centos7安装bind(DNS服务)
2024-08-31 23:32:00
环境介绍
公网IP:149.129.92.239
内网IP:172.17.56.249
系统:CentOS 7.4
一、安装
yum install bind bind-utils -y
二、修改bind配置文件
vim /etc/named.conf
options {
listen-on port 53 { any; }; #监听任何ip对53端口的请求
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
recursing-file "/var/named/data/named.recursing";
secroots-file "/var/named/data/named.secroots";
allow-query { any; }; #接收任何来源查询dns记录
/*
- If you are building an AUTHORITATIVE DNS server, do NOT enable recursion.
- If you are building a RECURSIVE (caching) DNS server, you need to enable
recursion.
- If your recursive DNS server has a public IP address, you MUST enable access
control to limit queries to your legitimate users. Failing to do so will
cause your server to become part of large scale DNS amplification
attacks. Implementing BCP38 within your network would greatly
reduce such attack surface
*/
recursion yes;
dnssec-enable yes;
dnssec-validation yes;
/* Path to ISC DLV key */
bindkeys-file "/etc/named.iscdlv.key";
managed-keys-directory "/var/named/dynamic";
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
zone "." IN {
type hint;
file "named.ca";
};
#增加一个a.com域名的解析,具体解析规则在/var/named/a.com.zone里
zone "a.com" IN {
type master;
file "a.com.zone";
};
#增加一个反向解析,即根据ip查域名(不需要的话可以不设置)
zone "56.17.172.in-addr.arpa" IN {
type master;
file "172.17.56.zone";
};
include "/etc/named.rfc1912.zones";
include "/etc/named.root.key";
三、配置解析文件
[root@izj6c1w3z30pendgik4p4vz ~]# cat /var/named/a.com.zone
$TTL 1D
@ IN SOA @ root.a.com. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS @
A 172.17.56.249 ;a.com的ip为172.17.56.249
www A 172.17.56.249 ;www.a.com的ip解析为172.17.56.249
@ MX 10 mx.a.com. ;a.com的mx记录为mx.a.com
AAAA ::1 [root@izj6c1w3z30pendgik4p4vz ~]# cat /var/named/172.17.56.zone
$TTL 86400
@ IN SOA localhost a.com. (
2014031101
2H
10M
7D
1D )
IN NS localhost.
249 IN PTR a.com ;172.17.56.249查询后得到的域名是a.com
249 IN PTR www.a.com. ;172.17.56.249查询后得到的域名是www.a.com
四、启动bind
systemctl start named
五、测试
1、修改dns配置/etc/resolv.conf
[root@izj6c1w3z30pendgik4p4vz ~]# cat /etc/resolv.conf
options timeout:2 attempts:3 rotate single-request-reopen
nameserver 172.17.56.249 2、解析测试
[root@izj6c1w3z30pendgik4p4vz ~]# ping a.com -c 2
PING a.com (172.17.56.249) 56(84) bytes of data.
64 bytes from a.com.56.17.172.in-addr.arpa (172.17.56.249): icmp_seq=1 ttl=64 time=0.016 ms
64 bytes from a.com.56.17.172.in-addr.arpa (172.17.56.249): icmp_seq=2 ttl=64 time=0.048 ms --- a.com ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1000ms
rtt min/avg/max/mdev = 0.016/0.032/0.048/0.016 ms
[root@izj6c1w3z30pendgik4p4vz ~]# ping www.a.com -c 2
PING www.a.com (172.17.56.249) 56(84) bytes of data.
