Lab 3-3
Execute the malware found in the file Lab03-03.exe while monitoring it using basic dynamic analysis tools in a safe environment.
Questions and Short Answers
What do you notice when monitoring this malware with Process Explorer?
A: The malware performs process replacement on svchost.exe.
Can you identify any live memory modifications?
A: Comparing the disk image of svchost.exe with its memory image shows that they are not the same. The memory image has strings such as practicalmalwareanalysis.log and [ENTER], but the disk image has neither.
What are the malware’s host-based indicators?
A: The malware creates the log file practicalmalwareanalysis.log.
What is the purpose of this program?
A: The program performs process replacement on svchost.exe to launch
a keylogger.
Detailed Analysis
For this lab, we begin by launching Process Explorer and procmon. When procmon starts, the events stream by quickly, so we use File -> Capture Events to toggle event capture on and off. (It’s best to keep event capture off until all dynamic analysis programs are started and you’re ready to execute the program.) We use Filter -> Filter to open the Filter dialog, and then ensure that only the default filters are enabled by clicking the Reset button.
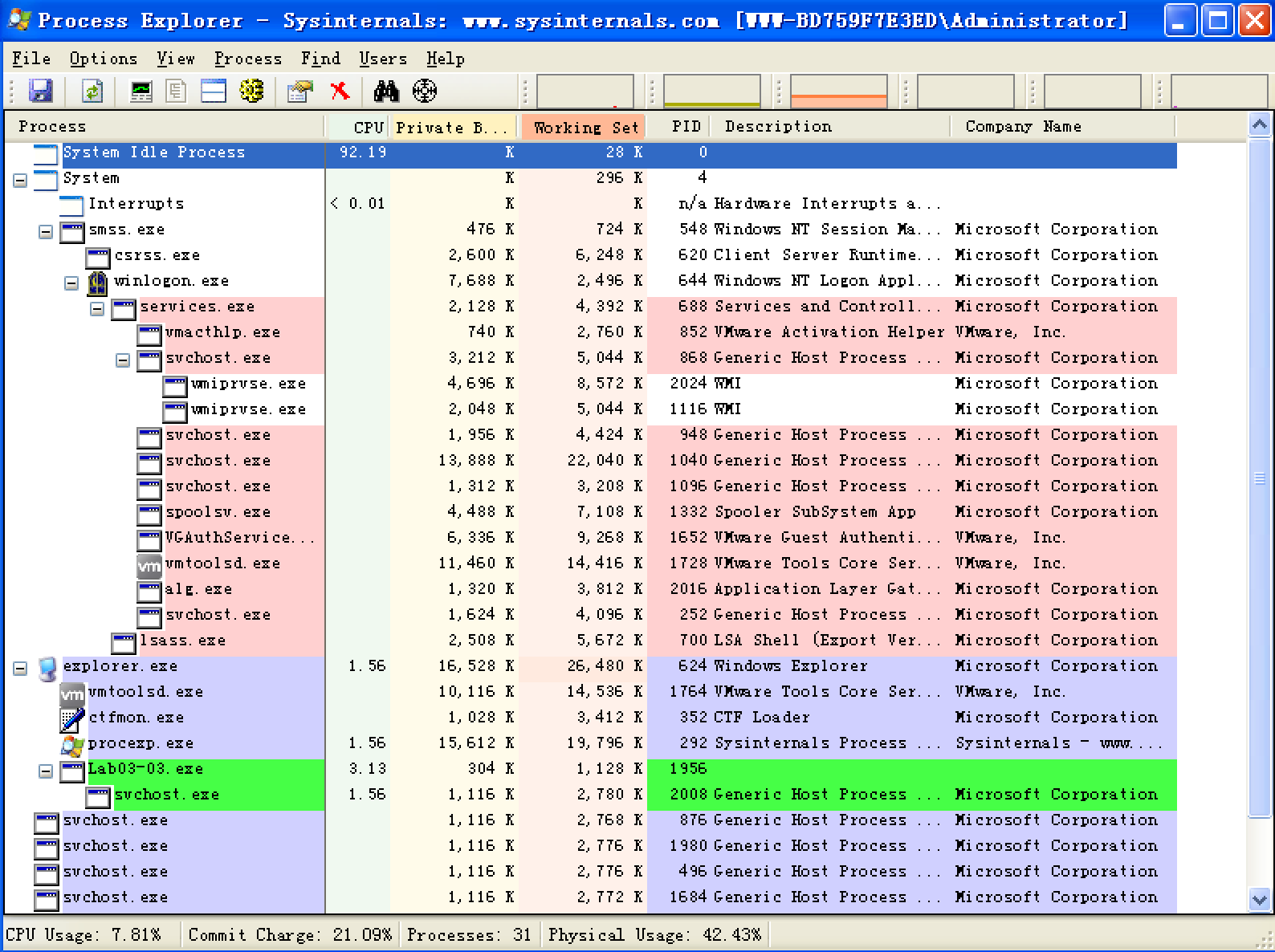
Lab03-03.exe can be run from the command prompt or by double-clicking its icon. Once run, Lab03-03.exe should be visible inside Process Explorer. Notice how it creates the subprocess svchost.exe, and then exits, but leaves the svchost.exe process running as an orphaned process, as shown in Figure 3-8L. (An