Nikto
https://cirt.net/nikto2
Fire Up Kali & Open Nikto
Let's fire up Kali and get started with nikto. Once we have Kali up and running, go to Kali Linux -> Vulnerability Analysis -> Misc Scanners -> nikto, like in the screenshot below.
Image via wonderhowto.com
Although there are many options in using nikto, we will limit ourselves here to the basic syntax, such as this:
- nikto -h <IP or hostname>
Step 2Scan the Web Server
Let's start with a safe web server on our own network. In this case, I have started the http service on another machine on my network. There is not a website hosted by this machine, just the web server. Let's scan it for vulnerabilities by typing:
- nikto -h 192.168.1.104
Nikto responds with a lot of information, as you can see below.
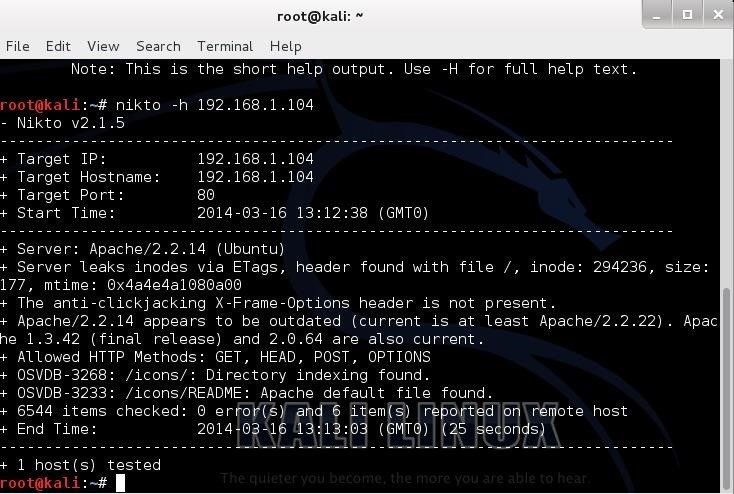
First, it tells us the server is Apache 2.2.14, probably on Ubuntu. It nailed this info and gives up more information on other potential vulnerabilities on this web server.
Note near the bottom that it identifies some vulnerabilities with the OSVDB prefix. This is the Open Source Vulnerability Database. This is a database maintained of known vulnerabilities at www.osvdb.org, in addition to other databases I covered, such as SecurityFocus and Microsoft's Technet.
Step 3Scan the Site
Let's try another site. In an earlier tutorial, we had hacked a web server named webscantest.com. Let's see what nikto can tell us about this site.
- nikto -h webscantest.com
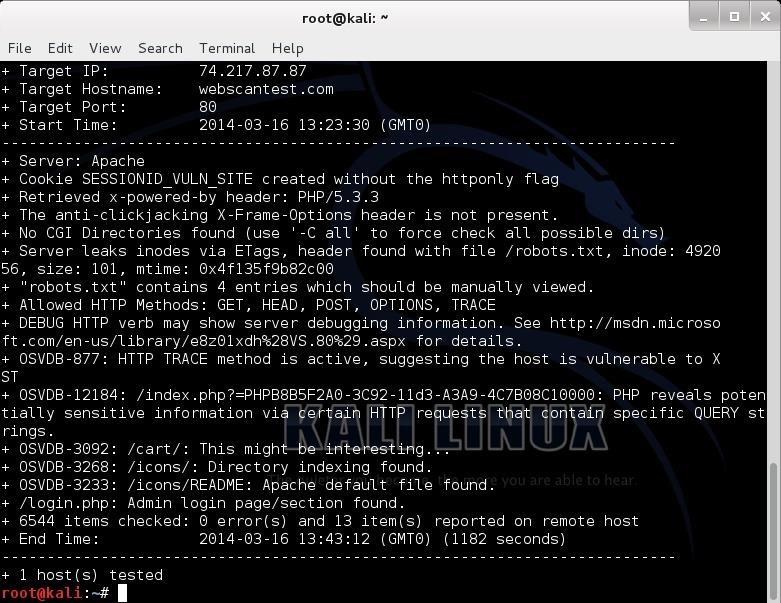
Once again, it identifies the server (Apache) and then proceeds to identify numerous potential vulnerabilities pre-fixed with OSVDB. We can take a look at that website at www.osvdb.org to learn more about these vulnerabilities.
