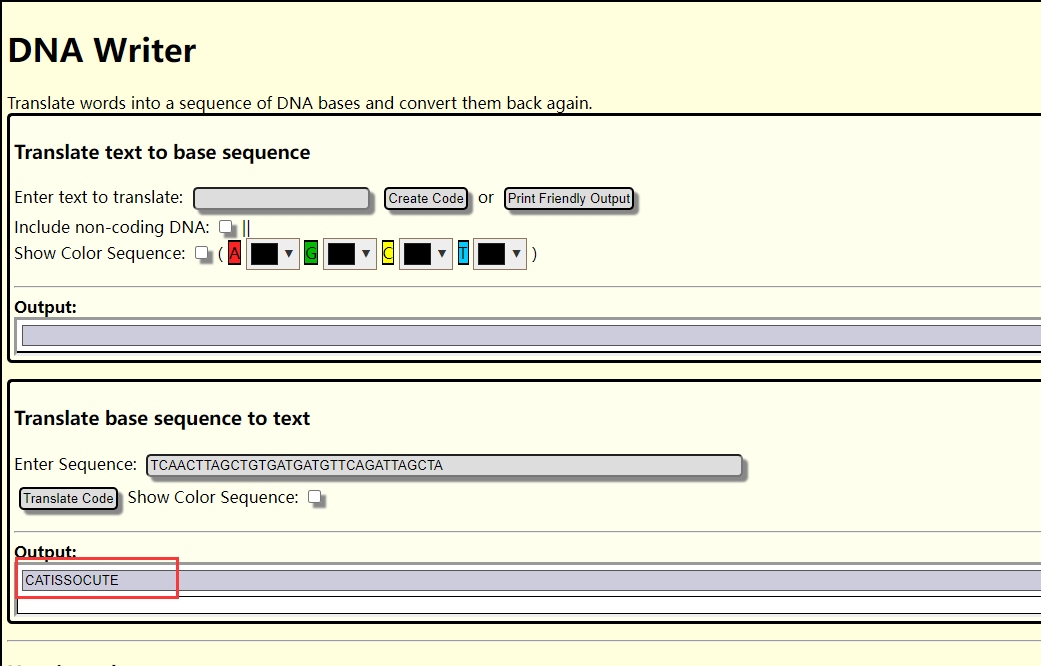
password
CATISSOCUTE
2.分析文件
(1)文件1
使用file命令或者在winhex等十六进制文本编辑器中可以发现是 BPG格式
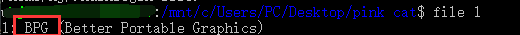
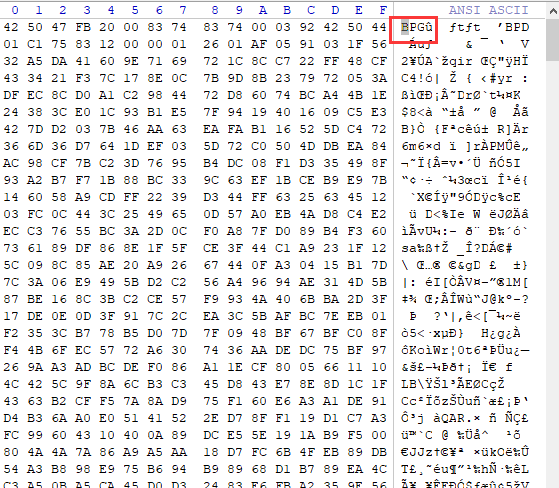
修改后缀得到一个1.bpg
下载BPGView查看
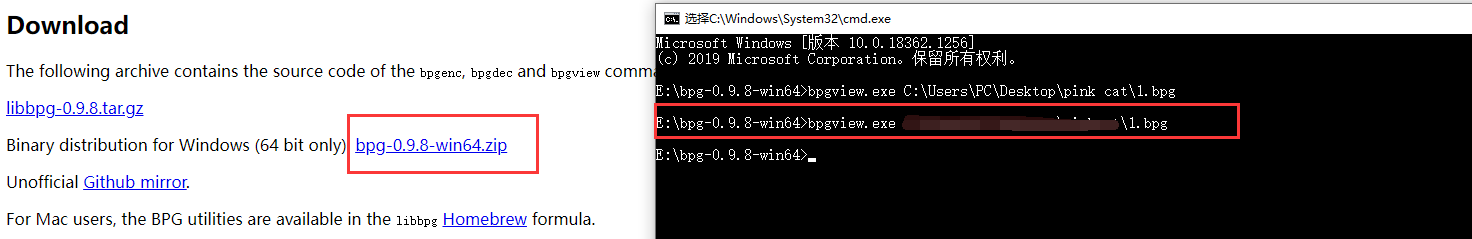
一脸茫然~~~
经过大佬指点是 猫脸变换
简单了解后我们解密该图片是需要知道变换的一个系数a b,于是查看key.txt文件
(2)key.txt
0001000D91683106019196F4000872003800390035003000340045003400370030004400300041003100410030004100300030003000300030003000300044003400390034003800340034003500320030003000300030003000300034003700300030003000300030003000300038003000380030003200300030003000300030
0001000D91683106019196F4000872003000320034004400430037003500460031003000300030003000300030004200430034003900340034003400310035003400370038003500450044004400390032003400310031003200380035003300300030003800340033004200390031003900460037003300460031003500390046
0001000D91683106019196F400087000380034004600410038003700310032003100370036004500370034003500310032003600450033004400340041003600320044003700390035003500420033003800380032003100310037003900390042004200320045004100420039003500410036004200330042004200450037
0001000D91683106019196F400086E0042003600300039003900330045004500360033004600320036004600440044003100420043004400410042003300300033003300310046004500350045003600440039003300370035004200300036003500360036004100320031003000410033004100420037003100440038