orphaned process has no parent process listed in the process tree structure.) The fact that svchost.exe is orphaned is highly unusual and highly suspicious.
Process Explorer 在 Lab03-03.exe 运行前中后的状态如下图:

注:此图是我运行了很多遍,拼手速截的,故进程 PID 会有出入。
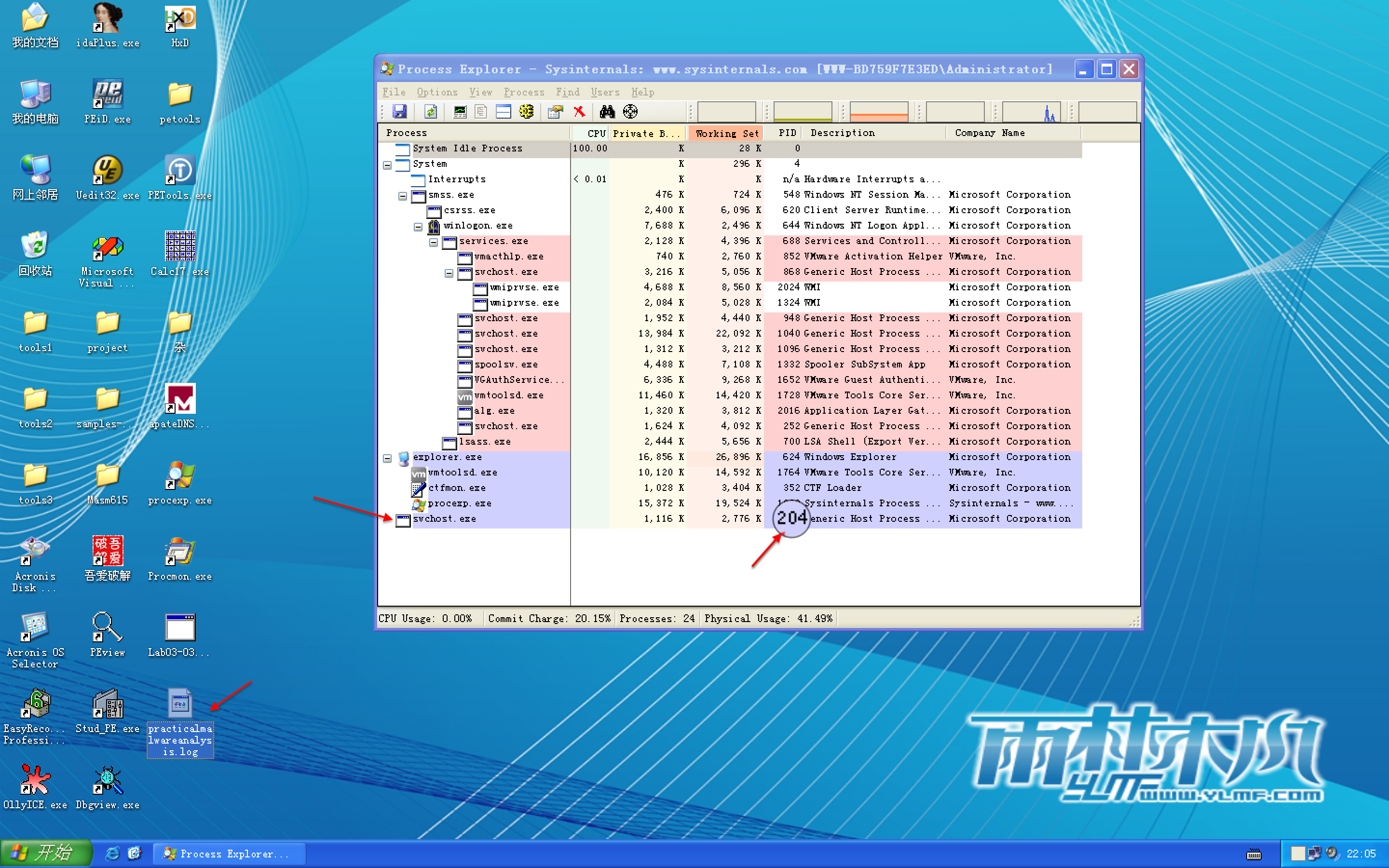
Figure 3-8L: Process Explorer view of orphaned svchost.exe

We investigate further by right-clicking and selecting Properties for the orphaned svchost.exe process. As shown in Figure 3-8L, the process appears to be a valid svchost.exe process with PID 204, but this svchost.exe is suspicious because svchost.exe is typically a child of services.exe.

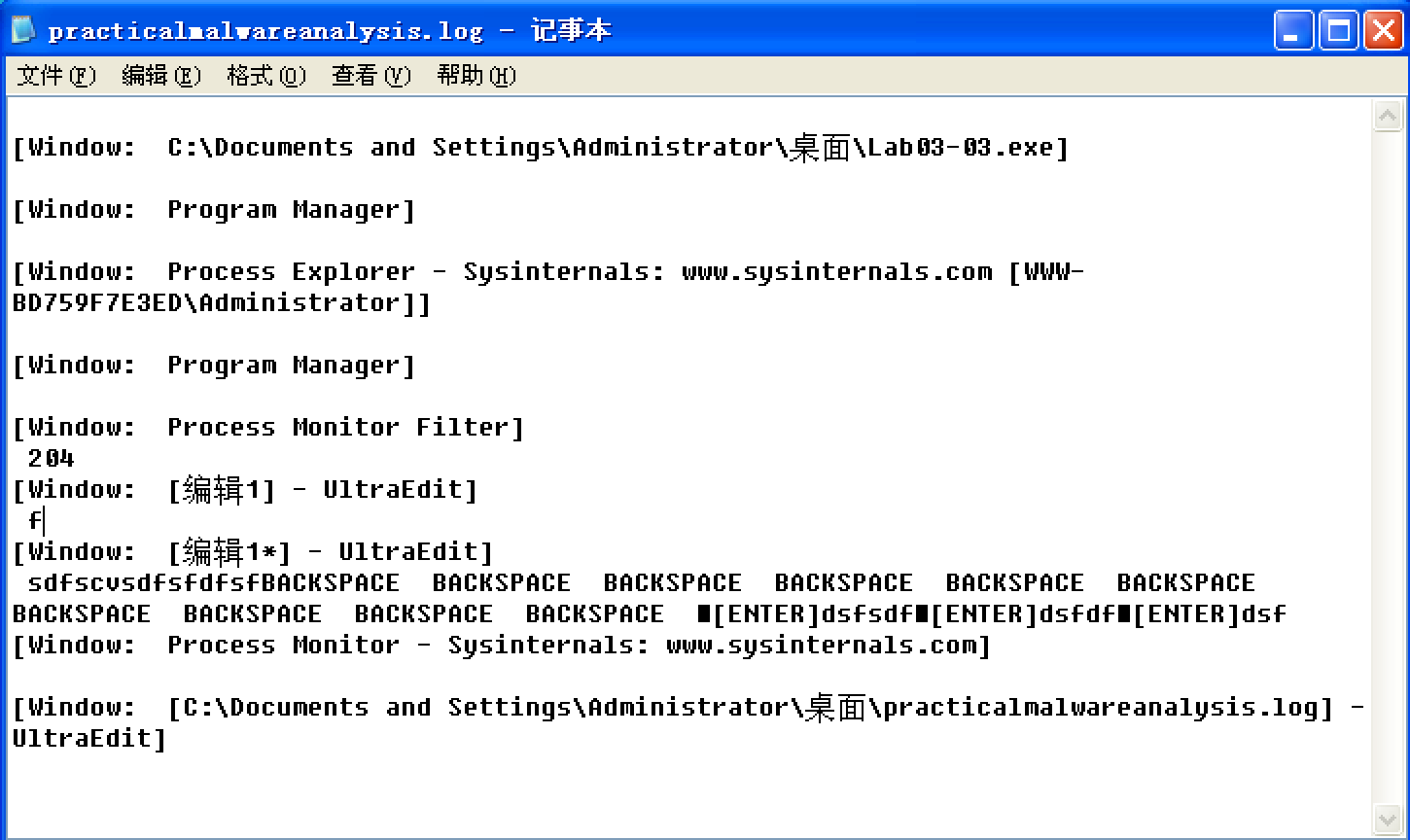
From this same properties page, we select Strings to show the strings in both the executable image on disk and in memory. Toggling