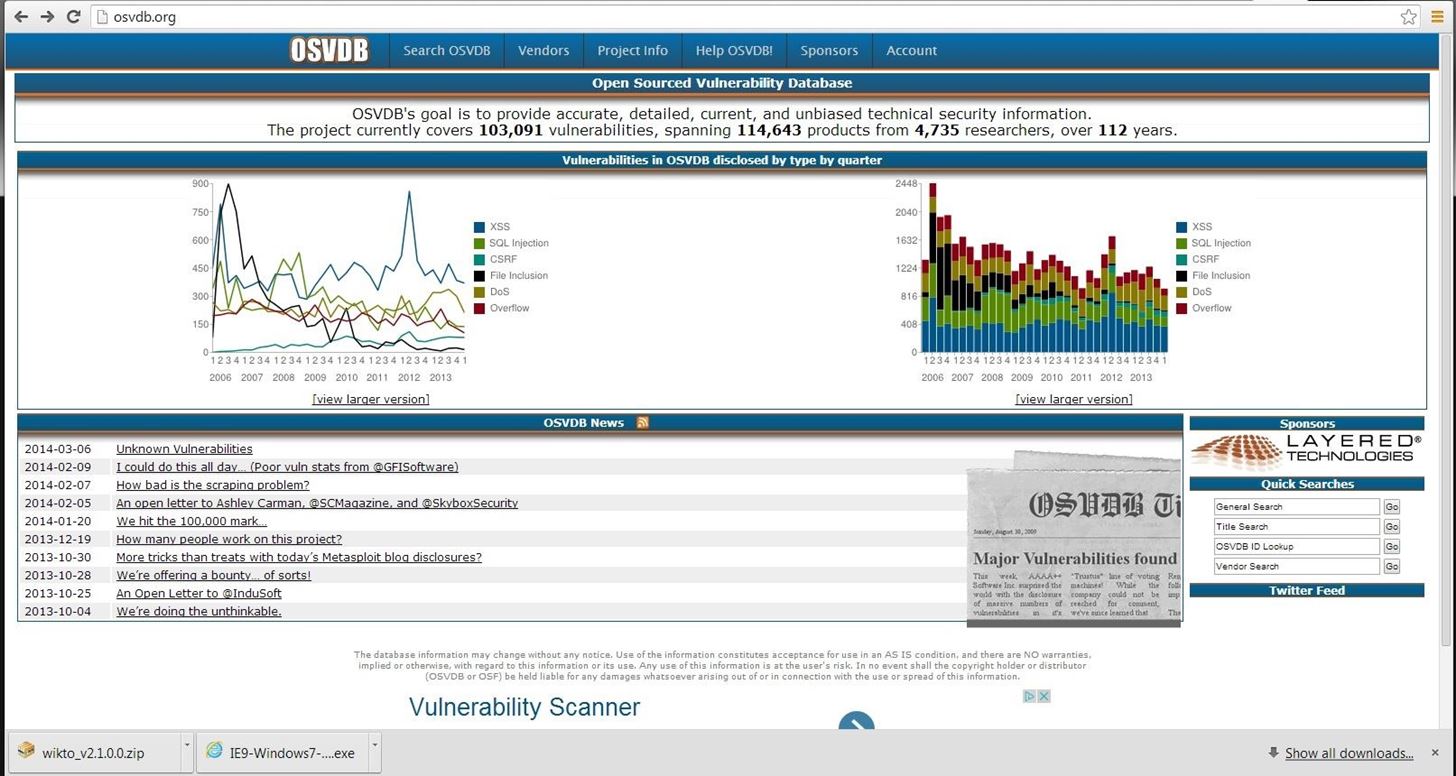
Now, let's use this site to find information on one of the vulnerabilities identified by nikto as OSVDB-877. We can put that reference number into the search function and it retrieves the following page.