0001000D91683106019196F400087000450033004400370032003100300031004400420034003900310036003900360038003000310033003200340046003800450046003200380034004500420033003500430030004600420036003400450046003100300030004100310042004100300043003200300044004400450042
0001000D91683106019196F400086E0038003400410032004200440038004200350038004200330039004500410043003600450030004100420031003000380044003600440036004600340034004300460044003800310044003000330042003600390034004200430039003400430032003300310033004400340046
0001000D91683106019196F400087000360038003900390031003600440036003200360041003700390035003800460035004300440039003500390042004500320038004300340034003300410045003700360043003100300035003800380030003200380035003900320039003600310042004600430044003400300044
0001000D91683106019196F4000872003100350037004600310033003400310033003800390043004600410042003600410045003500460032003300300038003700370035004500380031004500420032003000330030004300300035003000340037003500310044003900460041003400450045004600320032004600440030
0001000D91683106019196F400085200300037004400450044003500420036003800410033003100350046004400310031003000300030003000300030003000300034003900340035003400450034003400410045003400320036003000380032
第一眼看到又是???,人麻了。后来也是无意中将这些16进制转为字符发现了隐藏的信息
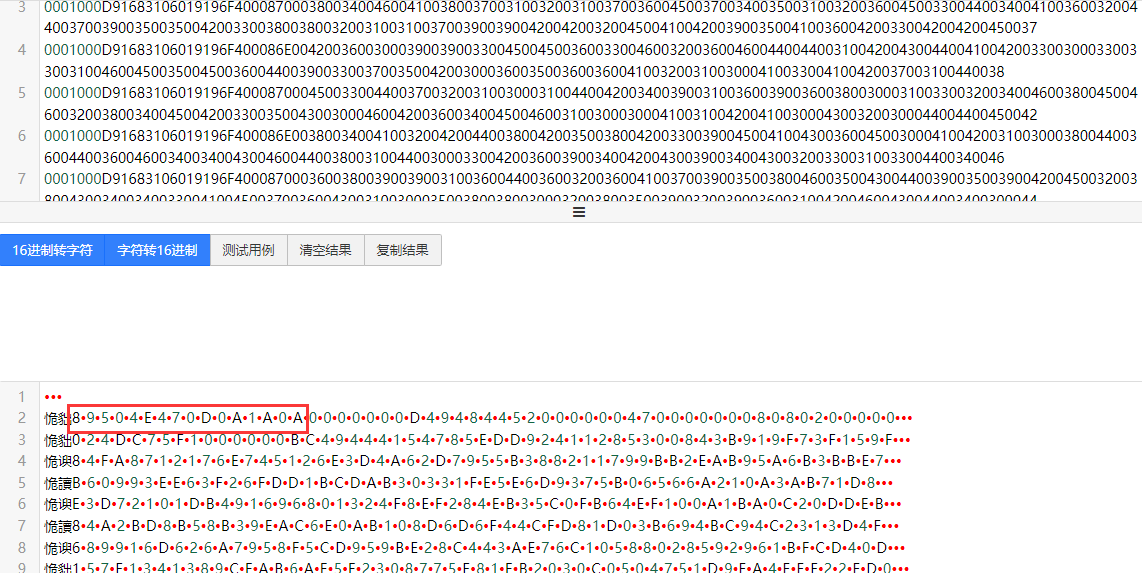
熟悉的文件头,于是将这些16进制拼接起来为一个新的png文件
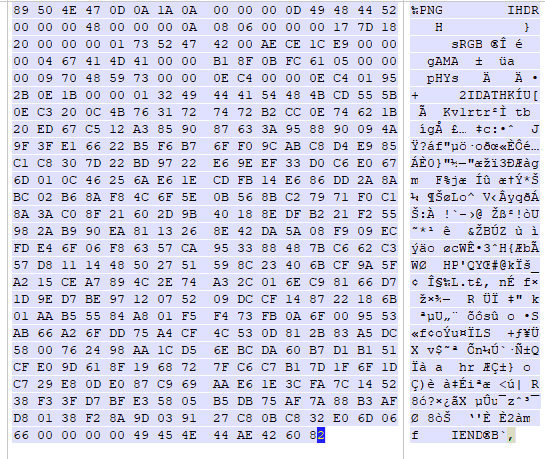

又是一脸???