between the Image and Memory radio buttons shows significant discrepancies between the images. As shown in Figure 3-9L, the strings in memory on the right contain practicalmalwareanalysis.log and [ENTER], seen at \({\color{red}1}\) and \({\color{red}2}\), neither of which is found in a typical Windows svchost.exe file on disk, as seen on the left.

Figure 3-9L: Process Explorer shows strings that are not normally contained in svchost.exe.
The presence of the string practicalmalwareanalysis.log, coupled with strings like [ENTER] and [CAPS LOCK], suggests that this program is a keylogger. To test our assumption, we open Notepad and type a short message to see if the malware will perform keylogging. To do so, we use the PID (found in Process Explorer) for the orphaned svchost.exe to create a filter in procmon to show only events from that PID (204). As you can see in Figure 3-10L, the CreateFile and WriteFile events for svchost.exe are writing to the file named practicalmalwareanalysis.log. (This same string is visible in the memory view of the orphaned svchost.exe process.)
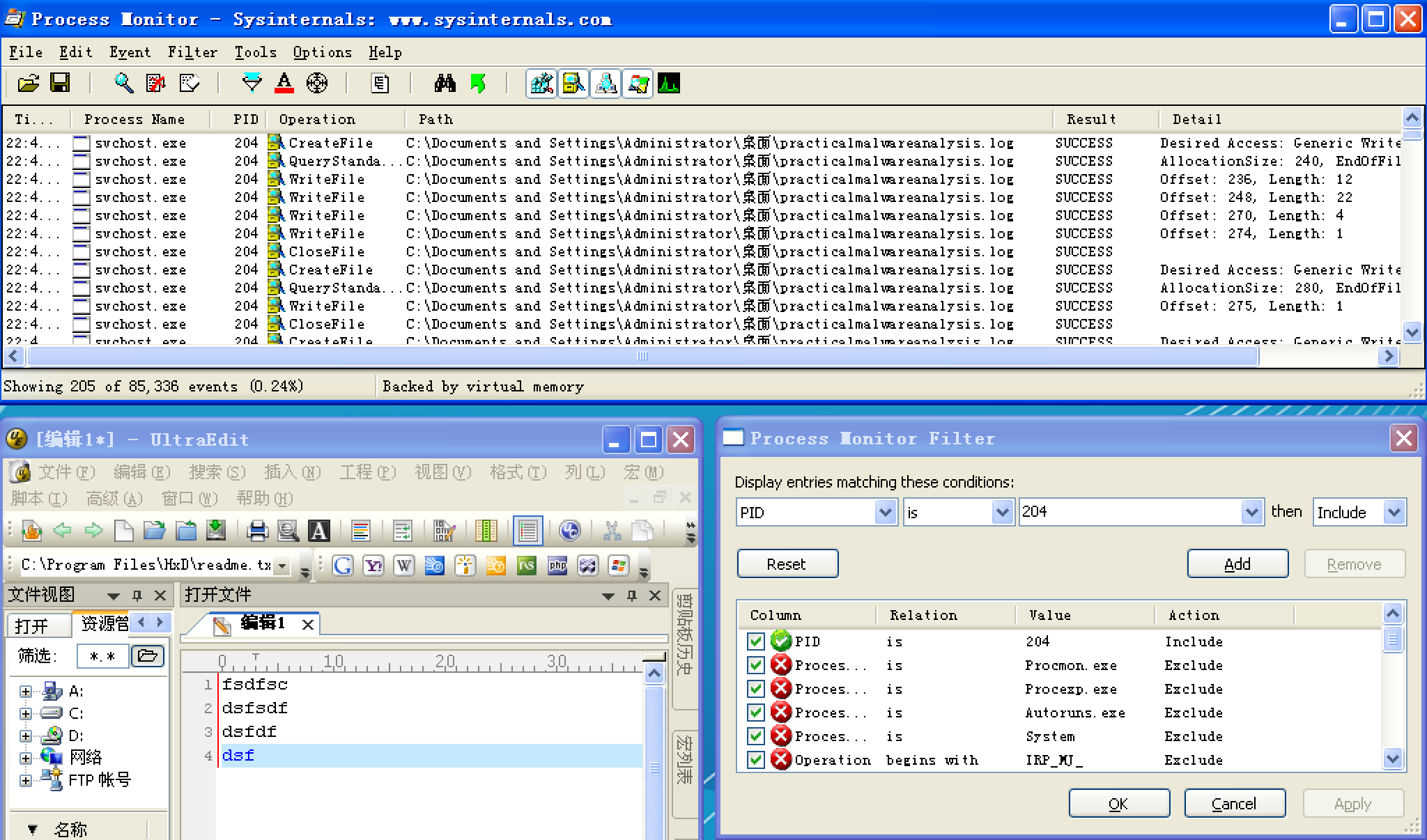
Figure 3-10L: Procmon output of svchost.exe with PID 204
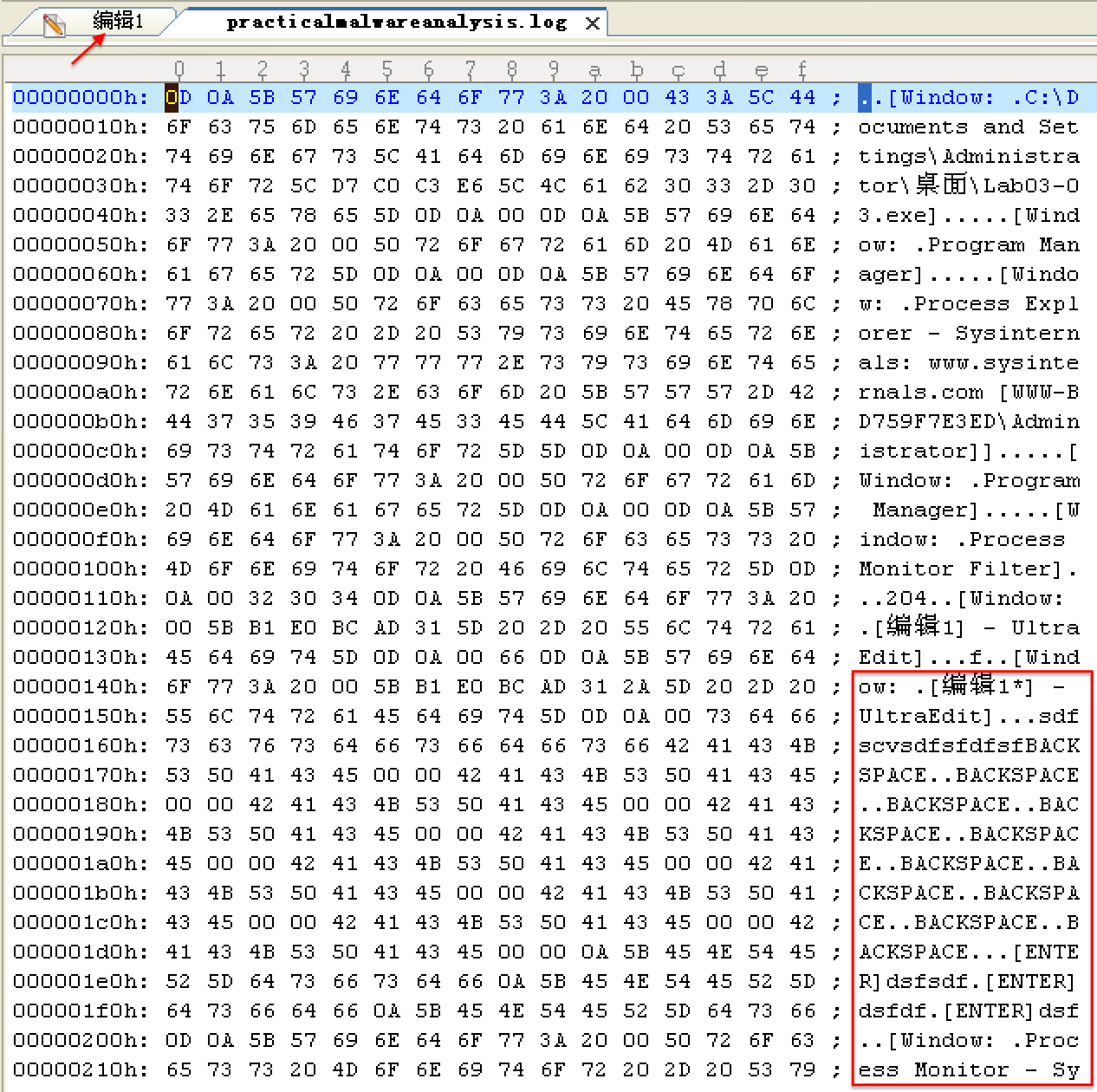
Opening practicalmalwareanalysis.log with a simple text editor reveals the keystrokes you entered in Notepad. We conclude that this malware is a keylogger that uses process replacement on svchost.exe.
Preference
最新文章
- 高仿淘宝和聚美优品商城详情页实现《IT蓝豹》
- ComponentOne 2016 年产品规划
- 软件项目发展历史<人月神话>这本书好
- Atom + activate-power-mode震屏插件Windows7下安装
- PHP 解决nginx 用file_get_content 问题