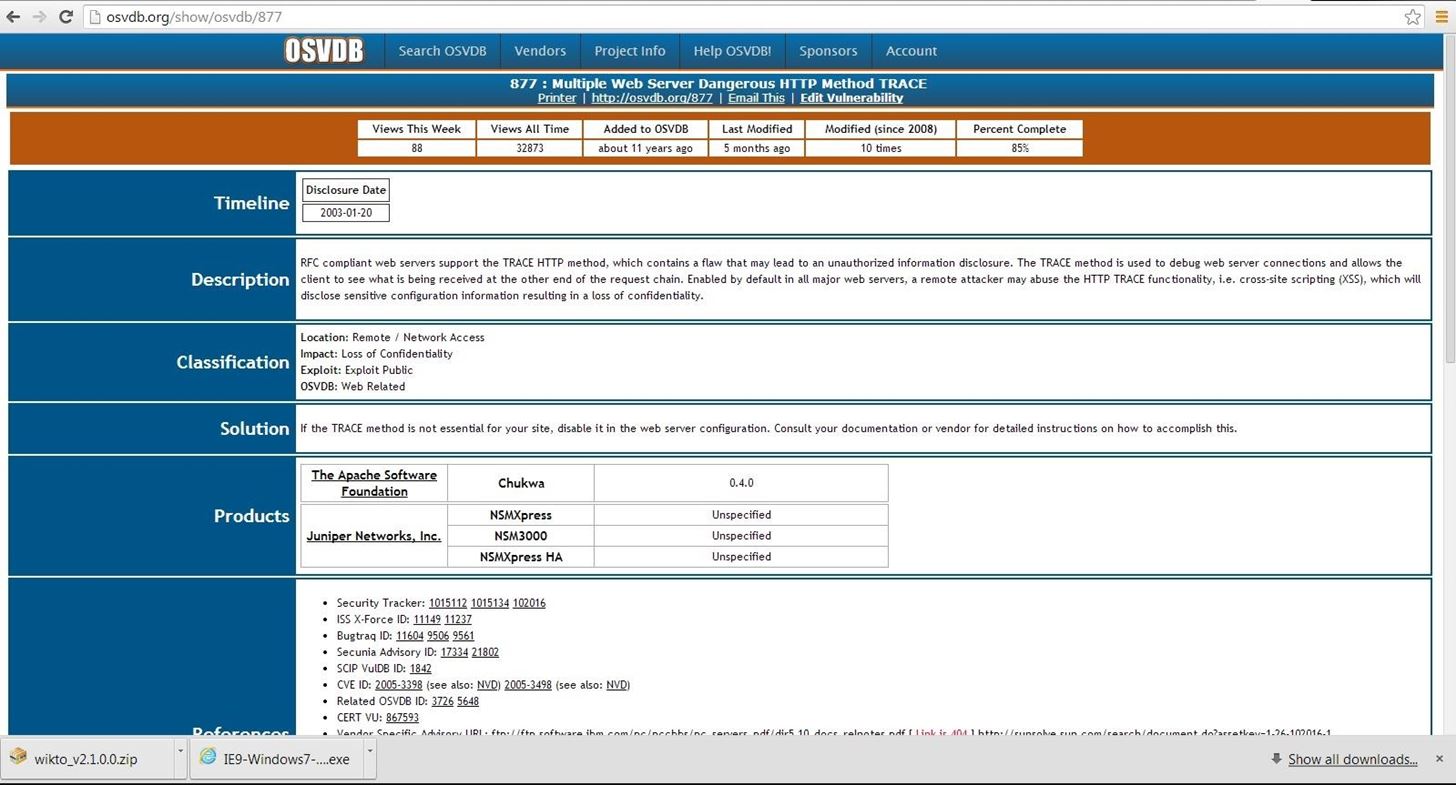
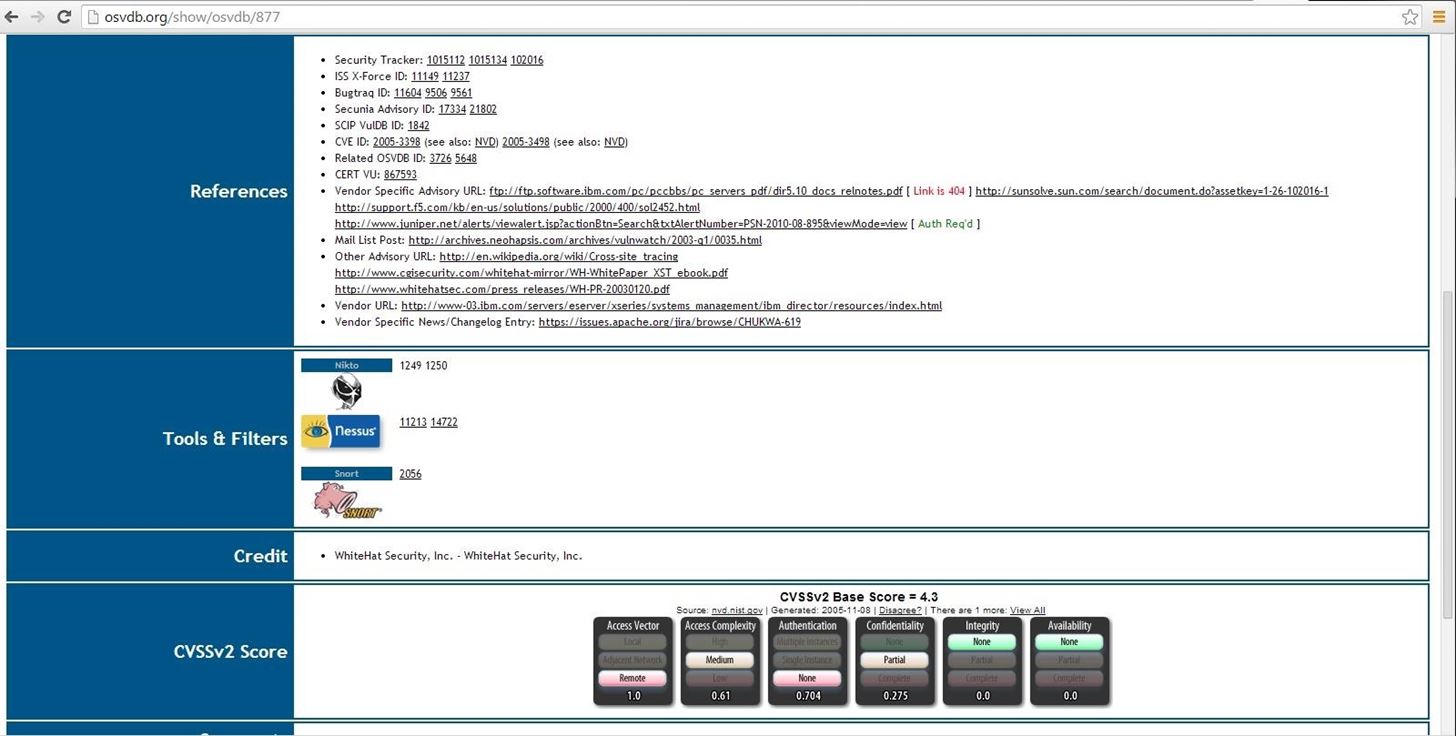
Note, in lower half of this page there are cross-references to the various information sources about this vulnerability, as well as references to tools and filters such as Nikto, Nessus, and Snort.