这里说明一下,看 了大佬的wp后发现这段16进制其实是 PDU编码!!一段一段放进去解密就行。
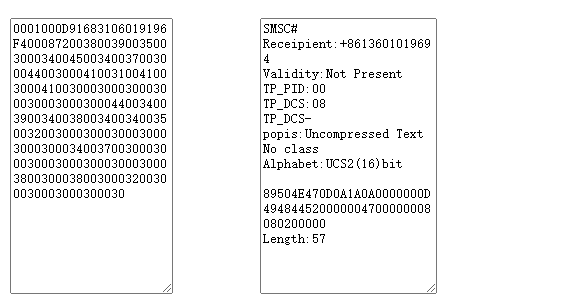
在线解密网站PDU解密
(3)png图片
看到这模糊的像素画,自己也是折腾很久没想到怎么解,即使自己后来有看过一题类似的像素解法也没想起来!!npiet
我就直接给大家一个在线的网站去解了
具体原理大家就自行百度哈

amazing!!
(4)show time!
网上找到的一个加解密代码。
import numpy as np
import cv2 def arnold_encode(image, a, b):
# 1:创建新图像
arnold_image = np.zeros(shape=image.shape) # 返回给定形状和类型的新数组,用0填充。img.shape返回img的长宽信息 # 2:计算N
h, w = image.shape[0], image.shape[1] # image.shape[0],image.shape[1],image.shape[2]表示图像长,宽,通道数
N = w # 或N=w # 3:遍历像素坐标变换
for x in range(h):
for y in range(w):
# 按照公式坐标变换
new_x = (1 * x + a * y) % N # 解密:上下对换,a变b,x变y,+变-
new_y = (b * x + (a * b + 1) * y) % N
# new_x = ( x + y) % N #狭义
# new_y = ( x + 2 * y) % N
arnold_image[new_x, new_y, :] = image[x, y, :] arnold_image = np.uint8(arnold_image) return arnold_image def dearnold_encode(image, a, b):
# 1:创建新图像
arnold_image = np.zeros(shape=image.shape) # 返回给定形状和类型的新数组,用0填充。img.shape返回img的长宽信息 # 2:计算N
h, w = image.shape[0], image.shape[1] # image.shape[0],image.shape[1],image.shape[2]表示图像长,宽,通道数
N = w # 或N=w # 3:遍历像素坐标变换
for x in range(h):
for y in range(w):
# 按照公式坐标变换
new_x = ((a * b + 1) * x - b * y) % N
new_y = (-a * x + y) % N
# new_x = (2* x - y) % N # 解密:上下对换,a变b,x变y,+变-
# new_y = ((-1) * x + y) % N
arnold_image[new_x, new_y, :] = image[x, y, :] arnold_image = np.uint8(arnold_image) return arnold_image r = cv2.imread(r'C:\Users\PC\Desktop\cat\out.png')#原始的1.bpg转换得到的文件路径
print(r) # 遍历次数
r = dearnold_encode(r, 13,14)
# r = dearnold_encode(r, 1, 1)
cv2.imshow("arnold", r)
cv2.waitKey(0)
cv2.destroyAllWindows()
这里的代码要先把bpg的图片转化为函数支持的图片格式
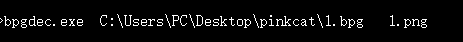
会在软件所在根目录下得到 out,png
然后 Run

Congratulations!
flag{c159549a-5604-4bb7-8a6e-9db9d8b1426a}
ps:曲折的解题过程,太多东西值得学习了,向大佬学习!欢迎大家交流~~
最新文章
- 怎么在myeclipse中导入已经写好的项目
- 39 网络相关函数(七)——live555源码阅读(四)网络
- Android常见控件— — —Button
- javascript笔记5-BOM
- ASP.NET地址栏form提交安全验证
- 【BZOJ】【3052】【WC2013】糖果公园
- Yii Active Record 查询结果转化成数组
- Java 操作 EXCEL
- poj2352 Stars
- UltraEdit中java代码换行问题
- IOS开发-UI学习-delegate(代理)的使用,键盘消失
- Java中httpClient中三种超时设置
- MVP架构在xamarin android中的简单使用
- may be a diary?
- JAVA判断是否是手机设备访问
- connected standby
- MY Views on Doctor-patient relationship 英语医患关系议论文
- 配置CenOS网络,并用Xshell链接。
- linux下逻辑卷管理 调整分区大小
- python 解析top文件格式