- 希赛网 > 问答 > 数据库 > MySQL数据库 > MySQL的管理与维护 > MySql开启远程用户登录GRANTALLPRIVILEGESON*.*TO'root'@'%'I MySql开启远程用户登录GRANTALLPRIVILEGESON*.*TO'root'@'%'I
- [转]安装openoffice,并且配置为windows服务
- phpize php扩展模块安装
- iPad和iPhone开发的比较
- ThinkPHP 3 的CURD管理用户信息 修改和删除
- HttpSesstionActivationLIstener示例
- “一切都是消息”--MSF(消息服务框架)之【发布-订阅】模式
- core dump文件的生成
- Echarts的一些总结
- bzoj3796(后缀数组)(SA四连)
- struts2框架之文件上传(参考第三天学习笔记)
- .NET BackgroundWorker的一般使用方式
- CSS做一个Switch开关
- MT【148】凸数列
- HTTP协议详解之响应篇
热门文章
- Python3基础 list reverse 反转列表
- Django组件(五) Django之ContentType组件
- shell编程(三)之条件判断(if语句)
- php的__autoload和php的__call
- ORM框架 之 Entity Framework
- P3605 [USACO17JAN]Promotion Counting晋升者计数
- Multi-attention Network for One Shot Learning
- js实现网站首页分享滑块
- React生命周期执行顺序详解
- Youtube-dl 配置 使用方法 + 配合aria2 多线程 下载 + 配合 ffmpeg 自动合并分段视频