Python Ethical Hacking - VULNERABILITY SCANNER(7)
2024-10-09 10:04:32
VULNERABILITY_SCANNER
How to discover a vulnerability in a web application?
1. Go into every possible page.
2. Look for ways to send data to the web application(URL + Forms).
3. Send payloads to discover vulnerabilities.
4. Analyze the response to check of the website is vulnerable.
->General steps are the same regardless of the vulnerability.
Login the metasploitable VM and modify the security of DVWA from high to medium.(dvwaPage.inc.php in /var/www/dvwa/dvwa/includes)

Submit the following script on the Reflected Cross Site Scripting(XSS)
<sCript>alert('test')</scriPt>
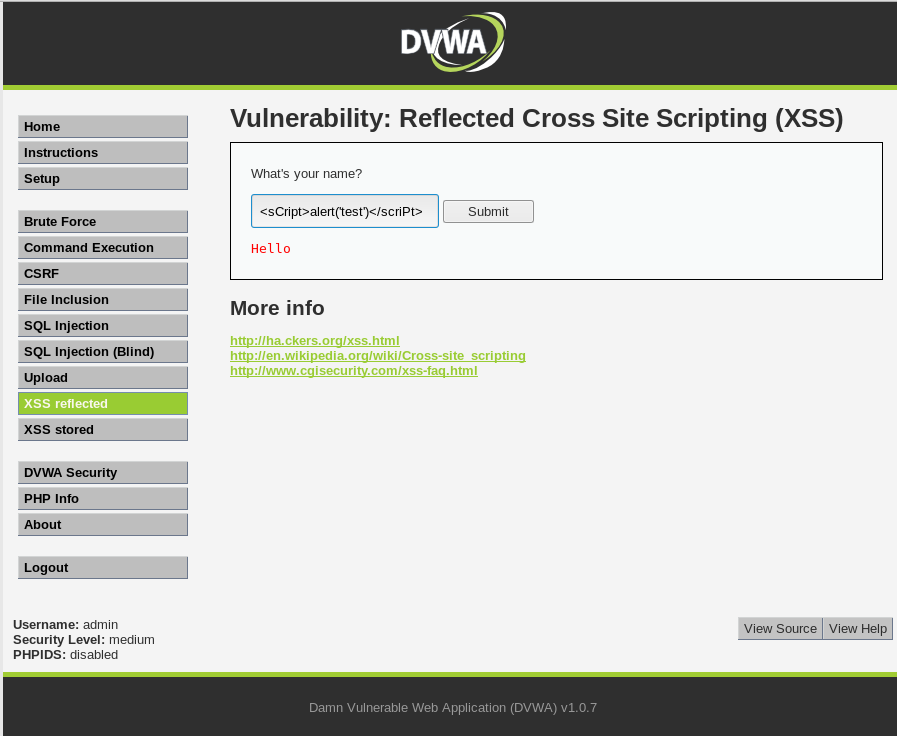
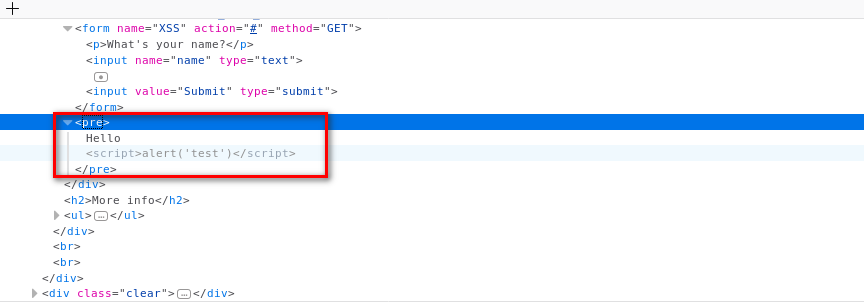
You can find the script in the source code.
Add the new feature - test_xss_in_form in Scanner class.
#!/usr/bin/env python import requests
import re
from bs4 import BeautifulSoup
from urllib.parse import urljoin class Scanner:
def __init__(self, url, ignore_links):
self.session = requests.Session()
self.target_url = url
self.target_links = []
self.links_to_ignore = ignore_links def extract_links_from(self, url):
response = self.session.get(url)
return re.findall('(?:href=")(.*?)"', response.content.decode(errors='ignore')) def crawl(self, url=None):
if url == None:
url = self.target_url
href_links = self.extract_links_from(url)
for link in href_links:
link = urljoin(url, link) if "#" in link:
link = link.split("#")[0] if self.target_url in link and link not in self.target_links and link not in self.links_to_ignore:
self.target_links.append(link)
print(link)
self.crawl(link) def extract_forms(self, url):
response = self.session.get(url)
parsed_html = BeautifulSoup(response.content.decode(), features="lxml")
return parsed_html.findAll("form") def submit_form(self, form, value, url):
action = form.get("action")
post_url = urljoin(url, action)
method = form.get("method") inputs_list = form.findAll("input")
post_data = {}
for input in inputs_list:
input_name = input.get("name")
input_type = input.get("type")
input_value = input.get("value")
if input_type == "text":
input_value = value post_data[input_name] = input_value
if method == "post":
return requests.post(post_url, data=post_data)
return self.session.get(post_url, params=post_data) def run_scanner(self):
for link in self.target_links:
forms = self.extract_forms(link)
for form in forms:
print("[+] Testing form in " + link) if "=" in link:
print("[+] Testing " + link) def test_xss_in_form(self, form, url):
xss_test_script = "<sCript>alert('test')</scriPt>"
response = self.submit_form(form, xss_test_script, url)
if xss_test_script in response.content.decode():
return True
Modify the vulnerability scanner code and test it.
#!/usr/bin/env python import scanner target_url = "http://10.0.0.45/dvwa/"
links_to_ignore = "http://10.0.0.45/dvwa/logout.php" data_dict = {"username": "admin", "password": "password", "Login": "submit"} vuln_scanner = scanner.Scanner(target_url, links_to_ignore)
vuln_scanner.session.post("http://10.0.0.45/dvwa/login.php", data=data_dict) # vuln_scanner.crawl()
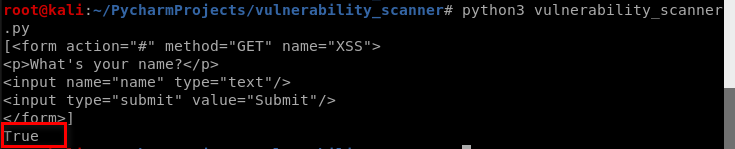
forms = vuln_scanner.extract_forms("http://10.0.0.45/dvwa/vulnerabilities/xss_r/")
print(forms)
response = vuln_scanner.test_xss_in_form(forms[0], "http://10.0.0.45/dvwa/vulnerabilities/xss_r/")
print(response)
Aha! We find customized vulnerability.
最新文章
- java线程(2016-4-7)
- 高级php面试题(转)
- unity渲染层级关系小结(转存)
- 常用SNS开源系统比较
- Android推送等耗电原因剖析
- static和extern关键字 对函数的作用
- COM模块三---根的形成和注册代理server(Building and Registering a Proxy DLL)
- linux devel包 和 非devel包的区别
- C++经典绘图工具EasyX
- 小T牛 绿色版 18.08.0100
- <API自动化测试>Centos-Newman
- tomcat启动dubbo报IO异常
- Android.mk(3) 宏
- dgraph 基本查询语法 三
- 如何用c#本地代码实现与Webbrowser中的JavaScript交互
- CMD命令操作符
- hdu 4403 爆搜
- EBS常用接口表
- LaTeX 的对参考文献的处理
- PowerDesigner 概念数据模型