64 bytes from www.a.com (172.17.56.249): icmp_seq=1 ttl=64 time=0.019 ms
64 bytes from www.a.com (172.17.56.249): icmp_seq=2 ttl=64 time=0.052 ms --- www.a.com ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 999ms
rtt min/avg/max/mdev = 0.019/0.035/0.052/0.017 ms
[root@izj6c1w3z30pendgik4p4vz ~]# nslookup a.com
Server: 172.17.56.249
Address: 172.17.56.249#53 Name: a.com
Address: 172.17.56.249 [root@izj6c1w3z30pendgik4p4vz ~]# dig www.a.com ; <<>> DiG 9.9.4-RedHat-9.9.4-73.el7_6 <<>> www.a.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 56816
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 3 ;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;www.a.com. IN A ;; ANSWER SECTION:
www.a.com. 86400 IN A 172.17.56.249 ;; AUTHORITY SECTION:
a.com. 86400 IN NS a.com. ;; ADDITIONAL SECTION:
a.com. 86400 IN A 172.17.56.249
a.com. 86400 IN AAAA ::1 ;; Query time: 0 msec
;; SERVER: 172.17.56.249#53(172.17.56.249)
;; WHEN: Wed Jun 05 09:58:34 CST 2019
;; MSG SIZE rcvd: 112
六、公网使用与测试
1、修改之前的文件与启动
[root@izj6c1w3z30pendgik4p4vz ~]# cat /etc/named.conf
#增加一个反向解析,即根据ip查域名(不需要的话可以不设置)
zone "92.129.149.in-addr.arpa" IN {
type master;
file "149.129.92.zone";
}; [root@izj6c1w3z30pendgik4p4vz ~]# cat /var/named/149.129.92.zone
$TTL 86400
@ IN SOA localhost a.com. (
2014031101
2H
10M
7D
1D )
IN NS localhost.
239 IN PTR a.com ;149.129.92.239查询后得到的域名是a.com
239 IN PTR www.a.com. ;149.129.92.239查询后得到的域名是www.a.com [root@izj6c1w3z30pendgik4p4vz ~]# cat /var/named/a.com.zone
$TTL 1D
@ IN SOA @ root.a.com. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS @
A 149.129.92.239
www A 149.129.92.239
@ MX 10 mx.a.com. ;a.com的mx记录为mx.a.com
AAAA ::1 #重启bind
systemctl restart named
2、防火墙开防53的udp端口对外
3、电脑或服务器更改dns
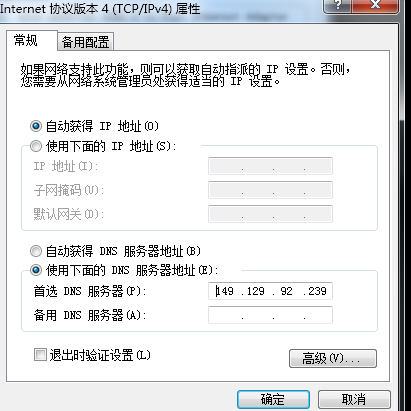
4、测试
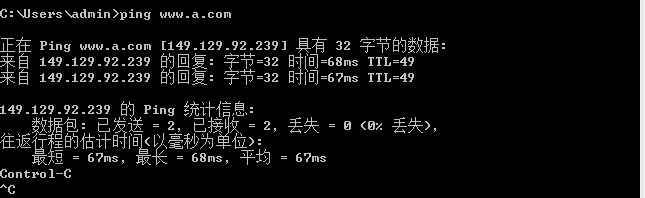
最新文章
- DUILIB入门使用说明整理
- Java的关键字与标识符
- Request 、Response 与Server的使用
- Atitit 常用比较复杂的图像滤镜 attilax大总结
- 10G整数文件中寻找中位数或者第K大数
- iOS7以上图片模糊效果
- HTTP 500.22 错误解决
- Aisen仿新浪微博客户端项目源码
- SQL Server用存储过程新建视图
- [CC150] Find a line passing the most number of points
- 解决 'utf-8' codec can't decode byte 0x8b in position 1: invalid start byte
- nginx 日志和监控
- BootKit病毒——“异鬼Ⅱ”的前世今生
- Linux IPC实践(12) --System V信号量(2)
- Java实现RSA密钥对并在加解密、加签验签中应用的实例
- UNIX网络编程(卷1)——学习过程中遇到的新词语
- mysql一张表多个字段关联另一张表查询
- java 实现Bridge模式(转)
- DevExpress如何实现皮肤的添加及本地化
- LVS+keepalived+nginx+tomcat部署实现