Scan WonderHowTo
Let's scan a few more sites and see what it can tell us about these sites. Let's see what we can find out about our own website, www.wonderhowto.com.
- nikto -h wonderhowto.com
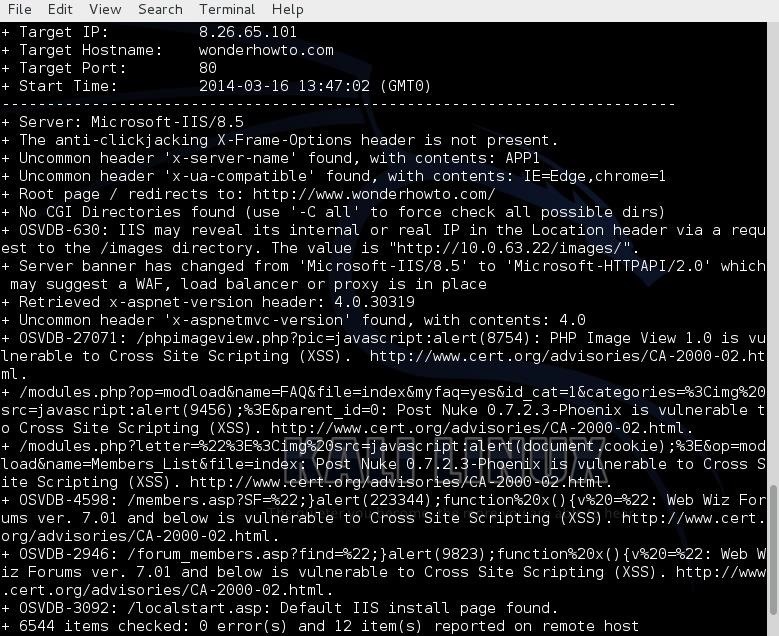
As you can see, it tells us that WonderHowTo is using Microsoft's IIS 8.5 as a web server and then lists numerous potential vulnerabilities.
However, any attempt to exploit the vulnerabilities listed will reveal that they're all false-positives, as WonderHowTo simply returns a harmless 404 page. This is because WonderHowTo is not built on php or asp as the noted exploits expect.
False positives like this can appear because the scan does not actually execute each of the possible vulnerabilities, but rather scans to see if the server responds without error to known exploitable URLs.
Scan Facebook
Finally, lets point nikto at www.facebook.com.
- nikto -h facebook.com

As you can see, Facebook is tightly secured with few vulnerabilities. As you can imagine, if Facebook weren't secure, every script-kiddie on the planet would be hacking it to see who his true love is chatting with online.
最新文章
- podfile The dependency `` is not used in any concrete target
- ZooKeeper之FastLeaderElection算法详解
- Golang(笔记) 顺序编程
- WCF自定义扩展,以实现aop!
- 2016年11月17日 星期四 --出埃及记 Exodus 20:8
- 【Qt】Qt之进程间通信(共享内存)【转】
- 修改linux文件/文件夹权限
- 关于 ioctl 的 FIONREAD 參数
- Loadrunner测试json接口
- Filter技术+职责链模式
- Hibernate一对一主键映射
- 通过jdbc完成单表的curd操作以及对JDBCUtils的封装
- 【dp】P1434 [SHOI2002]滑雪
- 876. Middle of the Linked List
- Web接口测试-HttpClient
- HanLP 配置与使用
- 在win8 App中,StorageFile比Path更好用
- Java实验报告(实验二)
- EXP无法导出空表的表结构解决办法
- php常量PHP_EOL